Difference between revisions of "Template:Article of the week"
Shawndouglas (talk | contribs) (Updated article of the week text) |
Shawndouglas (talk | contribs) (Updated article of the week text) |
||
| Line 1: | Line 1: | ||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File: | <div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig1 Taherdoost Electronics22 11-14.png|240px]]</div> | ||
'''"[[Journal: | '''"[[Journal:Understanding cybersecurity frameworks and information security standards: A review and comprehensive overview|Understanding cybersecurity frameworks and information security standards: A review and comprehensive overview]]"''' | ||
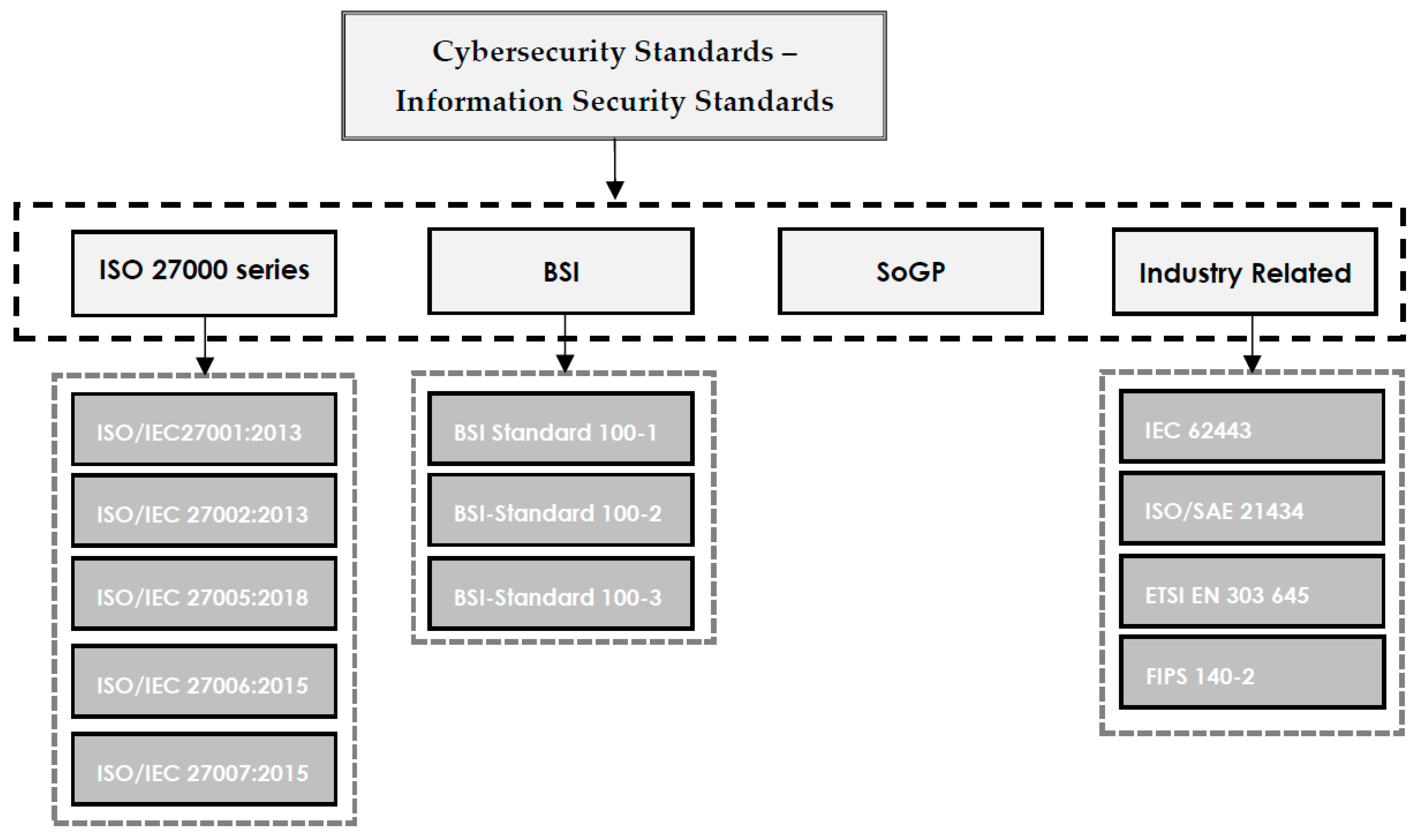
Businesses are reliant on data to survive in the competitive market, and data is constantly in danger of loss or theft. Loss of valuable data leads to negative consequences for both individuals and organizations. [[Cybersecurity]] is the process of protecting sensitive data from damage or theft. To successfully achieve the objectives of implementing cybersecurity at different levels, a range of procedures and standards should be followed. Cybersecurity standards determine the requirements that an organization should follow to achieve cybersecurity objectives and minimize the impact of cybercrimes. Cybersecurity standards demonstrate whether an [[information management]] system can meet security requirements through a range of best practices and procedures. A range of standards has been established by various organizations to be employed in information management systems of different sizes and types ... ('''[[Journal:Understanding cybersecurity frameworks and information security standards: A review and comprehensive overview|Full article...]]''')<br /> | |||
''Recently featured'': | ''Recently featured'': | ||
{{flowlist | | {{flowlist | | ||
* [[Journal:Bridging data management platforms and visualization tools to enable ad-hoc and smart analytics in life sciences|Bridging data management platforms and visualization tools to enable ad-hoc and smart analytics in life sciences]] | |||
* [[Journal:Digitalization of calibration data management in the pharmaceutical industry using a multitenant platform|Digitalization of calibration data management in the pharmaceutical industry using a multitenant platform]] | * [[Journal:Digitalization of calibration data management in the pharmaceutical industry using a multitenant platform|Digitalization of calibration data management in the pharmaceutical industry using a multitenant platform]] | ||
* [[Journal:Introductory evidence on data management and practice systems of forensic autopsies in sudden and unnatural deaths: A scoping review|Introductory evidence on data management and practice systems of forensic autopsies in sudden and unnatural deaths: A scoping review]] | * [[Journal:Introductory evidence on data management and practice systems of forensic autopsies in sudden and unnatural deaths: A scoping review|Introductory evidence on data management and practice systems of forensic autopsies in sudden and unnatural deaths: A scoping review]] | ||
}} | }} | ||
Revision as of 02:23, 24 July 2023
Businesses are reliant on data to survive in the competitive market, and data is constantly in danger of loss or theft. Loss of valuable data leads to negative consequences for both individuals and organizations. Cybersecurity is the process of protecting sensitive data from damage or theft. To successfully achieve the objectives of implementing cybersecurity at different levels, a range of procedures and standards should be followed. Cybersecurity standards determine the requirements that an organization should follow to achieve cybersecurity objectives and minimize the impact of cybercrimes. Cybersecurity standards demonstrate whether an information management system can meet security requirements through a range of best practices and procedures. A range of standards has been established by various organizations to be employed in information management systems of different sizes and types ... (Full article...)
Recently featured:
- Bridging data management platforms and visualization tools to enable ad-hoc and smart analytics in life sciences
- Digitalization of calibration data management in the pharmaceutical industry using a multitenant platform
- Introductory evidence on data management and practice systems of forensic autopsies in sudden and unnatural deaths: A scoping review