Difference between revisions of "Template:Article of the week"
Shawndouglas (talk | contribs) (Updated article of the week text) |
Shawndouglas (talk | contribs) (Updated article of the week text) |
||
| Line 1: | Line 1: | ||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig1 | <div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig1 Annane IntJInterMobileTech2019 13-4.png|240px]]</div> | ||
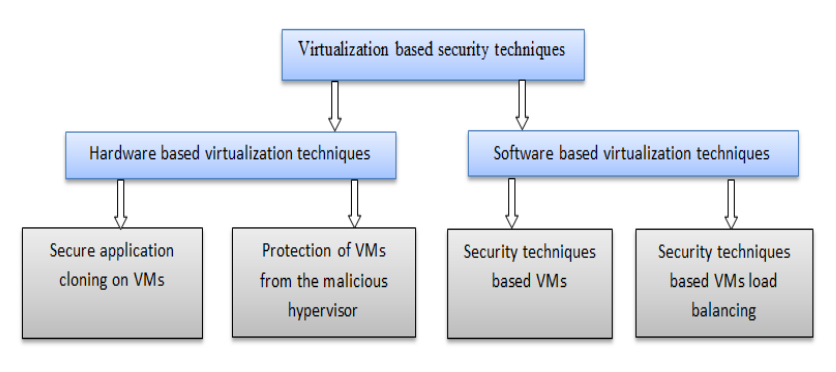
'''"[[Journal: | '''"[[Journal:Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges|Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges]]"''' | ||
The principle constraints of mobile devices are their limited resources, including processing capability, storage space, and battery life. However, [[cloud computing]] offers a means of vast computing resources and services. With it a new idea emerged, the inclusion of cloud computing into mobile devices such as smartphones, tablet, and other personal digital assistants (PDA) to augment their capacities, providing a robust technology called mobile cloud computing (MCC). Although MCC has brought many advantages to mobile users, it also still suffers from the security and privacy issues of data while hosted on virtual machines (VM) on remote cloud’s servers. Currently, the eyes of security experts are turned towards the virtualization-based security techniques used either on the cloud or on mobile devices. The new challenge is to develop secure methods in order to authenticate highly sensitive digital content. ('''[[Journal:Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges|Full article...]]''')<br /> | |||
<br /> | <br /> | ||
''Recently featured'': | ''Recently featured'': | ||
: ▪ [[Journal:Building open access to research (OAR) data infrastructure at NIST|Building open access to research (OAR) data infrastructure at NIST]] | |||
: ▪ [[Journal:Development of standard operating protocols for the optimization of Cannabis-based formulations for medical purposes|Development of standard operating protocols for the optimization of Cannabis-based formulations for medical purposes]] | : ▪ [[Journal:Development of standard operating protocols for the optimization of Cannabis-based formulations for medical purposes|Development of standard operating protocols for the optimization of Cannabis-based formulations for medical purposes]] | ||
: ▪ [[Journal:Next steps for access to safe, secure DNA synthesis|Next steps for access to safe, secure DNA synthesis]] | : ▪ [[Journal:Next steps for access to safe, secure DNA synthesis|Next steps for access to safe, secure DNA synthesis]] | ||
Revision as of 15:24, 7 October 2019
"Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges"
The principle constraints of mobile devices are their limited resources, including processing capability, storage space, and battery life. However, cloud computing offers a means of vast computing resources and services. With it a new idea emerged, the inclusion of cloud computing into mobile devices such as smartphones, tablet, and other personal digital assistants (PDA) to augment their capacities, providing a robust technology called mobile cloud computing (MCC). Although MCC has brought many advantages to mobile users, it also still suffers from the security and privacy issues of data while hosted on virtual machines (VM) on remote cloud’s servers. Currently, the eyes of security experts are turned towards the virtualization-based security techniques used either on the cloud or on mobile devices. The new challenge is to develop secure methods in order to authenticate highly sensitive digital content. (Full article...)
Recently featured: