Difference between revisions of "User:Shawndouglas/sandbox/sublevel1"
Shawndouglas (talk | contribs) (Replaced content with "==Citation information for this chapter== '''Chapter''': 1. What is cloud computing? '''Title''': ''Choosing and Implementing a Cloud-based Service for Your Laboratory''...") Tag: Replaced |
Shawndouglas (talk | contribs) |
||
| Line 1: | Line 1: | ||
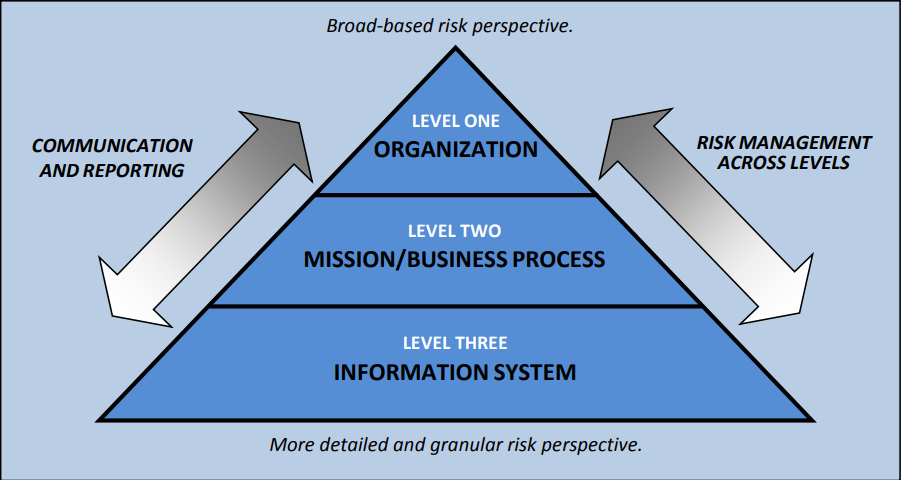
[[File:NISTRiskManApproach.png|right|450px|thumb|'''Figure 4.''' A diagram of an organization-wide risk management approach, as published in NIST SP 800-37 Rev. 2. NIST says this diagram "addresses security and privacy risk at the organization level, the mission/business process level, and the information system level. Communication and reporting are bi-directional information flows across the three levels to ensure that risk is addressed throughout the organization."<ref name="NISTSP800-37v2_18" />]]After discussing cloud standards, regulations, and security, it makes sense to next address the topic of [[cloud computing]] [[risk management]]. Risks beget risk management, which in turn begets security. Whether the risks are near the home, on an airplane, or with an online bank account, risk management practices limit the risks, usually through some "security." "The five-year crime numbers in my neighborhood are going up," one might assess. "I shall manage the risk with a home security system," is the risk management action performed. In the same way, engineers add multiple layers of redundancy to an airplane's components to mitigate the assessed risk of instrument failure, and banks require access controls like strong passwords on online accounts to protect customer data and limit their liability. As such, it shouldn't be surprising to talk about employing security and process control measures as part of managing risks in the cloud. | |||
''' | |||
'' | We learned in the last chapter that the National Institute of Standards and Technology (NIST) represents a strong example of a standards and recommendations body in the U.S. In their 2018 SP 800-37 Rev. 2 ''Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy'', NIST says the following about risk management for information systems<ref name="NISTSP800-37v2_18">{{cite web |url=https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final |title=SP 800-37 Rev. 2: Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy |author=National Institute of Standards and Technology |date=December 2018 |accessdate=21 August 2021}}</ref>: | ||
<blockquote>Managing information system-related security and privacy risk is a complex undertaking that requires the involvement of the entire organization—from senior leaders providing the strategic vision and top-level goals and objectives for the organization, to mid-level leaders planning, executing, and managing projects, to individuals developing, implementing, operating, and maintaining the systems supporting the organization’s missions and business functions. Risk management is a holistic activity that affects every aspect of the organization, including the mission and business planning activities, the enterprise architecture, the SDLC processes, and the systems engineering activities that are integral to those system life cycle processes.</blockquote> | |||
As Figure 4—from the same NIST guide—notes, there are three main levels at which an organization must approach risk management activities for their information systems: the organization level, the mission/business process level, and the information system level. The arrow on the left highlights the criticality of proper communication across all three levels in order for the organization to make the most of their risk management activities. Just as IT forms the base of any software-driven business efforts, critical stakeholders in IT form the base of communication about IT risk and security requirements. Without those stakeholders' knowledge and feedback, business processes and company policy would be ill-informed. Now let's start from the top of the pyramid and head downward. Note that without strong leadership, well-crafted business goals, and management buy-in on quality, budget, and security, business processes would be a mess and IT-related efforts would be sub-par and at-risk. | |||
''' | The implication with Figure 4 and NIST's guide is that effective planning and communication is critical to ensuring information systems are implemented securely during their entire life cycle. Many organizations approach this task by developing, implementing, and enforcing a [[cybersecurity]] plan, in which identifying cybersecurity requirements and objectives—i.e., [[risk assessment]] and management—is a vital component. (See the ''[[LII:Comprehensive Guide to Developing and Implementing a Cybersecurity Plan|Comprehensive Guide to Developing and Implementing a Cybersecurity Plan]]'' for much more on this topic.) | ||
==References== | |||
{{Reflist|colwidth=30em}} | |||
Revision as of 23:13, 3 February 2022
After discussing cloud standards, regulations, and security, it makes sense to next address the topic of cloud computing risk management. Risks beget risk management, which in turn begets security. Whether the risks are near the home, on an airplane, or with an online bank account, risk management practices limit the risks, usually through some "security." "The five-year crime numbers in my neighborhood are going up," one might assess. "I shall manage the risk with a home security system," is the risk management action performed. In the same way, engineers add multiple layers of redundancy to an airplane's components to mitigate the assessed risk of instrument failure, and banks require access controls like strong passwords on online accounts to protect customer data and limit their liability. As such, it shouldn't be surprising to talk about employing security and process control measures as part of managing risks in the cloud.
We learned in the last chapter that the National Institute of Standards and Technology (NIST) represents a strong example of a standards and recommendations body in the U.S. In their 2018 SP 800-37 Rev. 2 Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy, NIST says the following about risk management for information systems[1]:
Managing information system-related security and privacy risk is a complex undertaking that requires the involvement of the entire organization—from senior leaders providing the strategic vision and top-level goals and objectives for the organization, to mid-level leaders planning, executing, and managing projects, to individuals developing, implementing, operating, and maintaining the systems supporting the organization’s missions and business functions. Risk management is a holistic activity that affects every aspect of the organization, including the mission and business planning activities, the enterprise architecture, the SDLC processes, and the systems engineering activities that are integral to those system life cycle processes.
As Figure 4—from the same NIST guide—notes, there are three main levels at which an organization must approach risk management activities for their information systems: the organization level, the mission/business process level, and the information system level. The arrow on the left highlights the criticality of proper communication across all three levels in order for the organization to make the most of their risk management activities. Just as IT forms the base of any software-driven business efforts, critical stakeholders in IT form the base of communication about IT risk and security requirements. Without those stakeholders' knowledge and feedback, business processes and company policy would be ill-informed. Now let's start from the top of the pyramid and head downward. Note that without strong leadership, well-crafted business goals, and management buy-in on quality, budget, and security, business processes would be a mess and IT-related efforts would be sub-par and at-risk.
The implication with Figure 4 and NIST's guide is that effective planning and communication is critical to ensuring information systems are implemented securely during their entire life cycle. Many organizations approach this task by developing, implementing, and enforcing a cybersecurity plan, in which identifying cybersecurity requirements and objectives—i.e., risk assessment and management—is a vital component. (See the Comprehensive Guide to Developing and Implementing a Cybersecurity Plan for much more on this topic.)
References
- ↑ 1.0 1.1 National Institute of Standards and Technology (December 2018). "SP 800-37 Rev. 2: Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy". https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final. Retrieved 21 August 2021.









