Difference between revisions of "Main Page/Featured article of the week/2021"
Shawndouglas (talk | contribs) (Added last week's article of the week) |
Shawndouglas (talk | contribs) (Ombox header) |
||
| (13 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{ombox | {{ombox | ||
| type = notice | | type = notice | ||
| text = If you're looking for other "Article of the Week" archives: [[Main Page/Featured article of the week/2014|2014]] - [[Main Page/Featured article of the week/2015|2015]] - [[Main Page/Featured article of the week/2016|2016]] - [[Main Page/Featured article of the week/2017|2017]] - [[Main Page/Featured article of the week/2018|2018]] - [[Main Page/Featured article of the week/2019|2019]] - [[Main Page/Featured article of the week/2020|2020]] - 2021 | | text = If you're looking for other "Article of the Week" archives: [[Main Page/Featured article of the week/2014|2014]] - [[Main Page/Featured article of the week/2015|2015]] - [[Main Page/Featured article of the week/2016|2016]] - [[Main Page/Featured article of the week/2017|2017]] - [[Main Page/Featured article of the week/2018|2018]] - [[Main Page/Featured article of the week/2019|2019]] - [[Main Page/Featured article of the week/2020|2020]] - 2021 - [[Main Page/Featured article of the week/2022|2022]] - [[Main Page/Featured article of the week/2023|2023]] - [[Main Page/Featured article of the week/2024|2024]] | ||
}} | }} | ||
| Line 17: | Line 17: | ||
<!-- Below this line begin pasting previous news --> | <!-- Below this line begin pasting previous news --> | ||
<h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: October 11–17:</h2> | <h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: December 27–January 2:</h2> | ||
'''"[[Journal:Towards a risk catalog for data management plans|Towards a risk catalog for data management plans]]"''' | |||
Although [[Information management|data management]] and its careful planning are not new topics, there is little published research on [[Risk management|risk mitigation]] in data management plans (DMPs). We consider it a problem that DMPs do not include a structured approach for the [[Risk assessment|identification]] or mitigation of risks, because it would instill confidence and trust in the data and its stewards, and foster the successful conduction of data-generating projects, which often are funded research projects. In this paper, we present a lightweight approach for identifying general risk in DMPs. We introduce an initial version of a generic risk catalog for funded research and similar projects. By analyzing a selection of 13 DMPs for projects from multiple disciplines published in the ''Research Ideas and Outcomes'' (''RIO'') journal, we demonstrate that our approach is applicable to DMPs and transferable to multiple institutional constellations. As a result, the effort for integrating risk management in data management planning can be reduced. ('''[[Journal:Towards a risk catalog for data management plans|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: December 20–26:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig1 Brandt DataSciJourn21 20-1.png|240px]]</div> | |||
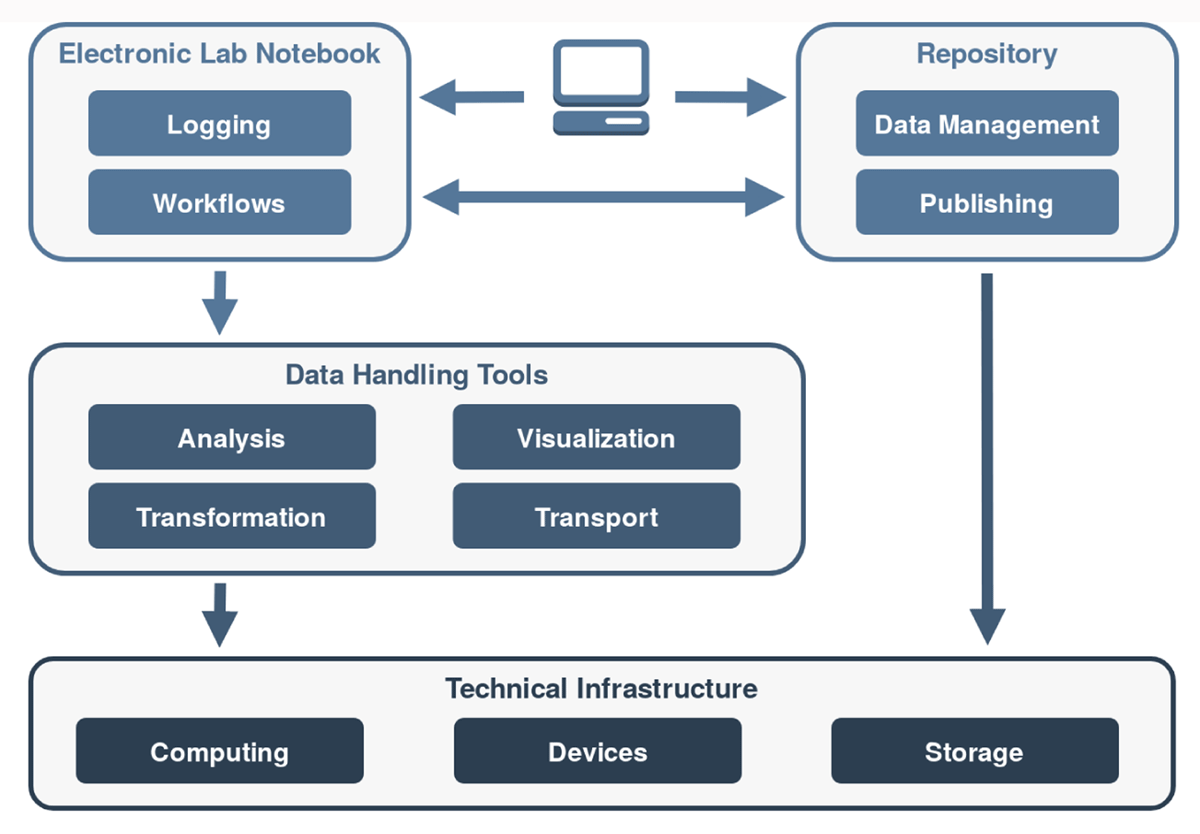
'''"[[Journal:Kadi4Mat: A research data infrastructure for materials science|Kadi4Mat: A research data infrastructure for materials science]]"''' | |||
The concepts and current developments of a research data infrastructure for [[Materials informatics|materials science]] are presented, extending and combining the features of an [[electronic laboratory notebook]] (ELN) and a repository. The objective of this infrastructure is to incorporate the possibility of structured data storage and data exchange with documented and reproducible [[data analysis]] and [[Data visualization|visualization]], which finally leads to the publication of the data. This way, researchers can be supported throughout the entire research process. The software is being developed as a web-based and desktop-based system, offering both a graphical user interface (GUI) and a programmatic interface. The focus of the development is on the integration of technologies and systems based on both established as well as new concepts. Due to the heterogeneous nature of materials science data, the current features are kept mostly generic, and the structuring of the data is largely left to the users. As a result, an extension of the research data infrastructure to other disciplines is possible in the future. The source code of the project is publicly available under a permissive Apache 2.0 license. ('''[[Journal:Kadi4Mat: A research data infrastructure for materials science|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: December 13–19:</h2> | |||
'''"[[Journal:Making data and workflows findable for machines|Making data and workflows findable for machines]]"''' | |||
[[Research]] data currently face a huge increase of data objects, with an increasing variety of types (data types, formats) and variety of [[workflow]]s by which objects need to be managed across their lifecycle by data infrastructures. Researchers desire to shorten the workflows from data generation to [[Data analysis|analysis]] and publication, and the full workflow needs to become transparent to multiple stakeholders, including research administrators and funders. This poses challenges for research infrastructures and user-oriented data services in terms of not only making data and workflows findable, accessible, interoperable, and reusable ([[Journal:The FAIR Guiding Principles for scientific data management and stewardship|FAIR]]), but also doing so in a way that leverages machine support for better efficiency. One primary need yet to be addressed is that of findability, and achieving better findability has benefits for other aspects of data and workflow management. In this article, we describe how machine capabilities can be extended to make workflows more findable, in particular by leveraging the Digital Object Architecture, common object operations, and [[machine learning]] techniques. ('''[[Journal:Making data and workflows findable for machines|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: December 6–12:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig1 Cassim AfricanJLabMed2020 9-2.jpg|240px]]</div> | |||
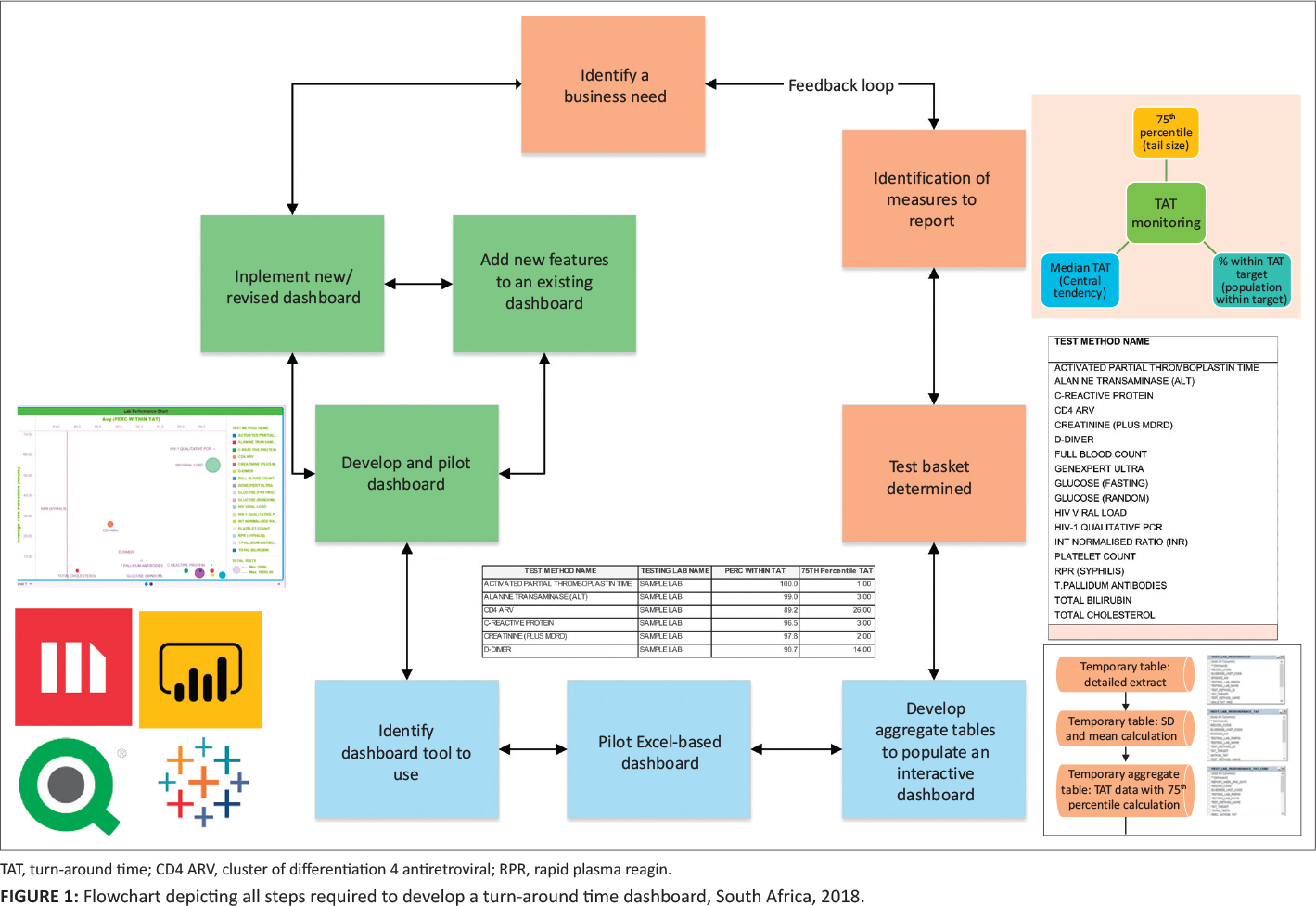
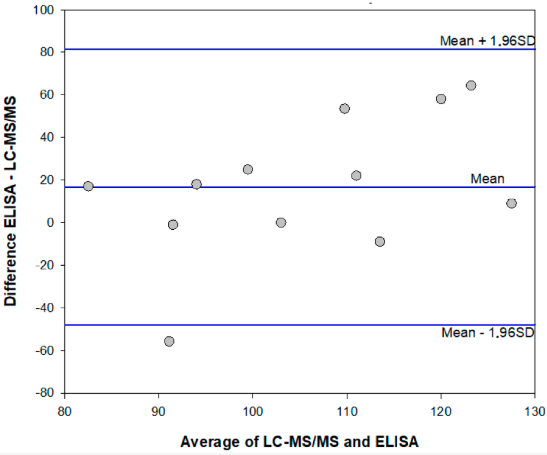
'''"[[Journal:Timely delivery of laboratory efficiency information, Part I: Developing an interactive turnaround time dashboard at a high-volume laboratory|Timely delivery of laboratory efficiency information, Part I: Developing an interactive turnaround time dashboard at a high-volume laboratory]]"''' | |||
Mean [[wikipedia:Turnaround time|turnaround time]] (TAT) [[reporting]] for testing [[Laboratory|laboratories]] in a national network is typically static and not immediately available for meaningful corrective action and does not allow for test-by-test or site-by-site interrogation of individual laboratory performance. The aim of this study was to develop an easy-to-use, visual dashboard to report interactive graphical TAT data to provide a weekly snapshot of TAT efficiency. An interactive dashboard was developed by staff from the National Priority Programme and Central Data Warehouse of the National Health Laboratory Service in Johannesburg, South Africa, during 2018. Steps required to develop the dashboard were summarized in a flowchart. To illustrate the dashboard, one week of data from a busy laboratory for a specific set of tests was analyzed using annual performance plan TAT cutoffs. Data were extracted and prepared to deliver an aggregate extract, with statistical measures provided, including test volumes, global percentage of tests that were within TAT cutoffs, and percentile statistics. ('''[[Journal:Timely delivery of laboratory efficiency information, Part I: Developing an interactive turnaround time dashboard at a high-volume laboratory|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: November 29–December 5:</h2> | |||
'''"[[Journal:Advanced engineering informatics: Philosophical and methodological foundations with examples from civil and construction engineering|Advanced engineering informatics: Philosophical and methodological foundations with examples from civil and construction engineering]]"''' | |||
We argue that the representation and formalization of complex engineering knowledge is the main aim of inquiries in the scientific field of [[Wikipedia:Engineering informatics|advanced engineering informatics]]. We introduce [[Ontology (information science)|ontology]] and logic as underlying methods to formalize [[Information#As an influence which leads to a transformation|knowledge]]. We also suggest that it is important to account for the purpose of engineers and the context they work in while representing and formalizing knowledge. Based on the concepts of ontology, logic, purpose, and context, we discuss different possible research methods and approaches that scholars can use to formalize complex engineering knowledge and to validate whether a specific formalization can support engineers with their complex tasks. On the grounds of this discussion, we suggest that research efforts in advanced engineering should be conducted in a bottom-up manner, closely involving engineering practitioners. We also suggest that researchers make use of social science methods while both eliciting knowledge to formalize and validating that formalized knowledge. ('''[[Journal:Advanced engineering informatics: Philosophical and methodological foundations with examples from civil and construction engineering|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: November 22–28:</h2> | |||
'''"[[Journal:Explainability for artificial intelligence in healthcare: A multidisciplinary perspective|Explainability for artificial intelligence in healthcare: A multidisciplinary perspective]]"''' | |||
Explainability is one of the most heavily debated topics when it comes to the application of [[artificial intelligence]] (AI) in healthcare. Even though AI-driven systems have been shown to outperform humans in certain analytical tasks, the lack of explainability continues to spark criticism. Yet, explainability is not a purely technological issue; instead, it invokes a host of medical, legal, ethical, and societal questions that require thorough exploration. This paper provides a comprehensive assessment of the role of explainability in medical AI and makes an ethical evaluation of what explainability means for the adoption of AI-driven tools into clinical practice. Taking AI-based [[clinical decision support system]]s as a case in point, we adopted a multidisciplinary approach to analyze the relevance of explainability for medical AI from the technological, legal, medical, and patient perspectives. Drawing on the findings of this conceptual analysis, we then conducted an ethical assessment using Beauchamp and Childress' ''Principles of Biomedical Ethics'' (autonomy, beneficence, nonmaleficence, and justice) as an analytical framework to determine the need for explainability in medical AI. ('''[[Journal:Explainability for artificial intelligence in healthcare: A multidisciplinary perspective|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: November 15–21:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig9 Brown JMIRMedInfo2020 8-9.png|240px]]</div> | |||
'''"[[Journal:Secure record linkage of large health data sets: Evaluation of a hybrid cloud model|Secure record linkage of large health data sets: Evaluation of a hybrid cloud model]]"''' | |||
The [[Linked data|linking]] of administrative data across agencies provides the capability to investigate many health and social issues, with the potential to deliver significant public benefit. Despite its advantages, the use of [[cloud computing]] resources for linkage purposes is scarce, with the storage of identifiable [[information]] on cloud infrastructure assessed as high-risk by data custodians. This study aims to present a model for record linkage that utilizes cloud computing capabilities while assuring custodians that identifiable data sets remain secure and local. A new hybrid cloud model was developed, including [[Information privacy|privacy-preserving]] record linkage techniques and container-based batch processing. An evaluation of this model was conducted with a prototype implementation using large synthetic data sets representative of administrative health data. ('''[[Journal:Secure record linkage of large health data sets: Evaluation of a hybrid cloud model|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: November 8–14:</h2> | |||
'''"[[Journal:Risk assessment for scientific data|Risk assessment for scientific data]]"''' | |||
Ongoing stewardship is required to keep data collections and archives in existence. Scientific data collections may face a range of risk factors that could hinder, constrain, or limit current or future data use. Identifying such risk factors to data use is a key step in preventing or minimizing data loss. This paper presents an analysis of data risk factors that scientific data collections may face, and a data risk assessment matrix to support data risk assessments to help ameliorate those risks. The goals of this work are to inform and enable effective data risk assessment by: a) individuals and organizations who manage data collections, and b) individuals and organizations who want to help to reduce the risks associated with data preservation and stewardship. The data risk assessment framework presented in this paper provides a platform from which risk assessments can begin, and a reference point for discussions of data stewardship resource allocations and priorities. ('''[[Journal:Risk assessment for scientific data|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: November 1–7:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Lazarjani BMCJournCannaRes2020 2.png|240px]]</div> | |||
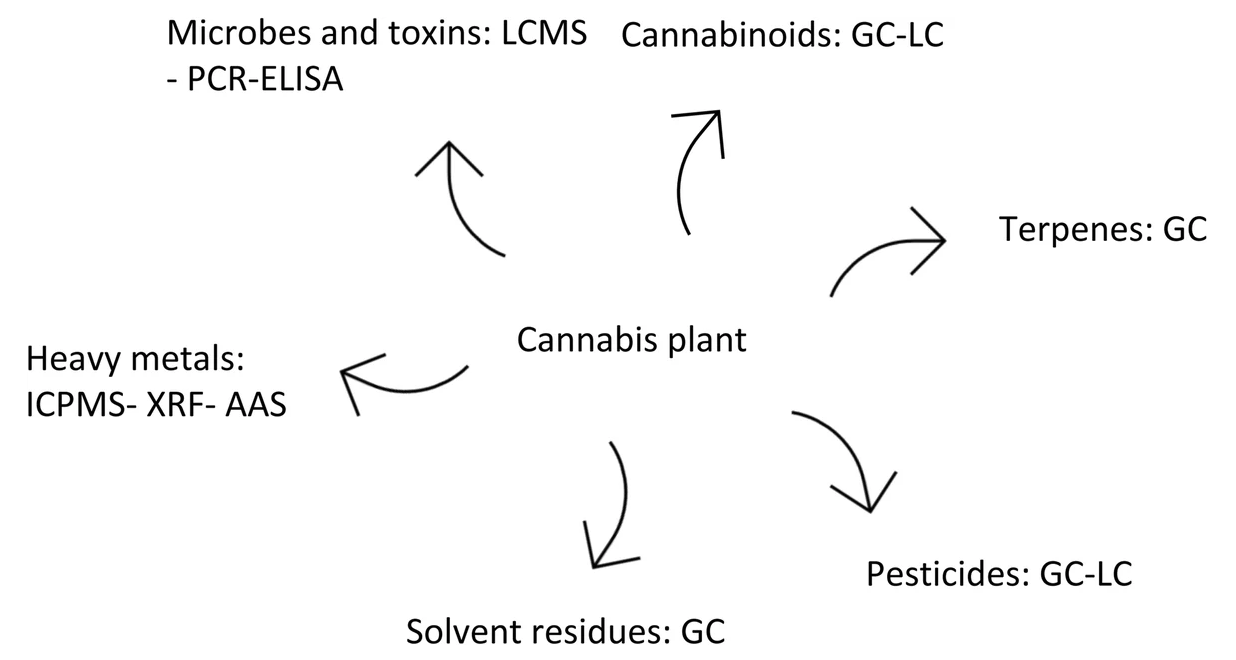
'''"[[Journal:Methods for quantification of cannabinoids: A narrative review|Methods for quantification of cannabinoids: A narrative review]]"''' | |||
Around 144 [[Wikipedia:Cannabinoid|cannabinoids]] have been identified in the ''[[Wikipedia:Cannabis|Cannabis]]'' plant; among them [[Wikipedia:Tetrahydrocannabinol|tetrahydrocannabinol]] (THC) and [[Wikipedia:Cannabidiol|cannabidiol]] (CBD) are the most prominent ones. Because of the legal restrictions on cannabis in many countries, it is difficult to obtain standards to use in research; nonetheless, it is important to develop a cannabinoid quantification technique, with practical pharmaceutical applications for quality control of future therapeutic cannabinoids. To find relevant articles for this narrative review paper, a combination of keywords such as "[[Wikipedia:Cannabis (drug)|medicinal cannabis]]," "analytical," "quantification," and "cannabinoids" were searched for in PubMed, EMBASE, MEDLINE, Google Scholar, and Cochrane Library (Wiley) databases. ('''[[Journal:Methods for quantification of cannabinoids: A narrative review|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: October 25–31:</h2> | |||
'''"[[Journal:Utilizing connectivity and data management systems for effective quality management and regulatory compliance in point-of-care testing|Utilizing connectivity and data management systems for effective quality management and regulatory compliance in point-of-care testing]]"''' | |||
Point-of-care testing (POCT) is one of the fastest growing disciplines in [[clinical laboratory]] medicine. POCT [[Medical device|devices]] are widely used in both acute and chronic patient management in the [[hospital]] and [[Physician office laboratory|primary care physician office]] settings. As demands for POCT in various healthcare settings increase, managing POCT testing quality and [[regulatory compliance]] are continually challenging. Despite technological advances in applying automatic system checks and built-in [[quality control]] to prevent analytical and operator errors, poor planning for POCT [[Interface (computing)|connectivity]] and [[Informatics (academic field)|informatics]] can limit [[Data sharing|data accessibility]] and [[Information management|management]] efficiency which impedes the utilization of POCT to its full potential. This article will summarize how connectivity and data management systems can improve timely access to POCT results, effective management of POCT programs, and ensure regulatory compliance. ('''[[Journal:Utilizing connectivity and data management systems for effective quality management and regulatory compliance in point-of-care testing|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: October 18–24:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Schmidt BMCMedInfoDecMak2020 20.png|240px]]</div> | |||
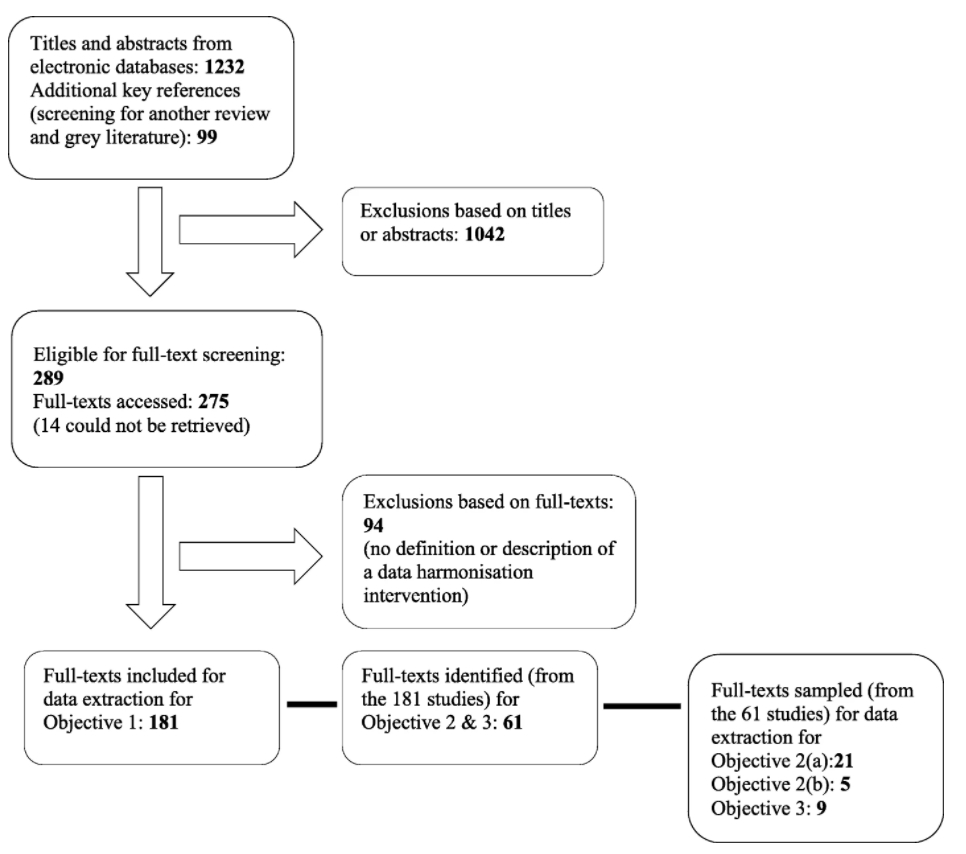
'''"[[Journal:Definitions, components and processes of data harmonization in healthcare: A scoping review|Definitions, components and processes of data harmonization in healthcare: A scoping review]]"''' | |||
[[Data cleansing|Data harmonization]] (DH) has is increasingly being used by health managers, information technology specialists, and researchers as an important intervention for [[Health information technology|routine health information systems]] (RHISs). It is important to understand what DH is, how it is defined and conceptualized, and how it can lead to better health management decision-making. This scoping review identifies a range of definitions for DH, its characteristics (in terms of key components and processes), and common explanations of the relationship between DH and health management decision-making. This scoping review identified more than 2,000 relevant studies (date filter) written in English and published in PubMed, Web of Science, and CINAHL. ('''[[Journal:Definitions, components and processes of data harmonization in healthcare: A scoping review|Full article...]]''')<br /> | |||
<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: October 11–17:</h2> | |||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Rantos Computers2020 9-1.png|240px]]</div> | <div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Rantos Computers2020 9-1.png|240px]]</div> | ||
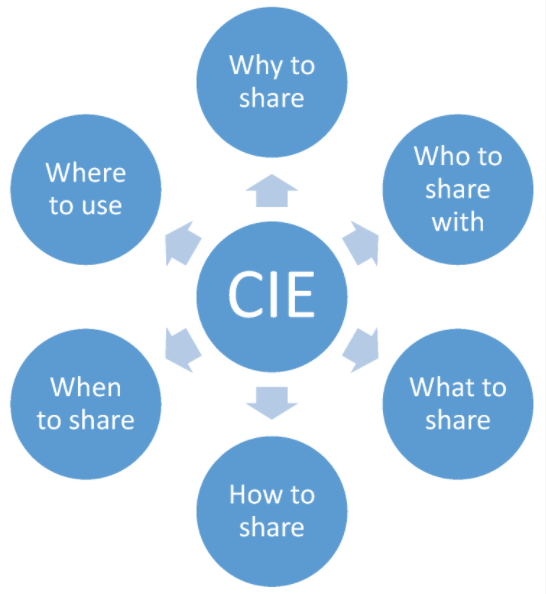
'''"[[Journal:Interoperability challenges in the cybersecurity information sharing ecosystem|Interoperability challenges in the cybersecurity information sharing ecosystem]]"''' | '''"[[Journal:Interoperability challenges in the cybersecurity information sharing ecosystem|Interoperability challenges in the cybersecurity information sharing ecosystem]]"''' | ||
Threat intelligence helps businesses and organizations make the right decisions in their fight against cyber threats, and strategically design their digital defenses for an optimized and up-to-date security situation. Combined with advanced security analysis, threat intelligence helps reduce the time between the detection of an attack and its containment. This is achieved by continuously providing [[information]], accompanied by data, on existing and emerging cyber threats and vulnerabilities affecting corporate networks. This paper addresses challenges that organizations are bound to face when they decide to invest in effective and interoperable [[cybersecurity]] information sharing, and it categorizes them in a layered model. Based on this, it provides an evaluation of existing sources that share cybersecurity information. The aim of this research is to help organizations improve their cyber threat information exchange capabilities, to enhance their security posture and be more prepared against emerging threats. ('''[[Journal:Interoperability challenges in the cybersecurity information sharing ecosystem|Full article...]]''')<br /> | Threat intelligence helps businesses and organizations make the right decisions in their fight against cyber threats, and strategically design their digital defenses for an optimized and up-to-date security situation. Combined with advanced security analysis, threat intelligence helps reduce the time between the detection of an attack and its containment. This is achieved by continuously providing [[information]], accompanied by data, on existing and emerging cyber threats and vulnerabilities affecting corporate networks. This paper addresses challenges that organizations are bound to face when they decide to invest in effective and interoperable [[cybersecurity]] information sharing, and it categorizes them in a layered model. Based on this, it provides an evaluation of existing sources that share cybersecurity information. The aim of this research is to help organizations improve their cyber threat information exchange capabilities, to enhance their security posture and be more prepared against emerging threats. ('''[[Journal:Interoperability challenges in the cybersecurity information sharing ecosystem|Full article...]]''')<br /> | ||
<br /> | <br /> | ||
|- | |- | ||
Latest revision as of 15:34, 2 January 2024
|
|
If you're looking for other "Article of the Week" archives: 2014 - 2015 - 2016 - 2017 - 2018 - 2019 - 2020 - 2021 - 2022 - 2023 - 2024 |
Featured article of the week archive - 2021
Welcome to the LIMSwiki 2021 archive for the Featured Article of the Week.
Featured article of the week: December 27–January 2:"Towards a risk catalog for data management plans" Although data management and its careful planning are not new topics, there is little published research on risk mitigation in data management plans (DMPs). We consider it a problem that DMPs do not include a structured approach for the identification or mitigation of risks, because it would instill confidence and trust in the data and its stewards, and foster the successful conduction of data-generating projects, which often are funded research projects. In this paper, we present a lightweight approach for identifying general risk in DMPs. We introduce an initial version of a generic risk catalog for funded research and similar projects. By analyzing a selection of 13 DMPs for projects from multiple disciplines published in the Research Ideas and Outcomes (RIO) journal, we demonstrate that our approach is applicable to DMPs and transferable to multiple institutional constellations. As a result, the effort for integrating risk management in data management planning can be reduced. (Full article...)
|