Journal:Interoperability challenges in the cybersecurity information sharing ecosystem
| Full article title | Interoperability challenges in the cybersecurity information sharing ecosystem |
|---|---|
| Journal | Computers |
| Author(s) | Rantos, Konstantinos; Spyros, Arnolnt; Papanikolaou, Alexandros; Kritsas, Antonios; Ilioudis, Christos; Katos, Vasilios |
| Author affiliation(s) | International Hellenic University, Innovative Secure Technologies, Bournemouth University |
| Primary contact | Email: krantos at cs dot ihu dot gr |
| Year published | 2020 |
| Volume and issue | 9(1) |
| Article # | 18 |
| DOI | 10.3390/computers9010018 |
| ISSN | 2073-431X |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2073-431X/9/1/18/htm |
| Download | https://www.mdpi.com/2073-431X/9/1/18/pdf (PDF) |
|
|
This article should be considered a work in progress and incomplete. Consider this article incomplete until this notice is removed. |
Abstract
Threat intelligence helps businesses and organizations make the right decisions in their fight against cyber threats, and strategically design their digital defences for an optimized and up-to-date security situation. Combined with advanced security analysis, threat intelligence helps reduce the time between the detection of an attack and its containment. This is achieved by continuously providing information, accompanied by data, on existing and emerging cyber threats and vulnerabilities affecting corporate networks. This paper addresses challenges that organizations are bound to face when they decide to invest in effective and interoperable cybersecurity information sharing, and it categorizes them in a layered model. Based on this, it provides an evaluation of existing sources that share cybersecurity information. The aim of this research is to help organizations improve their cyber threat information exchange capabilities, to enhance their security posture and be more prepared against emerging threats.
Keywords: cyber threat information, cyber threat intelligence, interoperability, cybersecurity, evaluation
Introduction
Information has undoubtedly become one of the most valuable assets for organizations, whose dependence on it is constantly rising. At the same time, the frequency and ferocity of cyberattacks is also increasing, posing a great threat to business environments. According to a study conducted jointly by Ponemon Institute and Accenture, the average cost of cybercrime to organizations in 2018 rose to $13 million.[1] Moreover, 79% of chief information security officers (CISOs) in the banking sector believe that cybercriminals have become more sophisticated.[2]
In this constant battle of cybersecurity, organizations must remain cognizant of emerging and evolving threats and defend themselves against a wide range of adversaries with various levels of motivations, capabilities, and access to resources. These adversaries typically range from amateur hackers to well-organized and highly capable teams that have direct access to vulnerabilities and exploits, and therefore become advanced, and sometimes persistent, threats to organizations. The impact of such sophisticated, dynamic, and automated cyberattacks can be devastating.
Various businesses and organizations have recognized the need of being able to share cyber threat information (CTI) in a timely and reliable manner to enhance their ability to identify any malicious activity or sources and mitigate attacks in a timely manner, prior to damaging their assets. The National Institute of Standards and Technology (NIST) defines CTI as "any information that can help an organization identify, assess, monitor, and respond to cyber threats."[3] In a survey conducted by the SANS institute regarding the evolution of cyber threat information, 72% of survey respondents mentioned that in 2018 they had produced or consumed such information for their network defense.[4] The respective percentage for 2017 was 60%.[4] This demonstrates that information sharing is increasingly becoming part of an organization's strategy, and the number of them that join the sharing community is rising. The types of information that can be produced and shared among communities include, among others, security appliance log entries and alerts, measurable and observable actions, security bulletins and advisories, identified vulnerabilities, news, reports, and intelligent information.
The number of CTI sources is therefore increasing, as do cyber threat intelligence platforms capable of consuming information from threat intelligence feeds, analyzing, evaluating, and classifying it prior to sharing threat information with the community. Threat intelligence, according to Tounsi and Rais[5], means evidence-based knowledge representing threats that can inform decision-making. Cyber threat information and intelligence (CTII) facilitate situational awareness of the threat landscape, a deeper understanding of threat actors and their tactics, techniques, and procedures (TTPs), and greater agility to defend against evolving threats.
Nowadays, organizations have the ability to participate in such threat-sharing communities or intelligence groups, and analyze and evaluate CTII via their security operations team. Depending on the types of security appliances they are using, they can incorporate CTII into their security solutions, including measures such as unified threat management (UTM), intrusion detection/prevention systems (IDS/IPS), and security information and event mnagement (SIEM). IT security vendors and service providers also collect such information from their clients worldwide, analyze it, and feed it back to the deployed security appliances, thus gaining from the experience of their community. Analysis and evaluation of such information is considered essential, as sometimes the information that is shared is not properly filtered or checked.
Using unreliable sources poses risks to organizations, as the information may not be accurate or complete. To confront this undesired situation, organizations go beyond closed groups and use multiple sources instead. As such, CTII sharing takes place among multiple actors, such as government agencies and organizations, private sector organizations, and industry-based focus groups. One of the most challenging issues in this process is achieving consensus regarding how this information should be shared among interested parties and the threat intelligence community. This requires having a common understanding on what information is shared, how it is shared, and whether sharing of such information is legal.
This paper addresses the interoperability challenges that businesses and organizations face when adopting specific sharing solutions. These challenges mainly stem from the adoption of multiple technical standards, strategies, and policies among stakeholders, together with legal restrictions concerning information sharing. The aim of this work is to highlight points that impede the wide adoption of cybersecurity information sharing and the much-needed automation of the sharing process.[4] Security analysts would benefit from such automation, as they could devote more time on analyzing collected interoperable data, as opposed to devoting their efforts on the collection process itself. Interoperability is also a means to widen the CTII sharing spectrum and engage more stakeholders in the exchange process, thus developing a global shield against emerging threats, with significant benefits for the community.
Background
Cybersecurity information exchange (CIE) concerns sharing CTII with third parties to help organizations enhance their security posture and protect themselves from cyber threats. The main motive is to create new knowledge or services about cyber threats, as well as to make cyber-defence systems more effective and efficient.
CTI can be sometimes directly imported to security appliances, e.g., IP addresses reported as malicious can be directly imported to firewalls and IDS/IPS, to speed up the organization’s reaction to a potential threat. This, however, may come at the cost of introducing many false positives as, after an in-depth analysis and evaluation, these IPs may prove to be non-malicious. Therefore, prior to becoming a valuable asset for the organization, cyber threat information has to be properly collected from various sources, correlated, analyzed, and evaluated to add significant value to the raw and/or unevaluated data, thus producing the so-called “cyber threat intelligence.” Analyzed information significantly reduces false positives and establishes trust on the various sources it comes from. The downside of this process is the delay introduced to information sharing, due to the time-consuming analysis of, e.g., big data as well as other techniques, like threat sandboxing, which is used for monitoring the behavior of suspicious targets.
The cooperation among organizations in the E.U. and the publication of detected security incidents are also encouraged, although there are also cases where they are obligatory, as stated in E.U. Directive 2016/1148 on the security of network and information systems.[6] Implementation guidance for meeting the requirements of that directive is provided by ETSI.[7] In this context, a computer security incident response team (CSIRT; also known as computer emergency response team or CERT) network has been established, which counts more than 400 members willing to share incidents and risk-related information (an inventory of the E.U.'s CSIRT network members is maintained by ENISA[8]). The network, however, is not restricted only to CSIRTs, but also includes commercial organizations, E.U. institutions, law enforcement agencies, private- and public-sector organizations, and national and military agencies.
Similar initiatives in the U.S. that promote the exchange of information include the U.S. Department of Homeland Security (DHS) Cyber Information Sharing and Collaboration Program (CISCP)[9] and its Automated Indicator Sharing (AIS) capability.[10]
Examples of such shareable information include the following:
- indicators of compromise (IOCs), i.e., system artifacts or observables that contain patterns, such as malicious Internet Protocol addresses (IPs) or hashes of files containing malware, which can help identify suspicious or malicious activity;
- tactics, techniques, and procedures (TTPs), i.e., (detailed) descriptions of the behavior of an actor that can assist operational activities, such as details of exploits and malware delivery mechanisms (examples include tradecrafts, i.e., behaviour used to conduct a malicious activity, infrastructure used to deliver malicious content or maintain command and control capabilities, and attackers’ intentions[11]);
- security alerts, i.e., notifications—usually human-readable—regarding security issues, such as vulnerabilities;
- threat intelligence reports, i.e., collections of threat intelligence for various topics, such as threat actors, malware, and attack techniques;
- recommended security tool configurations, regarding automated collection and processing as well as healing of identified security issues; and
- vulnerabilities, i.e., known weaknesses in software implementations or procedures, and corresponding mitigations, such as security patches (although in the information security literature, vulnerabilities are not threats, they are considered an important component in the CTII sharing ecosystem).
The U.K. National Computer Emergency Response Team CERT-UK, together with the U.K.’s Centre for the Protection of National Infrastructure, define four subtypes of threat intelligence in a whitepaper published by MWR Infosecurity.[12] A similar categorization is also adopted by ENISA.[13] Based on the two schemes, stakeholders exchange information of one of the following types:
- strategic reports providing high-level threat analyses that are consumed at board level or by other senior decision-makers;
- operational details providing information about impending attacks against an organization;
- advisories which include vulnerabilities, exploits, patches and patch statuses, or high-level tactical patterns of activity on host-, service-, network-, or internet-level tools and methodologies;
- indicators of compromise, which include IP addresses, DNS names, URLs, specific values of format-specific fields (e.g., email headers), artifacts (e.g., hashes, registries, and keys) related to malware and sequences of low-level events (e.g., syscalls and packets) linked to malicious behavior; and
- low-level activity, i.e., network flow records and full packet captures, application logs, including typical IDS alerts, samples of executable files, documents, and email messages.
Depending on the type of information that is being shared, organizations have the capability for prompt reaction, as a response to newly-emerged threats or vulnerabilities, for properly adapting their security defenses against changes in their situational awareness at a more tactical level, while making more strategic decisions on the allocation of their resources for upcoming threats.
Tounsi and Rais[5] classify and distinguish existing threat intelligence types, focusing on technical threat intelligence issues, emerging research, trends, and standards. They also explain why there is a reluctance among organizations to share threat intelligence, while also providing sharing strategies that can help overcome policy interoperability issues. Following a layered model, Burger et al.[14] propose a taxonomy to help classify existing threat-sharing standards and analyze interoperability. However, the five layers proposed by the authors do not address legal or semantic issues that are analyzed in this paper.
So far, although CTII sharing is identified in the literature as an important issue, it is treated as a problem that can be solved with the adoption of some technical standards.[3][14][15] To the best of the authors’ knowledge, no work has been published so far detailing a holistic approach to the interoperability problem of CTII sharing.
Interoperable CTII sharing
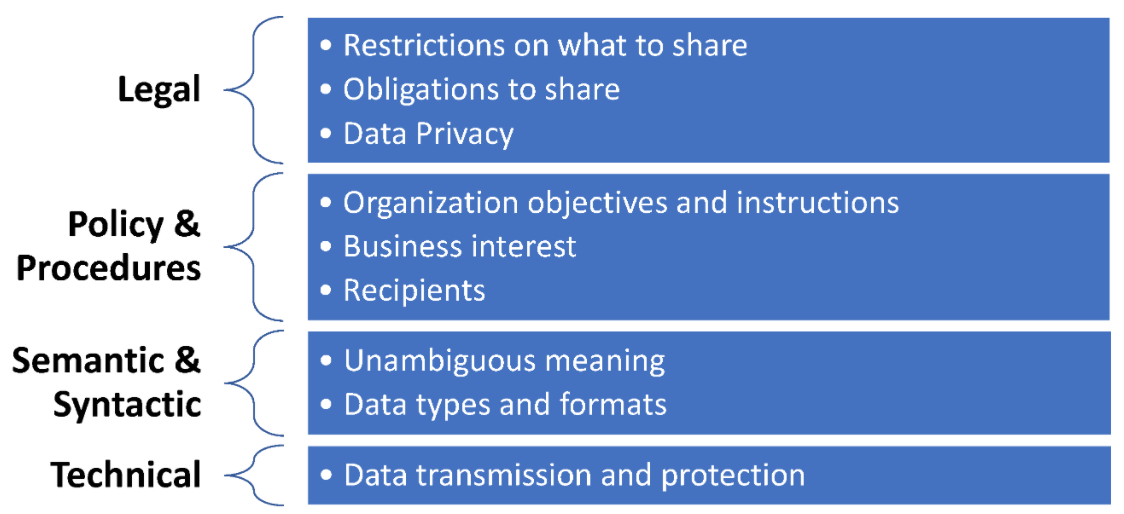
Cyber threat information and intelligence (CTII) information is generated and shared among devices and organizations that typically have well-established procedures to appropriately handle [[Information privacy|personal] and classified information found within. When CTII is about to be shared, especially with external entities, several interoperability and security issues have to be confronted. These issues can be categorized into the four layers depicted in Figure 1, further analyzed in the following sections.
|
3.1. Legal interoperability
Legal interoperability is about ensuring that the legal frameworks under which organizations operate and provide services are aligned and do not impede the sharing of CTII. Legal frameworks open up the potential for improving the collaboration among public–private organizations and may encourage or require the sharing of cyber threat information. Examples of such frameworks are the E.U.’s NIS Directive[6] and the U.S. Cybersecurity Information Sharing Act (CISA) of 2015.
Legal constraints may also prohibit or restrict the uncontrolled sharing of CTII. Examples of the latter are any personally identifiable information (PII) that may be part of the shared sightings, such as usernames of entities that have been identified as sources of malicious activity and restrictions that stem from the corresponding telecommunications privacy legal framework. One of the main legal restrictions arises from the E.U.'s General Data Protection Regulation (GDPR)[16] and relates to any PII shared with external entities without the user’s consent. CTII sharing with external entities should not impact privacy, and sharing parties must take measures to properly anonymize or pseudonymize any records of data that could otherwise be used to identify individuals.
Liability is another key factor that has to be considered when sharing information. Organizations have to take into account that they may be liable for any damage caused to stakeholders or entities that appear to be threat actors, by sharing information that may prove inaccurate or false. For instance, what would happen if an IDS/IPS falsely identified some malicious activity coming from a popular website and this was immediately reported to sharing parties?
Legal interoperability is even more important when data sharing spans multiple countries or legal domains. Therefore, restrictions imposed by each such domain must be carefully reviewed prior to information dissemination. The organization has to establish boundaries on any sharing activities so that these will not infringe on any legal restrictions.
As such, legal interoperability requires visibility control over CTII. The organization has to have the means to perform deep inspection on what is practically going to be shared to identify any information that may cross the well-established boundaries regarding information sharing, and this should be reflected to the policies and procedures adopted by the organization.
3.2. Policies and procedures for interoperability
An organization's information sharing policies and procedures are formal statements that reflect its objectives and detailed instructions to achieve these objectives respectively. They are typically part of the organization’s information security policy and have to be endorsed by the organization’s top management.
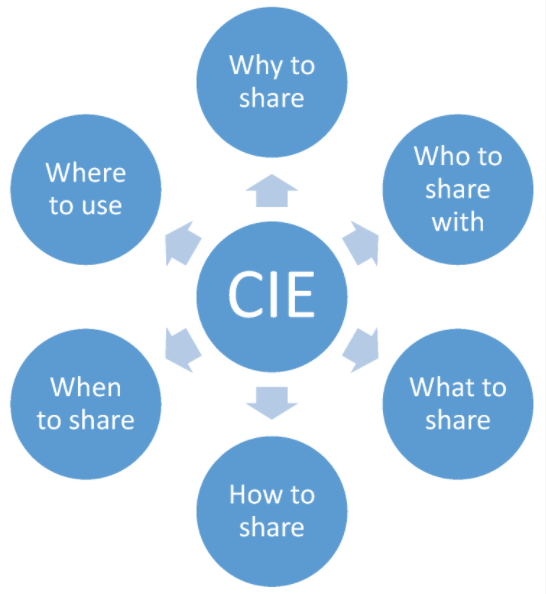
Among the issues that the organization has to consider at the policy layer when deciding to share CTII are the five "Ws" and one "H" that have to be answered prior to sharing, as depicted in Figure 2. The policy should clearly address them, while well-established procedures and appropriate robust measures will properly support them to avoid policy violations, such as the leakage of classified or sensitive information. Therefore, to ensure that the security and privacy posture of the organisation is not negatively affected by the introduction of CTII sharing, the service’s risk analysis should address the threats that are associated with the exchange of CTII with third parties and the consumption of the received information. The deployed security measures that will protect CTII and ensure that this is handled only by authenticated and authorized entities will minimise the associated risks.
|
References
- ↑ Accenture, Ponemon Institute (2019). "The Cost of Cybercrime" (PDF). Accenture. https://www.accenture.com/_acnmedia/pdf-96/accenture-2019-cost-of-cybercrime-study-final.pdf. Retrieved 03 March 2020.
- ↑ Kellermann, T. (5 March 2019). "Modern Bank Heists: The Bank Robbery Shifts to Cyberspace". Carbon Black. VMware, Inc. https://www.carbonblack.com/blog/modern-bank-heists-the-bank-robbery-shifts-to-cyberspace/. Retrieved 03 March 2020.
- ↑ 3.0 3.1 Johnson, C.; Badger, L.; Waltermire, D. et al. (October 2016). "Guide to Cyber Threat Information Sharing" (PDF). NIST Special Publication 800-150. National Institute of Standards and Technology. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-150.pdf. Retrieved 03 March 2020.
- ↑ 4.0 4.1 4.2 Brown, R.; Lee, R.M. (4 February 2019). "The Evolution of Cyber Threat Intelligence (CTI): 2019 SANS CTI Survey". The SANS Institute. https://www.sans.org/reading-room/whitepapers/threats/paper/38790. Retrieved 03 March 2020.
- ↑ 5.0 5.1 Tounsi, W.; Rais, H. (2018). "A survey on technical threat intelligence in the age of sophisticated cyber attacks". Computers & Security 72: 212–33. doi:10.1016/j.cose.2017.09.001.
- ↑ 6.0 6.1 "Directive (EU) 2016/1148 of the European Parliament and of the Council of 6 July 2016 concerning measures for a high common level of security of network and information systems across the Union". EUR-Lex. European Union. 6 July 2016. https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32016L1148&qid=1603749013818. Retrieved 03 March 2020.
- ↑ ETSI (October 2017). "CYBER; Implementation of the Network and Information Security (NIS) Directive" (PDF). ETSI TR 103 456 V1.1.1. https://www.etsi.org/deliver/etsi_tr/103400_103499/103456/01.01.01_60/tr_103456v010101p.pdf. Retrieved 03 March 2020.
- ↑ European Union Agency for Cybersecurity. "CSIRTs in Europe". https://www.enisa.europa.eu/topics/csirts-in-europe/csirt-inventory. Retrieved 03 March 2020.
- ↑ Cybersecurity & Infrastructure Security Agency. "Cyber Information Sharing and Collaboration Program (CISCP)". U.S. Department of Homeland Security. https://www.cisa.gov/ciscp. Retrieved 03 March 2020.
- ↑ Cybersecurity & Infrastructure Security Agency. "Automated Indicator Sharing". U.S. Department of Homeland Security. https://www.cisa.gov/automated-indicator-sharing-ais. Retrieved 03 March 2020.
- ↑ Office of the Director of National Intelligence (14 September 2018). "A Guide to Cyber Attribution" (PDF). https://www.dni.gov/files/CTIIC/documents/ODNI_A_Guide_to_Cyber_Attribution.pdf. Retrieved 03 March 2020.
- ↑ Chismon, D.; Ruks, M. (2015). "Threat Intelligence: Collecting, Analyzing, Evaluating" (PDF). MWR InfoSecurity Ltd. https://www.foo.be/docs/informations-sharing/Threat-Intelligence-Whitepaper.pdf. Retrieved 03 March 2020.
- ↑ ENISA (November 2014). "Actionable Information for Security Incident Response" (PDF). https://www.enisa.europa.eu/publications/actionable-information-for-security/at_download/fullReport. Retrieved 03 March 2020.
- ↑ 14.0 14.1 Burger, E.W.; Goodman, M.D.; Kampanakis, P. et al. (2014). "Taxonomy Model for Cyber Threat Intelligence Information Exchange Technologies". WISCS '14: Proceedings of the 2014 ACM Workshop on Information Sharing & Collaborative Security: 51–60. doi:10.1145/2663876.2663883.
- ↑ Skopik, F.; Settanni, G.; Fiedler, R. (2016). "A problem shared is a problem halved: A survey on the dimensions of collective cyber defense through security information sharing". Computers & Security 60: 154–76. doi:10.1016/j.cose.2016.04.003.
- ↑ "Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation)". EUR-Lex. European Union. 27 April 2016. https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX%3A32016R0679. Retrieved 03 March 2020.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added.