Difference between revisions of "Journal:Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges"
Shawndouglas (talk | contribs) (Saving and adding more.) |
Shawndouglas (talk | contribs) m (→Notes: Added cat) |
||
| (12 intermediate revisions by the same user not shown) | |||
| Line 29: | Line 29: | ||
Mobile cloud computing (MCC) has quickly grown in popularity among individuals and user communities. It combines the cloud computing paradigm with mobile devices through wireless technology in order to avoid the devices’ capacity restrictions and leverage the resources offered by cloud computing services.<ref name="ZhangEnsuring17">{{cite journal |title=Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing |journal=Information Sciences |author=Zhang, Y.; Chen, X.; Li, J. et al. |volume=379 |pages=42–61 |year=2017 |doi=10.1016/j.ins.2016.04.015}}</ref> Mobile devices such as smartphone and tablets have several limitations in their resource capacities (CPU, memory, and storage space) which inhibit application developers from providing powerful software solutions and hinder users in enjoying those solutions in their daily life.<ref name="RahimiMobile14" /> Integrating cloud computing services with mobile computing is an interesting solution towards solving these issues. MCC allows users to upload and move their applications, services, and data on shared cloud servers, taking advantage of their large remote storage capacity and significant computing resources when running intensive applications, taking the strain off the battery life of mobile devices. Recently, the use of mobile devices has moved beyond simple applications and into more complex and crucial applications which deal with sensitive data in various multimedia formats (text, images, audio, and video), including banking, health, and transport applications. The moving of clients’ data and services to the cloud raises many security challenges, particularly involving the major concerns of data security and privacy protection due to data being located in different distributed places. | Mobile cloud computing (MCC) has quickly grown in popularity among individuals and user communities. It combines the cloud computing paradigm with mobile devices through wireless technology in order to avoid the devices’ capacity restrictions and leverage the resources offered by cloud computing services.<ref name="ZhangEnsuring17">{{cite journal |title=Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing |journal=Information Sciences |author=Zhang, Y.; Chen, X.; Li, J. et al. |volume=379 |pages=42–61 |year=2017 |doi=10.1016/j.ins.2016.04.015}}</ref> Mobile devices such as smartphone and tablets have several limitations in their resource capacities (CPU, memory, and storage space) which inhibit application developers from providing powerful software solutions and hinder users in enjoying those solutions in their daily life.<ref name="RahimiMobile14" /> Integrating cloud computing services with mobile computing is an interesting solution towards solving these issues. MCC allows users to upload and move their applications, services, and data on shared cloud servers, taking advantage of their large remote storage capacity and significant computing resources when running intensive applications, taking the strain off the battery life of mobile devices. Recently, the use of mobile devices has moved beyond simple applications and into more complex and crucial applications which deal with sensitive data in various multimedia formats (text, images, audio, and video), including banking, health, and transport applications. The moving of clients’ data and services to the cloud raises many security challenges, particularly involving the major concerns of data security and privacy protection due to data being located in different distributed places. | ||
Security is considered a major challenge with MCC environments. Mobile cloud security's issues are inherited from cloud computing, so we are at least familiar with those issues; however, those issues are more critical with MCC because of devices’ limited resource capacity (e.g., lack of CPU capability) to handle CPU-intensive malware detection applications that protect sensitive data, at least when compared to personal computers. The tenants’ worries are concentrated on the migration to the cloud of their data, which might face more risks once they share the same cloud resources with other tenants.<ref name="MollahSecurity17">{{cite journal |title=Security and privacy challenges in mobile cloud computing: Survey and way ahead |journal=Journal of Network and Computer Applications |author=Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. |volume=84 |pages=38–54 |year=2017 |doi=10.1016/j.jnca.2017.02.001}}</ref> With MCC, cloud service providers offer the sharing of their resources to mobile users through the popular technique of virtualization, which increases the efficiency and effectiveness of hardware utilization.<ref name="HanUsing15">{{cite journal |title=Using Virtual Machine Allocation Policies to Defend against Co-Resident Attacks in Cloud Computing |journal=IEEE Transactions on Dependable and Secure Computing |author=Han, Y.; Chan, J.; Alpcan, T. et al. |volume=14 |issue=1 |pages=95–108 |year=2015 |doi=10.1109/TDSC.2015.2429132}}</ref> Various users’ virtual machines are running on the same cloud host when they share the same cloud resources, which leads to additional security risks like violating data use terms once the data shares the same memory or CPU.<ref name="RistenpartHeyYou09">{{cite journal |title=Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds |journal=Proceedings of the 16th ACM Conference on Computer and Communications Security |author=Ristenpart, T.; Tromer, E.; Shacham, H. et al. |pages=199–212 |year=2009 |doi=10.1145/1653662.1653687}}</ref><ref name="ZhangCross12">{{cite journal |title=Cross-VM side channels and their use to extract private keys |journal=Proceedings of the 2012 ACM Conference on Computer and Communications Security |author=Zhang, Y.; Juels, A.; Reiter, M.K. et al. |pages=305–316 |year=2012 |doi=10.1145/2382196.2382230}}</ref> Consequently, an important question must be raised whether the other cloud virtual machines’ clients are trusted or not. Several robust security techniques have been proposed in this decade, and a number of new techniques or improved versions of the latest approaches have been developed. However, most of the solutions proposed are not practical due to the critical change—eliminating side channels and clocks, as well as the hypervisor—that comes with the cloud platform.<ref name="HanUsing15" /> In this work, we aim to collect and present some relevant virtualization-based security techniques currently available in the field and review in detail the topic of various newly emerged security challenges. | |||
The rest of this paper is organized as follows. Firstly, we present basic requirements of the virtualization techniques on MCC. We detail malicious attacks and briefly review quality measures. Then, we discuss the recent virtualization security techniques, with comparison and evaluation of different approaches also presented. Then, we present discussion, research gaps, and challenges concerning a security-based virtualization layer. Finally, in the last section, we conclude and present plans for future work. | |||
==Virtualization-based security preliminaries== | |||
In MCC, cloud services are provided for mobile users using virtualization technologies. Virtualization is defined as a middle layer between the software and hardware layers in a cloud server that allows the cloud provider to efficiently exploit their services and computing resources.<ref name="SgandurraEvol16">{{cite journal |title=Evolution of Attacks, Threat Models, and Solutions for Virtualized Systems |journal=ACM Computing Surveys (CSUR) |author=Sgandurra, D.; Lupu, E. |volume=48 |issue=3 |pages=46 |year=2016 |doi=10.1145/2856126}}</ref> These resources can be shared among multiple virtual machines in order to run services simultaneously while also sharing benefits from available servers’ resources (e.g., CPU, network bandwidth, memory, etc.).<ref name="IslamMobile17">{{cite journal |title=Mobile Cloud-Based Big Healthcare Data Processing in Smart Cities |journal=IEEE Access |author=Islam, M.; Rzzaque, A.; Hassan, M.H. et al. |volume=5 |pages=11887–11899 |year=2017 |doi=10.1109/ACCESS.2017.2707439}}</ref> The virtualization process can reportedly increase hardware utilization (efficiency) between 60% and 80%.<ref name="HuAReview11">{{cite journal |title=A Review on Cloud Computing: Design Challenges in Architecture and Security |journal=Journal of Computing and Information Technology |author=Hu, F.; Qiu, M.; Li, J. et al. |volume=19 |issue=1 |pages=25–55 |year=2011 |doi=10.2498/cit.1001864}}</ref> The use of remote servers and other hardware utilization techniques also improves mobile device battery life by saving energy.<ref name="EllouzeAMobile15">{{cite journal |title=A Mobile Application Offloading Algorithm for Mobile Cloud Computing |journal=Proceedings of the 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering |author=Ellouze, A.; Gagnaire, M.; Haddad, A. |pages=34–40 |year=2015 |doi=10.1109/MobileCloud.2015.11}}</ref><ref name="DhanyaAdapt15">{{cite journal |title=Adaptive and Secure Application Partitioning for Offloading in Mobile Cloud Computing |journal=SSCC 2015: International Symposium on Security in Computing and Communication |author=Dhanya, N.M.; Kousalya, G. |pages=45–53 |year=2015 |doi=10.1007/978-3-319-22915-7_5}}</ref> | |||
The execution of mobile applications is considered a computationally intensive task that requires significant resource consumption on mobile devices. However, this kind of challenge has been defeated by the offloading technique. The computationally intensive application is divided into many tasks, which are migrated to the cloud (remote servers) for fast processing, with the results returned back to the mobile terminal afterwards.<ref name="ShirazARev13">{{cite journal |title=A Review on Distributed Application Processing Frameworks in Smart Mobile Devices for Mobile Cloud Computing |journal=IEEE Communications Surveys & Tutorials |author=Shiraz, M.; Gani, A.; Jhokhar, R. et al. |volume=15 |issue=3 |pages=1294–1313 |year=2013 |doi=10.1109/SURV.2012.111412.00045}}</ref> On the cloud end, once the mobile task is offloaded, a virtual machine image of the mobile device (also called a "phone clone") is pre-installed for processing the mobile user’s application data, which increases the efficiency of the cloud environment and decreases the maintenance overhead on the mobile device.<ref name="MollahSecurity17" /><ref name="SahooVirt10">{{cite journal |title=Virtualization: A Survey on Concepts, Taxonomy and Associated Security Issues |journal=Second International Conference on Computer and Network Technology |author=Sahoo, J.; Mohapatra, S.; Lath, R. |pages=222–226 |year=2010 |doi=10.1109/ICCNT.2010.49}}</ref> Therefore, running the phone clone of the mobile device on the same server and isolating them is the main role of the virtualization technology. However, multiple works<ref name="HanUsing15" /><ref name="RistenpartHeyYou09" /><ref name="HaoSMOC15">{{cite journal |title=SMOC: A secure mobile cloud computing platform |journal=2015 IEEE Conference on Computer Communications |author=Hao, Z.; Tang, Y.; Zhang, Y. et al. |pages=2668-2676 |year=2015 |doi=10.1109/INFOCOM.2015.7218658}}</ref><ref name="PaladiProvid17">{{cite journal |title=Providing User Security Guarantees in Public Infrastructure Clouds |journal=IEEE Transactions on Cloud Computing |author=Paladi, N.; Gehrmann, C.; Michalas, A. |volume=5 |pages=405-419 |year=2017 |doi=10.1109/TCC.2016.2525991}}</ref><ref name="HanVirtual14">{{cite journal |title=Virtual machine allocation policies against co-resident attacks in cloud computing |journal=2014 IEEE International Conference on Communications |author=Han, Y.; Chan, J.; Alpcan, T. et al. |pages=786-792 |year=2014 |doi=10.1109/ICC.2014.6883415}}</ref><ref name="YuDetect13">{{cite journal |title=Detecting VMs Co-residency in Cloud: Using Cache-based Side Channel Attacks |journal=Elektronika ir Elektrotechnika |author=Yu, S.; Xiaolin, G.; Jiancai, L. et al. |volume=19 |issue=5 |pages=73–78 |year=2013 |doi=10.5755/j01.eee.19.5.2422}}</ref><ref name="VaezpourANew16">{{cite journal |title=A new approach to mitigating security risks of phone clone co-location over mobile clouds |journal=Journal of Network and Computer Applications |author=Vaezpour, S.Y.; Zhang, R.; Wi, K. et al. |volume=62 |pages=171–184 |year=2016 |doi=10.1016/j.jnca.2016.01.005}}</ref> have shown that virtualization has brought with it several security concerns<ref name="SgandurraEvol16" /> that affect virtualized systems, including denial-of-service (DOS) attacks. This kind of attack hits insipid information like workload statistics to know whether the system is vulnerable or not. Moreover, virtualization techniques on MCC brings new security risks such as unauthorized access from malicious virtual machines (VMs), VM-to-VM attacks, breaches of confidential mobile user data, VM monitoring challenges (e.g., the hypervisor), and communication challenges in a virtualized environment.<ref name="MollahSecurity17" /><ref name="SgandurraEvol16" /> Thus, ensuring security mechanisms that prevent leakage of sensitive data and information from legitimate phone clones is not an easy task. | |||
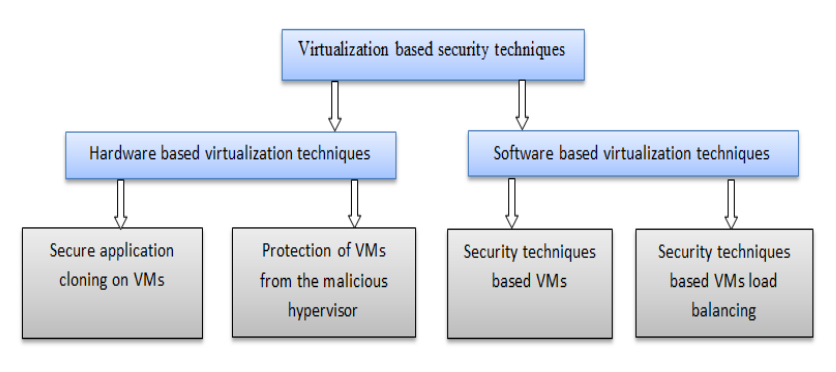
In terms of security, virtualization-based techniques are regrouped into two main categories: hardware-based techniques and software-based techniques. For the first class, we distinguish secure application cloning on VM<ref name="HaoSMOC15" /> and the protection of VMs from a malicious hypervisor<ref name="JinH-SVM15">{{cite journal |title=H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor |journal=IEEE Transactions on Computers |author=Jin, S.; Ahn, J.; Seol, J. et al. |volume=64 |issue=10 |pages=2833–2846 |year=2015 |doi=10.1109/TC.2015.2389792}}</ref> as two useful techniques. For the second, we also consider two techniques: VM-based security techniques<ref name="PaladiProvid17" /><ref name="HanVirtual14" /><ref name="YuDetect13" /><ref name="LiangALight15">{{cite journal |title=A Lightweight Security Isolation Approach for Virtual Machines Deployment |journal=Inscrypt 2014: International Conference on Information Security and Cryptology |author=Liang, H.; Han, C.; Zhang, D. et al. |pages=516–529 |year=2015 |doi=10.1007/978-3-319-16745-9_28}}</ref> and security techniques based on load balancing the VM.<ref name="HanUsing15" /><ref name="VaezpourANew16" /> Fig. 1 summarizes the important classes of virtualization-based security approaches. | |||
[[File:Fig1 Annane IntJInterMobileTech2019 13-4.png|836px]] | |||
{{clear}} | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| border="0" cellpadding="5" cellspacing="0" width="836px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"| <blockquote>'''Fig. 1''' Classification of virtualization-based security techniques</blockquote> | |||
|- | |||
|} | |||
|} | |||
Virtualization-based security techniques have five important proprieties<ref name="HanVirtual14" /><ref name="SuoSecur13">{{cite journal |title=Security and privacy in mobile cloud computing |journal=Proceedings from the 9th International Wireless Communications and Mobile Computing Conference |author=Suo, H.; Liu, Z.; Wan, J. et al. |pages=655–659 |year=2013 |doi=10.1109/IWCMC.2013.6583635}}</ref>: efficiency, coverage, complexity, security, and robustness. Roughly speaking, efficiency represents the number of malicious VMs that succeed to co-locate with a target (victim VM), divided by the total number of VMs lunched by the attacker. Coverage represents the number of malicious VMs that succeed to co-locate with a target, divided by the number of targets lunched by a legitimate user. Complexity in security is defined as any secure complex technique that needs high execution time, high computation complexity, and high energy consumption from the cloud server. Security refers to the privacy of the VMs and their sensitive data, meaning that optimally no one would be able to remove or extract the data without knowing the secure key. Similarly, robustness refers to the degree of resistance against any kind of manipulation. Any new approach must negotiate a trade-off among these five proprieties. | |||
Many researchers have begun developing frameworks, policies, and approaches against these kinds of challenges to ensure security for mobile users. These methods are mainly focused on how to ignore the side channel attacks between VMs while the malicious VMs access the cloud servers.<ref name="VattikondaElim11">{{cite journal |title=Eliminating fine grained timers in Xen |journal=Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop |author=Vattikonda, B.C.; Das, S.; Shacham, H. |pages=41–46 |year=2011 |doi=10.1145/2046660.2046671}}</ref><ref name="WuXenPump12">{{cite journal |title=XenPump: A New Method to Mitigate Timing Channel in Cloud Computing |journal=IEEE Fifth International Conference on Cloud Computing |author=Wu, J.; Ding, L.; Lin, Y. et al. |pages=678–685 |year=2012 |doi=10.1109/CLOUD.2012.28}}</ref><ref name="AviramDeterm10">{{cite journal |title=Determinating timing channels in compute clouds |journal=Proceedings of the 2010 ACM Workshop on Cloud Computing Security Workshop |author=Aviram, A.; Hu, S.; Ford, B. et al. |pages=103–108 |year=2010 |doi=10.1145/1866835.1866854}}</ref><ref name="ShiLimit11">{{cite journal |title=Limiting cache-based side-channel in multi-tenant cloud using dynamic page coloring |journal=IEEE/IFIP 41st International Conference on Dependable Systems and Networks Workshops |author=Shi, J.; Song, X.; Chen, H. et al. |pages=194–199 |year=2011 |doi=10.1109/DSNW.2011.5958812}}</ref> However, all the methods proposed require fundamental changes to the current commercial platform, and they are neither practical nor immediately deployable.<ref name="HanVirtual14" /> Additionally, while also strong candidates, hardware-based techniques lead to a high cost barrier.<ref name="HaoSMOC15" /> | |||
==Virtualization-based security techniques== | |||
How to protect virtual machines (VM) and sensitive data is undoubtedly one of the most important topics regarding MCC. Recent security techniques have been used largely to tackle the security issues related to the virtualized environment in either cloud or mobile cloud computing.<ref name="HanUsing15" /><ref name="HaoSMOC15" /><ref name="PaladiProvid17" /><ref name="HanVirtual14" /><ref name="YuDetect13" /><ref name="VaezpourANew16" /><ref name="JinH-SVM15" /><ref name="LiangALight15" /> This section discusses recent techniques described in the literature. | |||
===Virtualization-based security VM techniques=== | |||
====Hardware virtualization-based technique for securing application cloning on VM==== | |||
Hao ''et al.''<ref name="HaoSMOC15" /> have presented a platform called Secure Mobile Cloud Platform (SMOC) for securing the mobile cloud environment. The platform allows the user to run their applications whether on the cloud or directly on the mobile device itself. In contrast, their proposed platform includes two concepts. The first one is sharing resources, which means that a mobile application can freely change the run-from location for providing a better user experience, i.e., not running explicitly on the cloud. This design provides more flexibility compared to other proposed approaches and techniques. The second concept is ensuring security even though the operating system of the mobile device has been attacked. A thin virtual machine shares its information and files with the mobile device once the mobile application is running in the cloud. Conversely, the mobile device shares its files and information (device inputs and outputs) with the VM-cloud for running the application. Despite the benefits of this platform towards security concerns, many assumptions are made by the researchers, who fail to consider issues with an untrusted hypervisor and untrusted public cloud provider. The proposed platform ensures data security and privacy only when both assumptions (hypervisor and cloud provider) are assured. Thus, this platform ensures security towards an untrusted guest operating system which also runs unsecure applications. | |||
====Encryption protocol-based virualization technique for trusting launch of VM==== | |||
Paladi ''et al.''<ref name="PaladiProvid17" /> proposed a framework for data and transaction security of infrastructure services. The proposed framework contains various protocols for trust and the storage protection operation called Domain-Based Storage Protection (DBSP), as well as another protocol for trusting virtual machine deployment called TrustLunching. Trust VMs made a more suitable method when the virtual machines were running inside a trusted host using secure computing techniques. Their proposed solutions completed several attack-based security analyses, and the obtained results improved the robustness and the efficiency of their framework. Before the deployment of guest VMs, the protocol of trust VMs is performed. The second protocol used cryptography techniques outside the IaaS domain for ensuring the data confidentiality stored in the cloud. As such, a list of malicious host attacks against IaaS environments are demonstrated to produce both secure protocols. The proposed framework can be integrated into the existing cloud platform thanks to numerous successful experiments and tests run on tenants’ sensitive data (e.g., public healthcare patients’ data). However, this work focused specifically on attacks of IaaS platforms, which doesn't guarantee security for other threats such as hypervisor attacks, co-resident attacks, and so on. | |||
====VM allocation policy for defending co-residency attack==== | |||
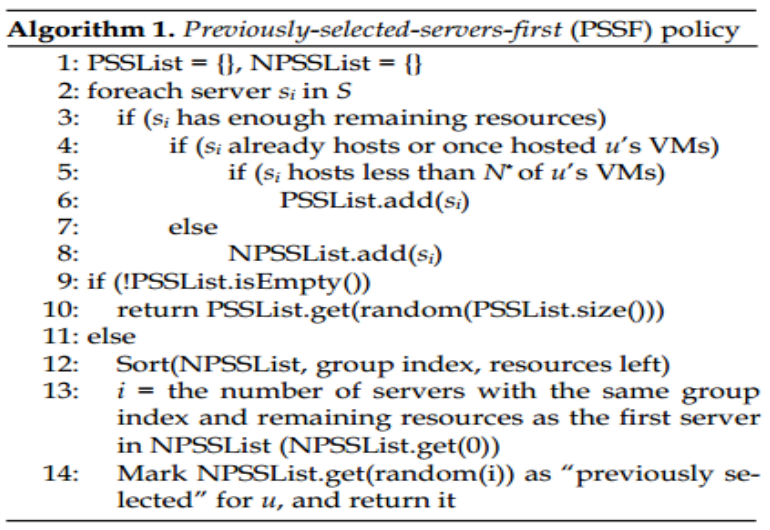
Frequently, VMs of different mobile users executed on the same physical host are logically isolated from each other. However, malevolent users can escape this logical isolation while sharing the same resources (CPU, memory, and cache) and capture sensitive and private information like crypto keys from co-resident virtual machines.<ref name="RistenpartHeyYou09" /><ref name="ZhangCross12" /> Han ''et al.''<ref name="HanVirtual14" /> have proposed a new secure VM allocation policy called Previous Selected Servers First Policy (PSSF). (The algorithm is shown in Fig.2.) The aim of this policy is to defend against co-resident attack. However, the proposed algorithm lacks various security enhancements such as securing the mobile device VMs residing on it, live migration, and securing the communication data between the VMs while located on mobile devices and in the cloud. The algorithm also lacks a distributed application security algorithm deployment for mobile and the cloud. Finally, this algorithm only targets co-resident attacks and does not target other types of attacks like distributed VM communication attacks, hypervisor attacks, and mobile device data attacks. | |||
[[File:Fig2 Annane IntJInterMobileTech2019 13-4.png|500px]] | |||
{{clear}} | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| border="0" cellpadding="5" cellspacing="0" width="500px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"| <blockquote>'''Fig. 2''' PSSF Algorithm<ref name="HanVirtual14" /></blockquote> | |||
|- | |||
|} | |||
|} | |||
====Mechanism-based network measurement for detecting VMs co-residency==== | |||
Yu ''et al.''<ref name="YuDetect13" /> have presented a new schema for detecting the VMs co-residency attacks by getting the location of the particular VM. The covert side channel is a kind of attack that breaks the isolation between the VMs, leading to the theft of sensitive information from users. To clarify more, the simple way to know whether two VMs are on the host is to rely on network metrics by performing TCP "traceroute" steps to get the IP address of the hypervisor. If two hypervisor IP addresses are the same, that means corresponding VMs are on the same host (co-resident). The advantage of this solution is that it increases the difficulty of establishing co-location. However, the attacker can still use other techniques to steal information from legitimate user VMs. As such, a simple hiding of the IP address of the hypervisor isn't sufficient to solve the co-residency issue. | |||
====Comparing the virtualization-based security techniques on VM==== | |||
In Table 1, the above virtualization-based security techniques on VM are compared in terms of strengths and drawbacks. | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="70%" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" colspan="4"|'''Table 1.''' Comparison of different virtualization-based security techniques on VM | |||
|- | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Authors | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Technique | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Strengths | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Drawbacks | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Hao ''et al.''<ref name="HaoSMOC15" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Hardware virtualization-based technique | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The security of the mobile device operating system is ensured even when the latter is attacked.<br />- Free to execute the mobile application on both the mobile device or in the cloud. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The proposed work assumes that both hypervisor and cloud are always secure, so if the adversary succeeds in penetrating them, the data of the user would be at risk<br />- The mobile application dynamically migrates within VMs on the cloud. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Paladi ''et al.''<ref name="PaladiProvid17" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Protocol for the trusted lunch of a VM-encryption-based technique to protect the stored data using a trusted third-party entity | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Ensures the confidentiality of sensitive data and information of the user. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The framework handles specified attacks on an IaaS platform, though not guaranteed to protect against other security threats such as attacks on network communication and data geo-localization. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Han ''et al.''<ref name="HanVirtual14" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|VM allocation policy | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The policy protects the VMs allocated on the same host to be co-located from malicious users. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- -The policy does not secure the interaction between VMs that are allocated on a different host.<br />- The policy does not secure the mobile user data while moving from the mobile device to the cloud.<br />- The policy has an absence of data isolation while VMs communicate between each other.<br />- The policy only decreases the efficiency and coverage attacks on the host. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Yu ''et al.''<ref name="YuDetect13" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Mechanism -based network measurement | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Increases the difficulty for malicious users to determine co-location on the user VMS. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Simple hiding of the hypervisor IP address is not sufficient, and the adversary can use another way to steal information from VMs. | |||
|- | |||
|} | |||
|} | |||
===Virtualization-based load balancing security techniques on VM=== | |||
====Dynamic allocation and migration for phone clones for preventing covert channel attacks==== | |||
Vaezpour ''et al.''<ref name="VaezpourANew16" /> have proposed a security scheme called the Security-aware Provisioning and Migration Scheme (SWAP) for provisioning and migrating thin virtual machines (phone clones) for preventing covert channel attacks.<ref name="VaezpourANew16" /> This kind of attack is a constructed link between VMs where the CPU cache and the memory bus are exploited to steal information from legitimate phone clones in a virtualized environment.<ref name="RistenpartHeyYou09" /> The goal of their work is to reduce the risks of covert channel attacks when the cloud provider does not have enough resources to isolate the foreigner’s phone clones on the mobile cloud environment. Their proposed scheme includes two techniques. The first one is provisioning new phone clones, where this technique works, with mobile communication history to prevent users’ phone clone from hosting with other strangers’ thin virtual machine. The second technique involves migrating the phone clones from one host to another when the threat of attacks increases. The first and second algorithm is used to allocate the phone clones on the specified host by implementing various conditions. The algorithm is based on the communication history between the mobile users, where the virtual machines represent the node and communication between the virtual machines represent the edges. Thus, both algorithms allocate the phone clones based on communication history between the mobile users. The phone clones that have a communication link would not attack each other and may allocate in the same host. The third algorithm is for moving the phone clone from a host to another one in order to prevent the risks of retrieving the content of the phone clone from another adversary. The proposed solution has successfully kept few risks on phone clones compared with other proposed techniques. The main shortcoming of the proposed approach is that the researchers assumed that two phone clones on the same host cannot attack each other when they have a communication link between them. This work does not consider different scenarios (co-resident attacks, hypervisor attacks) which can produce several security threats on the phone. | |||
====Context-aware VM allocation policy for defending against co-resident attacks==== | |||
Han ''et al.''<ref name="HanUsing15" /> have proposed an approach to minimize co-resident attacks in cloud environments. Their work improved the VM allocation policy—which extends the previously discuss PSSF tool<ref name="HanVirtual14" />—with three additional policies: security, power consumption, and load balance to enhance the effectiveness and the efficiency of the cloud environment. Moreover, they applied several experiments on the simulation cloud platform CloudSim, and the obtained results showed a remarkable robustness against co-resident attacks. However, the authors have only studied one type of attack: a co-resident attack that occurred only on one host and not distributed on different hosts. They also did not consider migration attacks, which constitute serious risks on VMs and increase the possibility of co-locating with VM victims. | |||
====Comparing the virtualization-based load balancing security techniques on VM==== | |||
In Table 2, the above virtualization-based load balancing techniques on VM are compared in terms of strengths and drawbacks. | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="70%" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" colspan="4"|'''Table 2.''' Comparison of different virtualization-based load balancing security techniques on VM | |||
|- | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Authors | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Technique | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Strengths | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Drawbacks | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Vaezpour ''et al.''<ref name="VaezpourANew16" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|1. Model-based user communication relationships and their potential risks when co-locating phone clones<br /> 2. Minimizing potential risks based on clique-covering techniques.<br />3. Migration strategy based on a decay function time-varying feature of covert channel. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Successfully minimizes the risk of phone clones’ attacks compared with a naïve provisioning and migration algorithm.<br />- Reasonable trade-off between security and load balancing. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The researchers failed to address how two phone clones on the same host can attack each other when they have a communication link between each other. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Han ''et al.''<ref name="HanUsing15" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Load balancing VM allocation policy | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The policy protects the VMs allocated on the same host to be co-located from malicious users.<br /> -Reasonable trade-off between security, load balancing, and power consumption. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Notable absence of data isolation while VMs communicate between each other (such as with tasks of distributed application).<br />- The researchers do not consider migration attacks, which can happen due to the vulnerabilities of the migration algorithm. | |||
|- | |||
|} | |||
|} | |||
===Virtualization-based security techniques on the hypervisor=== | |||
====Hardware-assisted secure VMs under a vulnerable hypervisor==== | |||
Jin ''et al.''<ref name="JinH-SVM15" /> have proposed a new design for hardware-based VM protection. Their approach is called a Hardware-Assisted Secure Virtual Machine (H-SVM). The proposed mechanism protects the guest virtual machine for monitoring the malicious VM or hypervisor by isolating its memory virtualization. The authors have proposed a new flexible and efficient mechanism of memory protection by allowing restricted roles for the hypervisors and decoupling the memory isolation from memory allocation, which is usually executed by the hypervisor. Therefore, the handler (processor) takes some roles of the hypervisor such as scheduling VMs. The mechanism of changing the hardware architecture presents drawbacks regarding the deployment cost and proves unsuitable for immediate deployment. | |||
====Mechanism-based Linux kernel Mandatory Access Control (MAC) for securing VMs deployment==== | |||
Liang ''et al.''<ref name="LiangALight15" /> have proposed an approach for securing VM deployment. Their approach reinforces the isolation among the virtual machines and controls the availability of resources by using a security system mechanism called Mandatory Access Control (MAC). MAC controls access to the various running processes. They used the hypervisor that is running on the server operating system to secure the isolation of guest VMs. In addition, they implemented a secure channel for migrating the VMs whenever risk threat heightens. Despite the benefits of the solution proposed, the authors have seemingly assumed that the hypervisor is trusted, with other studies proving that several crucial attacks may come from an untrusted hypervisor. Therefore, the authors do not give an evaluation that makes their solution more practical. | |||
====Comparing the virtualization-based security techniques on the hypervisor==== | |||
In Table 3, the above virtualization-based techniques on the hypervisor are compared in terms of strengths and drawbacks. | |||
{| | |||
| STYLE="vertical-align:top;"| | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="70%" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" colspan="4"|'''Table 3.''' Comparison of different virtualization-based security techniques on the hypervisor | |||
|- | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Authors | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Technique | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Strengths | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;"|Drawbacks | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Jin ''et al.''<ref name="JinH-SVM15" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Hardware-Assisted Secure VM | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- The solution ensures the protection of the virtual machines under a vulnerable hypervisor. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Hardware architecture changes are not practical due to high deployment cost in the current cloud environment. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Liang ''et al.''<ref name="LiangALight15" /> | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|Mechanism-based Linux kernel Mandatory Access Control (MAC) for securing VMs | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- Deployed VMs are secured via an isolating technique.<br />- Online VMs migrate by introducing a secure channel among them. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;"|- A compromised or untrusted hypervisor will lead to an insecure status of VMs. | |||
|- | |||
|} | |||
|} | |||
==Virtualization-based security challenges== | |||
From the above three tables, it can be clearly seen that previous research on virtualization-based security has many limitations. First, such proposed solutions lack a mechanism that ensures the communication between VMs located on different servers. To clarify, researchers such as Han ''et al.''<ref name="HanVirtual14" /> have a great idea in providing two metrics for measuring attacks (coverage and efficiency), yet they fail to consider the issues of data interaction between the VMs where an attacker can perform malicious activity while they communicate. Second, some solutions assume that the hypervisor is always protected unless the attacker can gain the control of the hypervisor, which directly controls the VMs. Finally, other solutions provide security using phone clones on the cloud side, but not on mobile devices. | |||
To enhance security on mobile-based distributed applications using virtualization, we must take into consideration numerous challenging aspects of MCC: scalability, credibility, and robust communication techniques. Secure mobile distributed applications must address these three significant challenges to better perform in regards to VM security and data privacy. | |||
'''1. Virtualization-based scalability''': The problem with system overload is one of the main drivers for the construction of virtualization-based load balancing systems. To clarify, as the number of mobile users’ requests for services increases, the load-balancing problem becomes an even greater challenge. A personalized security system<ref name="HanUsing15" /> enables the handling of virtual machines on a larger scale and intensive application management in cloud systems. | |||
'''2. Virtualization-based credibility''': The trustworthiness problem represents one of the great difficulties faced by security on MCC. The use of trust and information confidence on MCC allows making the cloud provider more reliable and capable to solve the problem of data credibility. Researchers such as Xu ''et al.''<ref name="XuVirtu17">{{cite journal |title=Virtualization of the Encryption Card for Trust Access in Cloud Computing |journal=IEEE Access |author=Xu, D.; Fu, C.; Li, G. et al. |volume=5 |pages=20652-20667 |year=2017 |doi=10.1109/ACCESS.2017.2754515}}</ref> ensure the trustworthiness of a cloud system by finding the trust server, with a reputation value more than 0.8. According to their past feedback, this trust value enables mobile users to select the best offloading and solve security problems such as integrity and confidentiality. | |||
'''3. Virtualization-based distributed VMs with robust encryption communication techniques''': Mobile-based virtualization provides the capability of exploiting and managing distributed heterogeneous applications in the cloud. Virtualization techniques provide a resource sharing mechanism that protects the sensitive data dynamically by isolating any malicious user task. The core idea is directly stopping the attacker by passing on the cloud hypervisor and adapting advance virtualization-based hash techniques to preserve data integrity and confidentiality. | |||
==Conclusions and future work== | |||
With the appearance of new technologies, preserving the security and authenticity of mobile applications that exchange sensitive data becomes a fundamental and necessary requirement in the cloud environment. Over previous years, a number of different researchers have proposed various virtualization-based techniques, but each method has a number of associated advantages as well as drawbacks. To clarify, the user thin virtual machines communicate with each other to exchange private and sensitive information (e.g., a distrusted application executed on a different host). We have studied the limitations of most existing virtualization security co-location techniques proposed in the literature. As a result, we have identified that the main limitation is the absence of protecting sensitive information exchanged between mobile application’s tasks deployed on different VMs on the cloud. In future work, we will present a new approach that contains three secure policies to protect users' sensitive data against co-resident and hypervisor attacks, as well as preserve the communication of users' sensitive data when deployed on a different cloud host. Furthermore, we aim to provide for mobile users additional advantages such as detection of unauthorized access, hypervisor security control on sensitive data, and improved confidentiality during the exchange of sensitive data among VMs. | |||
==References== | ==References== | ||
| Line 34: | Line 208: | ||
==Notes== | ==Notes== | ||
This presentation attempts to remain faithful to the original, with only a few minor changes to presentation. Grammar and punctuation has been updated reasonably to improve readability. In some cases important information was missing from the references, and that information was added. | This presentation attempts to remain faithful to the original, with only a few minor changes to presentation. Grammar and punctuation has been updated reasonably to improve readability. In some cases important information was missing from the references, and that information was added. References appear in the order of the inline citations, by design. | ||
<!--Place all category tags here--> | <!--Place all category tags here--> | ||
| Line 41: | Line 215: | ||
[[Category:LIMSwiki journal articles on cloud computing]] | [[Category:LIMSwiki journal articles on cloud computing]] | ||
[[Category:LIMSwiki journal articles on cybersecurity]] | [[Category:LIMSwiki journal articles on cybersecurity]] | ||
[[Category:LIMSwiki journal articles on information technology]] | |||
[[Category:LIMSwiki journal articles on privacy]] | |||
Latest revision as of 18:54, 14 October 2019
| Full article title | Virtualization-based security techniques on mobile cloud computing: Research gaps and challenges |
|---|---|
| Journal | International Journal of Interactive Mobile Technologies |
| Author(s) | Annane, Boubakeur; Ghazali, Osman |
| Author affiliation(s) | Universiti Utara Malaysia |
| Primary contact | Email: jakhar256 at yahoo dot com |
| Year published | 2019 |
| Volume and issue | 13(4) |
| Page(s) | 20–32 |
| DOI | 10.3991/ijim.v13i04.10515 |
| ISSN | 1865-7923 |
| Distribution license | Creative Commons Attribution 3.0 Austria |
| Website | https://online-journals.org/index.php/i-jim/article/view/10515 |
| Download | https://online-journals.org/index.php/i-jim/article/download/10515/5587 (PDF) |
Abstract
The principle constraints of mobile devices are their limited resources, including processing capability, storage space, and battery life. However, cloud computing offers a means of vast computing resources and services. With it a new idea emerged, the inclusion of cloud computing into mobile devices such as smartphones, tablet, and other personal digital assistants (PDA) to augment their capacities, providing a robust technology called mobile cloud computing (MCC). Although MCC has brought many advantages to mobile users, it also still suffers from the security and privacy issues of data while hosted on virtual machines (VM) on remote cloud’s servers. Currently, the eyes of security experts are turned towards the virtualization-based security techniques used either on the cloud or on mobile devices. The new challenge is to develop secure methods in order to authenticate highly sensitive digital content. This paper investigates the main challenges regarding the security and privacy issues inherent to the mobile cloud, focusing on the virtualization issue layer and giving clear strengths and weaknesses of recent relevant virtualization security techniques existing in the literature. Hence, the paper provides perspectives for researchers to adapt in order to achieve progress with future work.
Keywords: mobile cloud computing; virtualization; security and privacy of information; user virtual machines
Introduction
Nowadays, cloud computing is an attractive technology that is known to have an increasing importance for users by delivering services over the internet. It is defined as an information technology (IT) paradigm that allows the user to exploit cloud services in an on-demand way.[1] Three main services are provided: infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). In IaaS, virtualization relies on sharing computing resources rather than having personal mobile devices to handle and to perform applications and tasks simultaneously and efficiently.[2]
Mobile cloud computing (MCC) has quickly grown in popularity among individuals and user communities. It combines the cloud computing paradigm with mobile devices through wireless technology in order to avoid the devices’ capacity restrictions and leverage the resources offered by cloud computing services.[3] Mobile devices such as smartphone and tablets have several limitations in their resource capacities (CPU, memory, and storage space) which inhibit application developers from providing powerful software solutions and hinder users in enjoying those solutions in their daily life.[2] Integrating cloud computing services with mobile computing is an interesting solution towards solving these issues. MCC allows users to upload and move their applications, services, and data on shared cloud servers, taking advantage of their large remote storage capacity and significant computing resources when running intensive applications, taking the strain off the battery life of mobile devices. Recently, the use of mobile devices has moved beyond simple applications and into more complex and crucial applications which deal with sensitive data in various multimedia formats (text, images, audio, and video), including banking, health, and transport applications. The moving of clients’ data and services to the cloud raises many security challenges, particularly involving the major concerns of data security and privacy protection due to data being located in different distributed places.
Security is considered a major challenge with MCC environments. Mobile cloud security's issues are inherited from cloud computing, so we are at least familiar with those issues; however, those issues are more critical with MCC because of devices’ limited resource capacity (e.g., lack of CPU capability) to handle CPU-intensive malware detection applications that protect sensitive data, at least when compared to personal computers. The tenants’ worries are concentrated on the migration to the cloud of their data, which might face more risks once they share the same cloud resources with other tenants.[4] With MCC, cloud service providers offer the sharing of their resources to mobile users through the popular technique of virtualization, which increases the efficiency and effectiveness of hardware utilization.[5] Various users’ virtual machines are running on the same cloud host when they share the same cloud resources, which leads to additional security risks like violating data use terms once the data shares the same memory or CPU.[6][7] Consequently, an important question must be raised whether the other cloud virtual machines’ clients are trusted or not. Several robust security techniques have been proposed in this decade, and a number of new techniques or improved versions of the latest approaches have been developed. However, most of the solutions proposed are not practical due to the critical change—eliminating side channels and clocks, as well as the hypervisor—that comes with the cloud platform.[5] In this work, we aim to collect and present some relevant virtualization-based security techniques currently available in the field and review in detail the topic of various newly emerged security challenges.
The rest of this paper is organized as follows. Firstly, we present basic requirements of the virtualization techniques on MCC. We detail malicious attacks and briefly review quality measures. Then, we discuss the recent virtualization security techniques, with comparison and evaluation of different approaches also presented. Then, we present discussion, research gaps, and challenges concerning a security-based virtualization layer. Finally, in the last section, we conclude and present plans for future work.
Virtualization-based security preliminaries
In MCC, cloud services are provided for mobile users using virtualization technologies. Virtualization is defined as a middle layer between the software and hardware layers in a cloud server that allows the cloud provider to efficiently exploit their services and computing resources.[8] These resources can be shared among multiple virtual machines in order to run services simultaneously while also sharing benefits from available servers’ resources (e.g., CPU, network bandwidth, memory, etc.).[9] The virtualization process can reportedly increase hardware utilization (efficiency) between 60% and 80%.[10] The use of remote servers and other hardware utilization techniques also improves mobile device battery life by saving energy.[11][12]
The execution of mobile applications is considered a computationally intensive task that requires significant resource consumption on mobile devices. However, this kind of challenge has been defeated by the offloading technique. The computationally intensive application is divided into many tasks, which are migrated to the cloud (remote servers) for fast processing, with the results returned back to the mobile terminal afterwards.[13] On the cloud end, once the mobile task is offloaded, a virtual machine image of the mobile device (also called a "phone clone") is pre-installed for processing the mobile user’s application data, which increases the efficiency of the cloud environment and decreases the maintenance overhead on the mobile device.[4][14] Therefore, running the phone clone of the mobile device on the same server and isolating them is the main role of the virtualization technology. However, multiple works[5][6][15][16][17][18][19] have shown that virtualization has brought with it several security concerns[8] that affect virtualized systems, including denial-of-service (DOS) attacks. This kind of attack hits insipid information like workload statistics to know whether the system is vulnerable or not. Moreover, virtualization techniques on MCC brings new security risks such as unauthorized access from malicious virtual machines (VMs), VM-to-VM attacks, breaches of confidential mobile user data, VM monitoring challenges (e.g., the hypervisor), and communication challenges in a virtualized environment.[4][8] Thus, ensuring security mechanisms that prevent leakage of sensitive data and information from legitimate phone clones is not an easy task.
In terms of security, virtualization-based techniques are regrouped into two main categories: hardware-based techniques and software-based techniques. For the first class, we distinguish secure application cloning on VM[15] and the protection of VMs from a malicious hypervisor[20] as two useful techniques. For the second, we also consider two techniques: VM-based security techniques[16][17][18][21] and security techniques based on load balancing the VM.[5][19] Fig. 1 summarizes the important classes of virtualization-based security approaches.
|
Virtualization-based security techniques have five important proprieties[17][22]: efficiency, coverage, complexity, security, and robustness. Roughly speaking, efficiency represents the number of malicious VMs that succeed to co-locate with a target (victim VM), divided by the total number of VMs lunched by the attacker. Coverage represents the number of malicious VMs that succeed to co-locate with a target, divided by the number of targets lunched by a legitimate user. Complexity in security is defined as any secure complex technique that needs high execution time, high computation complexity, and high energy consumption from the cloud server. Security refers to the privacy of the VMs and their sensitive data, meaning that optimally no one would be able to remove or extract the data without knowing the secure key. Similarly, robustness refers to the degree of resistance against any kind of manipulation. Any new approach must negotiate a trade-off among these five proprieties.
Many researchers have begun developing frameworks, policies, and approaches against these kinds of challenges to ensure security for mobile users. These methods are mainly focused on how to ignore the side channel attacks between VMs while the malicious VMs access the cloud servers.[23][24][25][26] However, all the methods proposed require fundamental changes to the current commercial platform, and they are neither practical nor immediately deployable.[17] Additionally, while also strong candidates, hardware-based techniques lead to a high cost barrier.[15]
Virtualization-based security techniques
How to protect virtual machines (VM) and sensitive data is undoubtedly one of the most important topics regarding MCC. Recent security techniques have been used largely to tackle the security issues related to the virtualized environment in either cloud or mobile cloud computing.[5][15][16][17][18][19][20][21] This section discusses recent techniques described in the literature.
Virtualization-based security VM techniques
Hardware virtualization-based technique for securing application cloning on VM
Hao et al.[15] have presented a platform called Secure Mobile Cloud Platform (SMOC) for securing the mobile cloud environment. The platform allows the user to run their applications whether on the cloud or directly on the mobile device itself. In contrast, their proposed platform includes two concepts. The first one is sharing resources, which means that a mobile application can freely change the run-from location for providing a better user experience, i.e., not running explicitly on the cloud. This design provides more flexibility compared to other proposed approaches and techniques. The second concept is ensuring security even though the operating system of the mobile device has been attacked. A thin virtual machine shares its information and files with the mobile device once the mobile application is running in the cloud. Conversely, the mobile device shares its files and information (device inputs and outputs) with the VM-cloud for running the application. Despite the benefits of this platform towards security concerns, many assumptions are made by the researchers, who fail to consider issues with an untrusted hypervisor and untrusted public cloud provider. The proposed platform ensures data security and privacy only when both assumptions (hypervisor and cloud provider) are assured. Thus, this platform ensures security towards an untrusted guest operating system which also runs unsecure applications.
Encryption protocol-based virualization technique for trusting launch of VM
Paladi et al.[16] proposed a framework for data and transaction security of infrastructure services. The proposed framework contains various protocols for trust and the storage protection operation called Domain-Based Storage Protection (DBSP), as well as another protocol for trusting virtual machine deployment called TrustLunching. Trust VMs made a more suitable method when the virtual machines were running inside a trusted host using secure computing techniques. Their proposed solutions completed several attack-based security analyses, and the obtained results improved the robustness and the efficiency of their framework. Before the deployment of guest VMs, the protocol of trust VMs is performed. The second protocol used cryptography techniques outside the IaaS domain for ensuring the data confidentiality stored in the cloud. As such, a list of malicious host attacks against IaaS environments are demonstrated to produce both secure protocols. The proposed framework can be integrated into the existing cloud platform thanks to numerous successful experiments and tests run on tenants’ sensitive data (e.g., public healthcare patients’ data). However, this work focused specifically on attacks of IaaS platforms, which doesn't guarantee security for other threats such as hypervisor attacks, co-resident attacks, and so on.
VM allocation policy for defending co-residency attack
Frequently, VMs of different mobile users executed on the same physical host are logically isolated from each other. However, malevolent users can escape this logical isolation while sharing the same resources (CPU, memory, and cache) and capture sensitive and private information like crypto keys from co-resident virtual machines.[6][7] Han et al.[17] have proposed a new secure VM allocation policy called Previous Selected Servers First Policy (PSSF). (The algorithm is shown in Fig.2.) The aim of this policy is to defend against co-resident attack. However, the proposed algorithm lacks various security enhancements such as securing the mobile device VMs residing on it, live migration, and securing the communication data between the VMs while located on mobile devices and in the cloud. The algorithm also lacks a distributed application security algorithm deployment for mobile and the cloud. Finally, this algorithm only targets co-resident attacks and does not target other types of attacks like distributed VM communication attacks, hypervisor attacks, and mobile device data attacks.
|
Mechanism-based network measurement for detecting VMs co-residency
Yu et al.[18] have presented a new schema for detecting the VMs co-residency attacks by getting the location of the particular VM. The covert side channel is a kind of attack that breaks the isolation between the VMs, leading to the theft of sensitive information from users. To clarify more, the simple way to know whether two VMs are on the host is to rely on network metrics by performing TCP "traceroute" steps to get the IP address of the hypervisor. If two hypervisor IP addresses are the same, that means corresponding VMs are on the same host (co-resident). The advantage of this solution is that it increases the difficulty of establishing co-location. However, the attacker can still use other techniques to steal information from legitimate user VMs. As such, a simple hiding of the IP address of the hypervisor isn't sufficient to solve the co-residency issue.
Comparing the virtualization-based security techniques on VM
In Table 1, the above virtualization-based security techniques on VM are compared in terms of strengths and drawbacks.
| ||||||||||||||||||||||||
Virtualization-based load balancing security techniques on VM
Dynamic allocation and migration for phone clones for preventing covert channel attacks
Vaezpour et al.[19] have proposed a security scheme called the Security-aware Provisioning and Migration Scheme (SWAP) for provisioning and migrating thin virtual machines (phone clones) for preventing covert channel attacks.[19] This kind of attack is a constructed link between VMs where the CPU cache and the memory bus are exploited to steal information from legitimate phone clones in a virtualized environment.[6] The goal of their work is to reduce the risks of covert channel attacks when the cloud provider does not have enough resources to isolate the foreigner’s phone clones on the mobile cloud environment. Their proposed scheme includes two techniques. The first one is provisioning new phone clones, where this technique works, with mobile communication history to prevent users’ phone clone from hosting with other strangers’ thin virtual machine. The second technique involves migrating the phone clones from one host to another when the threat of attacks increases. The first and second algorithm is used to allocate the phone clones on the specified host by implementing various conditions. The algorithm is based on the communication history between the mobile users, where the virtual machines represent the node and communication between the virtual machines represent the edges. Thus, both algorithms allocate the phone clones based on communication history between the mobile users. The phone clones that have a communication link would not attack each other and may allocate in the same host. The third algorithm is for moving the phone clone from a host to another one in order to prevent the risks of retrieving the content of the phone clone from another adversary. The proposed solution has successfully kept few risks on phone clones compared with other proposed techniques. The main shortcoming of the proposed approach is that the researchers assumed that two phone clones on the same host cannot attack each other when they have a communication link between them. This work does not consider different scenarios (co-resident attacks, hypervisor attacks) which can produce several security threats on the phone.
Context-aware VM allocation policy for defending against co-resident attacks
Han et al.[5] have proposed an approach to minimize co-resident attacks in cloud environments. Their work improved the VM allocation policy—which extends the previously discuss PSSF tool[17]—with three additional policies: security, power consumption, and load balance to enhance the effectiveness and the efficiency of the cloud environment. Moreover, they applied several experiments on the simulation cloud platform CloudSim, and the obtained results showed a remarkable robustness against co-resident attacks. However, the authors have only studied one type of attack: a co-resident attack that occurred only on one host and not distributed on different hosts. They also did not consider migration attacks, which constitute serious risks on VMs and increase the possibility of co-locating with VM victims.
Comparing the virtualization-based load balancing security techniques on VM
In Table 2, the above virtualization-based load balancing techniques on VM are compared in terms of strengths and drawbacks.
| ||||||||||||||||
Virtualization-based security techniques on the hypervisor
Hardware-assisted secure VMs under a vulnerable hypervisor
Jin et al.[20] have proposed a new design for hardware-based VM protection. Their approach is called a Hardware-Assisted Secure Virtual Machine (H-SVM). The proposed mechanism protects the guest virtual machine for monitoring the malicious VM or hypervisor by isolating its memory virtualization. The authors have proposed a new flexible and efficient mechanism of memory protection by allowing restricted roles for the hypervisors and decoupling the memory isolation from memory allocation, which is usually executed by the hypervisor. Therefore, the handler (processor) takes some roles of the hypervisor such as scheduling VMs. The mechanism of changing the hardware architecture presents drawbacks regarding the deployment cost and proves unsuitable for immediate deployment.
Mechanism-based Linux kernel Mandatory Access Control (MAC) for securing VMs deployment
Liang et al.[21] have proposed an approach for securing VM deployment. Their approach reinforces the isolation among the virtual machines and controls the availability of resources by using a security system mechanism called Mandatory Access Control (MAC). MAC controls access to the various running processes. They used the hypervisor that is running on the server operating system to secure the isolation of guest VMs. In addition, they implemented a secure channel for migrating the VMs whenever risk threat heightens. Despite the benefits of the solution proposed, the authors have seemingly assumed that the hypervisor is trusted, with other studies proving that several crucial attacks may come from an untrusted hypervisor. Therefore, the authors do not give an evaluation that makes their solution more practical.
Comparing the virtualization-based security techniques on the hypervisor
In Table 3, the above virtualization-based techniques on the hypervisor are compared in terms of strengths and drawbacks.
| ||||||||||||||||
Virtualization-based security challenges
From the above three tables, it can be clearly seen that previous research on virtualization-based security has many limitations. First, such proposed solutions lack a mechanism that ensures the communication between VMs located on different servers. To clarify, researchers such as Han et al.[17] have a great idea in providing two metrics for measuring attacks (coverage and efficiency), yet they fail to consider the issues of data interaction between the VMs where an attacker can perform malicious activity while they communicate. Second, some solutions assume that the hypervisor is always protected unless the attacker can gain the control of the hypervisor, which directly controls the VMs. Finally, other solutions provide security using phone clones on the cloud side, but not on mobile devices.
To enhance security on mobile-based distributed applications using virtualization, we must take into consideration numerous challenging aspects of MCC: scalability, credibility, and robust communication techniques. Secure mobile distributed applications must address these three significant challenges to better perform in regards to VM security and data privacy.
1. Virtualization-based scalability: The problem with system overload is one of the main drivers for the construction of virtualization-based load balancing systems. To clarify, as the number of mobile users’ requests for services increases, the load-balancing problem becomes an even greater challenge. A personalized security system[5] enables the handling of virtual machines on a larger scale and intensive application management in cloud systems.
2. Virtualization-based credibility: The trustworthiness problem represents one of the great difficulties faced by security on MCC. The use of trust and information confidence on MCC allows making the cloud provider more reliable and capable to solve the problem of data credibility. Researchers such as Xu et al.[27] ensure the trustworthiness of a cloud system by finding the trust server, with a reputation value more than 0.8. According to their past feedback, this trust value enables mobile users to select the best offloading and solve security problems such as integrity and confidentiality.
3. Virtualization-based distributed VMs with robust encryption communication techniques: Mobile-based virtualization provides the capability of exploiting and managing distributed heterogeneous applications in the cloud. Virtualization techniques provide a resource sharing mechanism that protects the sensitive data dynamically by isolating any malicious user task. The core idea is directly stopping the attacker by passing on the cloud hypervisor and adapting advance virtualization-based hash techniques to preserve data integrity and confidentiality.
Conclusions and future work
With the appearance of new technologies, preserving the security and authenticity of mobile applications that exchange sensitive data becomes a fundamental and necessary requirement in the cloud environment. Over previous years, a number of different researchers have proposed various virtualization-based techniques, but each method has a number of associated advantages as well as drawbacks. To clarify, the user thin virtual machines communicate with each other to exchange private and sensitive information (e.g., a distrusted application executed on a different host). We have studied the limitations of most existing virtualization security co-location techniques proposed in the literature. As a result, we have identified that the main limitation is the absence of protecting sensitive information exchanged between mobile application’s tasks deployed on different VMs on the cloud. In future work, we will present a new approach that contains three secure policies to protect users' sensitive data against co-resident and hypervisor attacks, as well as preserve the communication of users' sensitive data when deployed on a different cloud host. Furthermore, we aim to provide for mobile users additional advantages such as detection of unauthorized access, hypervisor security control on sensitive data, and improved confidentiality during the exchange of sensitive data among VMs.
References
- ↑ Deng, M.; Petkovic, M.; Nalin, M. et al. (2011). "A Home Healthcare System in the Cloud--Addressing Security and Privacy Challenges". IEEE 4th International Conference on Cloud Computing: 549-556. doi:10.1109/CLOUD.2011.108.
- ↑ 2.0 2.1 Rahimi, M.R.; Rn, J.; Liu, C.H. et al. (2014). "Mobile Cloud Computing: A Survey, State of Art and Future Directions". Mobile Networks and Applications 19 (2): 133–43. doi:10.1007/s11036-013-0477-4.
- ↑ Zhang, Y.; Chen, X.; Li, J. et al. (2017). "Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing". Information Sciences 379: 42–61. doi:10.1016/j.ins.2016.04.015.
- ↑ 4.0 4.1 4.2 Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. (2017). "Security and privacy challenges in mobile cloud computing: Survey and way ahead". Journal of Network and Computer Applications 84: 38–54. doi:10.1016/j.jnca.2017.02.001.
- ↑ 5.0 5.1 5.2 5.3 5.4 5.5 5.6 5.7 Han, Y.; Chan, J.; Alpcan, T. et al. (2015). "Using Virtual Machine Allocation Policies to Defend against Co-Resident Attacks in Cloud Computing". IEEE Transactions on Dependable and Secure Computing 14 (1): 95–108. doi:10.1109/TDSC.2015.2429132.
- ↑ 6.0 6.1 6.2 6.3 Ristenpart, T.; Tromer, E.; Shacham, H. et al. (2009). "Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds". Proceedings of the 16th ACM Conference on Computer and Communications Security: 199–212. doi:10.1145/1653662.1653687.
- ↑ 7.0 7.1 Zhang, Y.; Juels, A.; Reiter, M.K. et al. (2012). "Cross-VM side channels and their use to extract private keys". Proceedings of the 2012 ACM Conference on Computer and Communications Security: 305–316. doi:10.1145/2382196.2382230.
- ↑ 8.0 8.1 8.2 Sgandurra, D.; Lupu, E. (2016). "Evolution of Attacks, Threat Models, and Solutions for Virtualized Systems". ACM Computing Surveys (CSUR) 48 (3): 46. doi:10.1145/2856126.
- ↑ Islam, M.; Rzzaque, A.; Hassan, M.H. et al. (2017). "Mobile Cloud-Based Big Healthcare Data Processing in Smart Cities". IEEE Access 5: 11887–11899. doi:10.1109/ACCESS.2017.2707439.
- ↑ Hu, F.; Qiu, M.; Li, J. et al. (2011). "A Review on Cloud Computing: Design Challenges in Architecture and Security". Journal of Computing and Information Technology 19 (1): 25–55. doi:10.2498/cit.1001864.
- ↑ Ellouze, A.; Gagnaire, M.; Haddad, A. (2015). "A Mobile Application Offloading Algorithm for Mobile Cloud Computing". Proceedings of the 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering: 34–40. doi:10.1109/MobileCloud.2015.11.
- ↑ Dhanya, N.M.; Kousalya, G. (2015). "Adaptive and Secure Application Partitioning for Offloading in Mobile Cloud Computing". SSCC 2015: International Symposium on Security in Computing and Communication: 45–53. doi:10.1007/978-3-319-22915-7_5.
- ↑ Shiraz, M.; Gani, A.; Jhokhar, R. et al. (2013). "A Review on Distributed Application Processing Frameworks in Smart Mobile Devices for Mobile Cloud Computing". IEEE Communications Surveys & Tutorials 15 (3): 1294–1313. doi:10.1109/SURV.2012.111412.00045.
- ↑ Sahoo, J.; Mohapatra, S.; Lath, R. (2010). "Virtualization: A Survey on Concepts, Taxonomy and Associated Security Issues". Second International Conference on Computer and Network Technology: 222–226. doi:10.1109/ICCNT.2010.49.
- ↑ 15.0 15.1 15.2 15.3 15.4 15.5 Hao, Z.; Tang, Y.; Zhang, Y. et al. (2015). "SMOC: A secure mobile cloud computing platform". 2015 IEEE Conference on Computer Communications: 2668-2676. doi:10.1109/INFOCOM.2015.7218658.
- ↑ 16.0 16.1 16.2 16.3 16.4 Paladi, N.; Gehrmann, C.; Michalas, A. (2017). "Providing User Security Guarantees in Public Infrastructure Clouds". IEEE Transactions on Cloud Computing 5: 405-419. doi:10.1109/TCC.2016.2525991.
- ↑ 17.0 17.1 17.2 17.3 17.4 17.5 17.6 17.7 17.8 17.9 Han, Y.; Chan, J.; Alpcan, T. et al. (2014). "Virtual machine allocation policies against co-resident attacks in cloud computing". 2014 IEEE International Conference on Communications: 786-792. doi:10.1109/ICC.2014.6883415.
- ↑ 18.0 18.1 18.2 18.3 18.4 Yu, S.; Xiaolin, G.; Jiancai, L. et al. (2013). "Detecting VMs Co-residency in Cloud: Using Cache-based Side Channel Attacks". Elektronika ir Elektrotechnika 19 (5): 73–78. doi:10.5755/j01.eee.19.5.2422.
- ↑ 19.0 19.1 19.2 19.3 19.4 19.5 Vaezpour, S.Y.; Zhang, R.; Wi, K. et al. (2016). "A new approach to mitigating security risks of phone clone co-location over mobile clouds". Journal of Network and Computer Applications 62: 171–184. doi:10.1016/j.jnca.2016.01.005.
- ↑ 20.0 20.1 20.2 20.3 Jin, S.; Ahn, J.; Seol, J. et al. (2015). "H-SVM: Hardware-Assisted Secure Virtual Machines under a Vulnerable Hypervisor". IEEE Transactions on Computers 64 (10): 2833–2846. doi:10.1109/TC.2015.2389792.
- ↑ 21.0 21.1 21.2 21.3 Liang, H.; Han, C.; Zhang, D. et al. (2015). "A Lightweight Security Isolation Approach for Virtual Machines Deployment". Inscrypt 2014: International Conference on Information Security and Cryptology: 516–529. doi:10.1007/978-3-319-16745-9_28.
- ↑ Suo, H.; Liu, Z.; Wan, J. et al. (2013). "Security and privacy in mobile cloud computing". Proceedings from the 9th International Wireless Communications and Mobile Computing Conference: 655–659. doi:10.1109/IWCMC.2013.6583635.
- ↑ Vattikonda, B.C.; Das, S.; Shacham, H. (2011). "Eliminating fine grained timers in Xen". Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop: 41–46. doi:10.1145/2046660.2046671.
- ↑ Wu, J.; Ding, L.; Lin, Y. et al. (2012). "XenPump: A New Method to Mitigate Timing Channel in Cloud Computing". IEEE Fifth International Conference on Cloud Computing: 678–685. doi:10.1109/CLOUD.2012.28.
- ↑ Aviram, A.; Hu, S.; Ford, B. et al. (2010). "Determinating timing channels in compute clouds". Proceedings of the 2010 ACM Workshop on Cloud Computing Security Workshop: 103–108. doi:10.1145/1866835.1866854.
- ↑ Shi, J.; Song, X.; Chen, H. et al. (2011). "Limiting cache-based side-channel in multi-tenant cloud using dynamic page coloring". IEEE/IFIP 41st International Conference on Dependable Systems and Networks Workshops: 194–199. doi:10.1109/DSNW.2011.5958812.
- ↑ Xu, D.; Fu, C.; Li, G. et al. (2017). "Virtualization of the Encryption Card for Trust Access in Cloud Computing". IEEE Access 5: 20652-20667. doi:10.1109/ACCESS.2017.2754515.
Notes
This presentation attempts to remain faithful to the original, with only a few minor changes to presentation. Grammar and punctuation has been updated reasonably to improve readability. In some cases important information was missing from the references, and that information was added. References appear in the order of the inline citations, by design.