Difference between revisions of "Journal:CustodyBlock: A distributed chain of custody evidence framework"
Shawndouglas (talk | contribs) (Saving and adding more.) |
Shawndouglas (talk | contribs) (Finished adding rest of content.) |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 19: | Line 19: | ||
|download = [https://www.mdpi.com/2078-2489/12/2/88/pdf?version=1614304317 https://www.mdpi.com/2078-2489/12/2/88/pdf] (PDF) | |download = [https://www.mdpi.com/2078-2489/12/2/88/pdf?version=1614304317 https://www.mdpi.com/2078-2489/12/2/88/pdf] (PDF) | ||
}} | }} | ||
==Abstract== | ==Abstract== | ||
With the increasing number of cybercrimes, the [[digital forensics]] team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of [[information]] that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient [[wikipedia:Evidence management|evidence management]] to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate [[chain of custody]] (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private [[blockchain]] protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed. | With the increasing number of cybercrimes, the [[digital forensics]] team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of [[information]] that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient [[wikipedia:Evidence management|evidence management]] to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate [[chain of custody]] (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private [[blockchain]] protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed. | ||
| Line 32: | Line 25: | ||
==Introduction== | ==Introduction== | ||
[[wikipedia:Evidence management|Evidence management]] is one of the most important problems in [[digital forensics]]. Digital proof plays a vital role in crime investigations because it is used to link persons with their criminal activities. [[Chain of custody]] (CoC) in digital forensics can be defined as a process of documenting and maintaining the chronological history of handling digital evidence. | [[wikipedia:Evidence management|Evidence management]] is one of the most important problems in [[digital forensics]]. Digital proof plays a vital role in crime investigations because it is used to link persons with their criminal activities. [[Chain of custody]] (CoC) in digital forensics can be defined as a process of documenting and maintaining the chronological history of handling digital evidence.<ref>{{Cite journal |last=Adam |first=Iliyasu Yahaya |last2=Varol |first2=Cihan |date=2020-06 |title=Intelligence in Digital Forensics Process |url=https://ieeexplore.ieee.org/document/9116442/ |journal=2020 8th International Symposium on Digital Forensics and Security (ISDFS) |publisher=IEEE |place=Beirut, Lebanon |pages=1–6 |doi=10.1109/ISDFS49300.2020.9116442 |isbn=978-1-7281-6939-2}}</ref><ref name=":1">{{Cite journal |last=Giova, G. |year=2011 |title=Improving Chain of Custody in Forensic Investigation of Electronic Digital Systems |url=http://paper.ijcsns.org/07_book/html/201101/201101001.html |journal=International Journal of Computer Science and Network Security |volume=11 |issue=1 |pages=1–9}}</ref> This plays an important role in the investigation of digital forensics because it notes every detail of concern to digital evidence through different levels of hierarchy. This goes from the first responder to the higher authorities who were responsible for handling the investigation of cybercrime. | ||
Digital proof comes with its own particular challenges, particularly when linked with the CoC. Blockchain technology can enable various stages of digital transaction to take place, however, providing massive advantages for the forensic community. In general, blockchain can act as a scattered form of [[information]] that maintains tamper-proof arrangement blocks that hold a cluster of individual transactions. It executes a decentralized and fully replicated append-only ledger, present in a peer-to-peer network, originally deployed for the bitcoin cryptocurrency. All the nodes present on the chain maintain a complete local copy of the blockchain. The blockchain is an indigenous technology that has emerged for decentralized applications, the outcome of complicated privacy and security issues present in applications for over half a century. | Digital proof comes with its own particular challenges, particularly when linked with the CoC. Blockchain technology can enable various stages of digital transaction to take place, however, providing massive advantages for the forensic community. In general, blockchain can act as a scattered form of [[information]] that maintains tamper-proof arrangement blocks that hold a cluster of individual transactions. It executes a decentralized and fully replicated append-only ledger, present in a peer-to-peer network, originally deployed for the bitcoin cryptocurrency. All the nodes present on the chain maintain a complete local copy of the blockchain. The blockchain is an indigenous technology that has emerged for decentralized applications, the outcome of complicated privacy and security issues present in applications for over half a century.<ref>{{Cite journal |last=Bali |first=Jatinder |last2=Garg |first2=Rohit |last3=Bali |first3=RenuT |date=2019 |title=Artificial intelligence (AI) in healthcare and biomedical research: Why a strong computational/AI bioethics framework is required? |url=https://journals.lww.com/10.4103/ijo.IJO_1292_18 |journal=Indian Journal of Ophthalmology |language=en |volume=67 |issue=1 |pages=3 |doi=10.4103/ijo.IJO_1292_18 |issn=0301-4738 |pmc=PMC6324122 |pmid=30574881}}</ref><ref name=":0">{{Cite journal |last=Sabir |first=B. E. |last2=Youssfi |first2=M. |last3=Bouattane |first3=O. |last4=Allali |first4=H. |date=2020-04-04 |title=Towards a New Model to Secure IoT-based Smart Home Mobile Agents using Blockchain Technology |url=https://etasr.com/index.php/ETASR/article/view/3394 |journal=Engineering, Technology & Applied Science Research |volume=10 |issue=2 |pages=5441–5447 |doi=10.48084/etasr.3394 |issn=1792-8036}}</ref> It is a peer-to-peer system that authorizes users to maintain a ledger for various transactions that are reproduced, and it remains identical in more than one location over multiple user servers.<ref>{{Cite journal |last=Zheng |first=Zibin |last2=Xie |first2=Shaoan |last3=Dai |first3=Hong Ning |last4=Chen |first4=Xiangping |last5=Wang |first5=Huaimin |date=2018 |title=Blockchain challenges and opportunities: a survey |url=http://www.inderscience.com/link.php?id=95647 |journal=International Journal of Web and Grid Services |language=en |volume=14 |issue=4 |pages=352–75 |doi=10.1504/IJWGS.2018.095647 |issn=1741-1106}}</ref> | ||
A blockchain is essentially a "block of chains," with the growing list of records that come from it referred to as "blocks" that are joined with [[Encryption|cryptography]]. | A blockchain is essentially a "block of chains," with the growing list of records that come from it referred to as "blocks" that are joined with [[Encryption|cryptography]].<ref name=":0" /> Each blockchain contains a hash of a previous block, and a timestamp that keeps track of the creation and modification time of a document. In terms of security, nobody, not even the owners of the document, ought to be able to modify it once it has been recorded (this can be done only if the integrity of time-stampers is compromised, which is rare). Blockchain was invented in 2008 and implemented in 2009 to function in the general public ledger of the Bitcoin cryptocurrency, a type of electronic money. Blockchain technology is decentralized (i.e., peer-to-peer). It consists of world network computers, which apply blockchain technology to put together and manage the information that records each Bitcoin transaction managed by its network. The architecture of blockchain technology, shown in Figure 1, implements a decentralized, fully replicated append-only ledger in a peer-to-peer network.<ref name=":2">{{Cite journal |last=Zhang |first=Yu |last2=Wen |first2=Jiangtao |date=2017-07 |title=The IoT electric business model: Using blockchain technology for the internet of things |url=http://link.springer.com/10.1007/s12083-016-0456-1 |journal=Peer-to-Peer Networking and Applications |language=en |volume=10 |issue=4 |pages=983–994 |doi=10.1007/s12083-016-0456-1 |issn=1936-6442}}</ref> | ||
| Line 50: | Line 43: | ||
|} | |} | ||
The methodology proposed in this paper uses IBM's Hyperledger blockchain technology, as it is private and open-source. Hyperledger supports smart contracts called chaincodes. | The methodology proposed in this paper uses IBM's Hyperledger blockchain technology, as it is private and open-source. Hyperledger supports smart contracts called chaincodes.<ref name=":3">{{Cite journal |last=Ramezan |first=Gholamreza |last2=Leung |first2=Cyril |date=2018-11-01 |title=A Blockchain-Based Contractual Routing Protocol for the Internet of Things Using Smart Contracts |url=https://www.hindawi.com/journals/wcmc/2018/4029591/ |journal=Wireless Communications and Mobile Computing |language=en |volume=2018 |pages=1–14 |doi=10.1155/2018/4029591 |issn=1530-8669}}</ref> Hyperledger is able to approve blocks and send the associated exchange transactions to the trusted and approved blocks to be validated and approved.<ref>{{Cite journal |last=Bozic |first=Nikola |last2=Pujolle |first2=Guy |last3=Secci |first3=Stefano |date=2016-12 |title=A tutorial on blockchain and applications to secure network control-planes |url=http://ieeexplore.ieee.org/document/7870552/ |journal=2016 3rd Smart Cloud Networks & Systems (SCNS) |publisher=IEEE |place=Dubai, United Arab Emirates |pages=1–8 |doi=10.1109/SCNS.2016.7870552 |isbn=978-1-5090-4476-4}}</ref> This is the most broadly utilized blockchain stage, utilized across various ventures and use-cases. It is utilized in a few models and proof-of-concepts, and is also being disseminated in record frameworks. | ||
Hyperledger is a blockchain with pluggable agreement. It is one of the more favorable uses of Hyperledger, which is hosted by the Linux Foundation. It is the first blockchain framework that permits the execution of dispersed applications written in standard programming. While generic blockchain utilizes request–execute–approve engineering, Hyperledger uses an execute–request–approve design and a support strategy that is overseen by assigned directors and functions as a static library for exchange approval. | Hyperledger is a blockchain with pluggable agreement. It is one of the more favorable uses of Hyperledger, which is hosted by the Linux Foundation. It is the first blockchain framework that permits the execution of dispersed applications written in standard programming. While generic blockchain utilizes request–execute–approve engineering, Hyperledger uses an execute–request–approve design and a support strategy that is overseen by assigned directors and functions as a static library for exchange approval.<ref>{{Cite journal |last=Pavithran |first=Deepa |last2=Shaalan |first2=Khaled |last3=Al-Karaki |first3=Jamal N. |last4=Gawanmeh |first4=Amjad |date=2020-09 |title=Towards building a blockchain framework for IoT |url=http://link.springer.com/10.1007/s10586-020-03059-5 |journal=Cluster Computing |language=en |volume=23 |issue=3 |pages=2089–2103 |doi=10.1007/s10586-020-03059-5 |issn=1386-7857}}</ref> | ||
Blockchain technology also provides decentralization, tracking, data transparency, security, and privacy for [[internet of things]] (IoT) applications. | Blockchain technology also provides decentralization, tracking, data transparency, security, and privacy for [[internet of things]] (IoT) applications.<ref>{{Cite journal |last=Yang |first=Wenli |last2=Aghasian |first2=Erfan |last3=Garg |first3=Saurabh |last4=Herbert |first4=David |last5=Disiuta |first5=Leandro |last6=Kang |first6=Byeong |date=2019 |title=A Survey on Blockchain-Based Internet Service Architecture: Requirements, Challenges, Trends, and Future |url=https://ieeexplore.ieee.org/document/8717702/ |journal=IEEE Access |volume=7 |pages=75845–75872 |doi=10.1109/ACCESS.2019.2917562 |issn=2169-3536}}</ref> IoT applications running in medical, transportation, agriculture, and other contexts require a high level of security. Blockchain provides the necessary security and privacy for different IoT applications and transactions, while maintaining a high level of integrity. Additionally, blockchain provides a high level of management for IoT systems by using privileged digital identities and access management.<ref>{{Citation |last=Mamdouh |first=Moustafa |last2=Awad |first2=Ali Ismail |last3=Hamed |first3=Hesham F. A. |last4=Khalaf |first4=Ashraf A. M. |date=2020 |editor-last=Hassanien |editor-first=Aboul-Ella |editor2-last=Azar |editor2-first=Ahmad Taher |editor3-last=Gaber |editor3-first=Tarek |editor4-last=Oliva |editor4-first=Diego |editor5-last=Tolba |editor5-first=Fahmy M. |title=Outlook on Security and Privacy in IoHT: Key Challenges and Future Vision |url=http://link.springer.com/10.1007/978-3-030-44289-7_67 |work=Proceedings of the International Conference on Artificial Intelligence and Computer Vision (AICV2020) |language=en |publisher=Springer International Publishing |place=Cham |volume=1153 |pages=721–730 |doi=10.1007/978-3-030-44289-7_67 |isbn=978-3-030-44288-0 |accessdate=2022-06-28}}</ref> Many researchers illustrate the importance of connecting IoT systems to a blockchain-based technology to enhance the level of security and IoT performance.<ref>{{Cite journal |last=Ernest |first=Bonnah |last2=Shiguang |first2=Ju |date=2020 |title=Privacy Enhancement Scheme (PES) in a Blockchain-Edge Computing Environment |url=https://ieeexplore.ieee.org/document/8966296/ |journal=IEEE Access |volume=8 |pages=25863–25876 |doi=10.1109/ACCESS.2020.2968621 |issn=2169-3536}}</ref><ref>{{Cite journal |last=Kim |first=Hyunil |last2=Kim |first2=Seung-Hyun |last3=Hwang |first3=Jung Yeon |last4=Seo |first4=Changho |date=2019 |title=Efficient Privacy-Preserving Machine Learning for Blockchain Network |url=https://ieeexplore.ieee.org/document/8827509/ |journal=IEEE Access |volume=7 |pages=136481–136495 |doi=10.1109/ACCESS.2019.2940052 |issn=2169-3536}}</ref><ref name=":4">{{Cite journal |last=Liu |first=Wenzheng |last2=Wang |first2=Xiaofeng |last3=Peng |first3=Wei |date=2020 |title=Secure Remote Multi-Factor Authentication Scheme Based on Chaotic Map Zero-Knowledge Proof for Crowdsourcing Internet of Things |url=https://ieeexplore.ieee.org/document/8945237/ |journal=IEEE Access |volume=8 |pages=8754–8767 |doi=10.1109/ACCESS.2019.2962912 |issn=2169-3536}}</ref> | ||
In the context of digital forensics, the production of evidence in the modern digital world is a complex task. For this reason, we consider it essential that digital evidence should be accepted as valid in court only if the CoC can assure exactly what the evidence is, why it was collected and analyzed, and how evidentiary data were collected, analyzed, and reported. This can be in the form of big data. | In the context of digital forensics, the production of evidence in the modern digital world is a complex task. For this reason, we consider it essential that digital evidence should be accepted as valid in court only if the CoC can assure exactly what the evidence is, why it was collected and analyzed, and how evidentiary data were collected, analyzed, and reported. This can be in the form of big data.<ref>{{Cite journal |last=Alfandi |first=Omar |last2=Otoum |first2=Safa |last3=Jararweh |first3=Yaser |date=2020-04 |title=Blockchain Solution for IoT-based Critical Infrastructures: Byzantine Fault Tolerance |url=https://ieeexplore.ieee.org/document/9110312/ |journal=NOMS 2020 - 2020 IEEE/IFIP Network Operations and Management Symposium |publisher=IEEE |place=Budapest, Hungary |pages=1–4 |doi=10.1109/NOMS47738.2020.9110312 |isbn=978-1-7281-4973-8}}</ref><ref name=":5">{{Cite journal |last=Khan |first=Z. Faizal |last2=Alotaibi |first2=Sultan Refa |date= |year=2020 |title=Applications of Artificial Intelligence and Big Data Analytics in m-Health: A Healthcare System Perspective |url=https://www.hindawi.com/journals/jhe/2020/8894694/ |journal=Journal of Healthcare Engineering |language=en |volume=2020 |pages=8894694 |at= |doi=10.1155/2020/8894694 |issn=2040-2295 |pmc=PMC7481991 |pmid=32952992}}</ref> Additionally, the CoC must demonstrate exactly where, when, and who came into contact with the electronic evidence in each stage of an investigation, as well as any manipulation of the evidence.<ref name=":6">{{Cite journal |last=Jabareen |first=Yosef |date=2009-12 |title=Building a Conceptual Framework: Philosophy, Definitions, and Procedure |url=http://journals.sagepub.com/doi/10.1177/160940690900800406 |journal=International Journal of Qualitative Methods |language=en |volume=8 |issue=4 |pages=49–62 |doi=10.1177/160940690900800406 |issn=1609-4069}}</ref><ref>{{Cite journal |last=Singh |first=Kumar Shanu |last2=Irfan |first2=Annie |last3=Dayal |first3=Neelam |date=2019-11 |title=Cyber Forensics and Comparative Analysis of Digital Forensic Investigation Frameworks |url=https://ieeexplore.ieee.org/document/9036214/ |journal=2019 4th International Conference on Information Systems and Computer Networks (ISCON) |publisher=IEEE |place=Mathura, India |pages=584–590 |doi=10.1109/ISCON47742.2019.9036214 |isbn=978-1-7281-3651-6}}</ref> The increasing complexity of [[forensic science]] in the digital area leads researchers to claim that traditional computer forensics “is on the edge of a precipice,” especially because of the great diversity of electronic devices to be examined and the intensive growth of the quantity of data that must be collected and examined during preservation in the blockchain.<ref>{{Cite journal |last=Sun |first=Xia |last2=Zou |first2=Jinglin |last3=Li |first3=Li |last4=Luo |first4=Min |date=2021-02 |title=A blockchain-based online language learning system |url=https://link.springer.com/10.1007/s11235-020-00699-1 |journal=Telecommunication Systems |language=en |volume=76 |issue=2 |pages=155–166 |doi=10.1007/s11235-020-00699-1 |issn=1018-4864}}</ref><ref name=":7">{{Cite journal |last=Tiwari |first=V. |last2=Keskar |first2=A. |last3=Shivaprakash |first3=N. C. |date=2017-04-24 |title=Design of an IoT Enabled Local Network Based Home Monitoring System with a Priority Scheme |url=https://etasr.com/index.php/ETASR/article/view/1033 |journal=Engineering, Technology & Applied Science Research |volume=7 |issue=2 |pages=1464–1472 |doi=10.48084/etasr.1033 |issn=1792-8036}}</ref> This growing complexity makes it harder to create and maintain a reliable CoC, and it exposes a wide gap between general evidentiary criteria based on traditional forensic procedures and the scientific community’s point of view about the risks and conditions necessary to consider reliable any contemporary digital evidence. | ||
This scenario circumscribes the objective of this work: to review difficulties and formulate suggestions to make a more reliable CoC of digital evidence, making it more consistent with legal necessity regardless of the country, company, or tool through which digital evidence is collected. Within this objective, this work explores gaps between the traditional CoC and the modern studies’ point-of-view about the risks and requirements concerning the reliability of contemporary digital evidence. | This scenario circumscribes the objective of this work: to review difficulties and formulate suggestions to make a more reliable CoC of digital evidence, making it more consistent with legal necessity regardless of the country, company, or tool through which digital evidence is collected. Within this objective, this work explores gaps between the traditional CoC and the modern studies’ point-of-view about the risks and requirements concerning the reliability of contemporary digital evidence. | ||
| Line 65: | Line 58: | ||
==Problem analysis and motivation for this research== | ==Problem analysis and motivation for this research== | ||
In the event of a crime, the investigation process relies heavily on physical and digital evidence. The judicial system has gradually become flexible in accepting digital evidence given the fact that the handling mechanism is somewhat similar to how they treat physical evidence.<ref name=":6" /><ref name=":8">{{Cite journal |last=Reedy |first=Paul |date=2020 |title=Interpol review of digital evidence 2016 - 2019 |url=https://linkinghub.elsevier.com/retrieve/pii/S2589871X20300152 |journal=Forensic Science International: Synergy |language=en |volume=2 |pages=489–520 |doi=10.1016/j.fsisyn.2020.01.015 |pmc=PMC7770434 |pmid=33385144}}</ref> The field of digital investigation continues to grow and therefore requires effective computer investigators with skills needed to capture the crime scene, call data records, search collected records, recover data, and engage with the forensic process.<ref name=":3" /><ref name=":8" /><ref name=":9">{{Cite journal |last=Aziz |first=Benjamin |last2=Blackwell |first2=Clive |last3=Islam |first3=Shareeful |date=2013-04-01 |title=A Framework for Digital Forensics and Investigations: The Goal-Driven Approach |url=https://services.igi-global.com/resolvedoi/resolve.aspx?doi=10.4018/jdcf.2013040101 |journal=International Journal of Digital Crime and Forensics |language=ng |volume=5 |issue=2 |pages=1–22 |doi=10.4018/jdcf.2013040101 |issn=1941-6210}}</ref> | |||
The issues a forensics team encounters with digital evidence are due to the nature of digital information. For example, digital information: | |||
*can easily be duplicated or reproduced; | |||
*can be altered and modified with new data or the removal of important information to the case, compromising its integrity; | |||
*has varying levels of accessibility, depending on how and by whom the information is treated/managed and what level of access control is granted to it; | |||
*requires secure storage to maintain its integrity; | |||
*can be transmitted to someone else or to a different country; and | |||
*in some cases, can be time-sensitive in purpose (e.g., to the case and pre-arrest situations). | |||
An issue arises with the gap introduced when providing digital evidence versus physical evidence in the court of law. This is certainly becoming a challenge to the judicial system’s solid and secure digital witnesses.<ref name=":6" /><ref>{{Cite journal |last=Mante |first=R. V. |last2=Khan |first2=Reshma |date=2020-03 |title=A Survey on Video-based Evidence Analysis and Digital Forensic |url=https://ieeexplore.ieee.org/document/9076417/ |journal=2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC) |publisher=IEEE |place=Erode, India |pages=118–121 |doi=10.1109/ICCMC48092.2020.ICCMC-00024 |isbn=978-1-7281-4889-2}}</ref> Another issue is that there are various practices of digital forensics activities and models. Figure 2 demonstrates the investigation process and how physical and digital evidence support each other in creating a complete theory about the criminal case. | |||
[[File:Fig2 Alruwaili Information21 12-2.png|1000px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="1000px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 2''' Physical and digital investigation constructs</blockquote> | |||
|- | |||
|} | |||
|} | |||
This paper argues for the utilization of blockchain technology to improve the CoC process and the evidence-handling life cycle. The blockchain is a digital ledger system, namely a distributed ledger technology (DLT), and we believe it can address the current issues faced with the digital evidence handling lifecycle. DLT implementation is growing due to its benefits in advancing sustainability, automation, and digital transformation. It also provides built-in security to control access to information and trace changes throughout the data life period. Nonetheless, the blockchain is an emerging technological advancement, hence very few concrete real-life applications have been identified. | |||
Proposed herein is a conceptual blockchain model (CB) to fill the gap in the literature and address the challenges faced in handling digital evidence to efficiently transform the global practice of law. The CB model demonstrates how blockchain and smart contracts can provide monitored and traceable access to the evidence chain for those involved participants, e.g., regulators, courts, law firms, etc. The CB nodes are trusted network stakeholders that have a sustainable and distributed set of rules/standards. The CB smart contracts ensure the automation of rights on the evidence related to the plaintiff, defendant, and involved third party. It also has the flexibility to adapt to and comply with the applicable judicial system and provide compliance metrics to the evidence-handling lifecycle. | |||
Various researchers<ref name=":6" /><ref name=":7" /><ref>{{Cite journal |last=Carrier, B.D.; Spafford, E.H. |year=2004 |title=An Event-Based Digital Forensic Investigation Framework |url=https://www.cerias.purdue.edu/apps/reports_and_papers/view/2762 |journal=Proceedings of the 2004 Digital Forensic Research Workshop |at=CERIAS TR 2004-53}}</ref><ref>{{Cite journal |last=Zhang |first=Ning |last2=Zhong |first2=Shan |last3=Tian |first3=Li |date=2017-12-04 |title=Using Blockchain to Protect Personal Privacy in the Scenario of Online Taxi-hailing |url=http://univagora.ro/jour/index.php/ijccc/article/view/2886 |journal=International Journal of Computers Communications & Control |volume=12 |issue=6 |pages=886–902 |doi=10.15837/ijccc.2017.6.2886 |issn=1841-9836}}</ref> have strongly suggested that computer forensics and law firms consider blockchain implementations for evidence handling before acquiring CoC services. By combining trustless, scalable, distributed, and traceable custody systems with the next generation of legal digital standards and service level agreements (SLAs), the forensics team and involved parties on a crime scene can be confident in their CoC and forensics activities. However, the focus here is on leveraging the trust, security, accessibility, provenance, and transportation of the digital evidence and handling service, the improvement of and investment in supporting law-enforcement institutions, and the investigation of cybercrime. | |||
==Existing research== | |||
Nowadays, forensic software is used to better acquire evidence that describes and identifies the electronic user, e.g., via the digital signature, [[audit trail]], etc. Still, there is still a significant gap between the usual CoC software and using traceable digital evidence effectively in the courtroom. Nowadays, this process is executed through the concept of CoC. The CoC is a set of consecutive documented records that demonstrate the order of custody for physical or electronic evidence, as well as of its control, transfer, and analysis. Maintaining CoC during the process of investigation and at the time of submitting the evidence in court can be challenging, however. In the past few years, various IoT-based studies have been conducted in forensics<ref>{{Cite journal |last=Hossain |first=Mahmud |last2=Hasan |first2=Ragib |last3=Zawoad |first3=Shams |date=2017-06 |title=Trust-IoV: A Trustworthy Forensic Investigation Framework for the Internet of Vehicles (IoV) |url=http://ieeexplore.ieee.org/document/8039051/ |journal=2017 IEEE International Congress on Internet of Things (ICIOT) |publisher=IEEE |place=Honolulu, HI, USA |pages=25–32 |doi=10.1109/IEEE.ICIOT.2017.13 |isbn=978-1-5386-2011-3}}</ref><ref>{{Cite journal |last=Hossain |first=Mahmud |last2=Hasan |first2=Ragib |last3=Zawoad |first3=Shams |date=2018-04 |title=Probe-IoT: A public digital ledger based forensic investigation framework for IoT |url=https://ieeexplore.ieee.org/document/8406875/ |journal=IEEE INFOCOM 2018 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) |publisher=IEEE |place=Honolulu, HI |pages=1–2 |doi=10.1109/INFCOMW.2018.8406875 |isbn=978-1-5386-5979-3}}</ref><ref>{{Cite journal |last=Li |first=Wanxin |last2=Guo |first2=Hao |last3=Nejad |first3=Mark |last4=Shen |first4=Chien-Chung |date=2020 |title=Privacy-Preserving Traffic Management: A Blockchain and Zero-Knowledge Proof Inspired Approach |url=https://ieeexplore.ieee.org/document/9210529/ |journal=IEEE Access |volume=8 |pages=181733–181743 |doi=10.1109/ACCESS.2020.3028189 |issn=2169-3536}}</ref><ref>{{Cite journal |last=Perdana |first=Arif |last2=Robb |first2=Alastair |last3=Balachandran |first3=Vivek |last4=Rohde |first4=Fiona |date=2021-04 |title=Distributed ledger technology: Its evolutionary path and the road ahead |url=https://linkinghub.elsevier.com/retrieve/pii/S0378720620302494 |journal=Information & Management |language=en |volume=58 |issue=3 |pages=103316 |doi=10.1016/j.im.2020.103316}}</ref><ref>{{Cite journal |last=Shah |first=Makhdoom |last2=Saleem |first2=Shahzad |last3=Zulqarnain |first3=Roha |date= |year=2017 |title=Protecting Digital Evidence Integrity and Preserving Chain of Custody |url=https://commons.erau.edu/jdfsl/vol12/iss2/12/ |journal=The Journal of Digital Forensics, Security and Law |volume=12 |at=12 |doi=10.15394/jdfsl.2017.1478}}</ref>, which includes the identification of the digital evidence, its collection, storage, analysis, and distribution within IoT platforms.<ref name=":5" /> This process is entirely different from existing computer-based forensics. Since 2017, blockchain technology has been applied in various applications of digital forensics, such as the documentation of evidence.<ref name=":10">{{Cite journal |last=Cebe |first=Mumin |last2=Erdin |first2=Enes |last3=Akkaya |first3=Kemal |last4=Aksu |first4=Hidayet |last5=Uluagac |first5=Selcuk |date=2018-10 |title=Block4Forensic: An Integrated Lightweight Blockchain Framework for Forensics Applications of Connected Vehicles |url=https://ieeexplore.ieee.org/document/8493118/ |journal=IEEE Communications Magazine |volume=56 |issue=10 |pages=50–57 |doi=10.1109/MCOM.2018.1800137 |issn=0163-6804}}</ref><ref>{{Cite journal |last=Van Der Horst |first=Luuc |last2=Choo |first2=Kim-Kwang Raymond |last3=Le-Khac |first3=Nhien-An |date=2017 |title=Process Memory Investigation of the Bitcoin Clients Electrum and Bitcoin Core |url=http://ieeexplore.ieee.org/document/8058429/ |journal=IEEE Access |volume=5 |pages=22385–22398 |doi=10.1109/ACCESS.2017.2759766 |issn=2169-3536}}</ref><ref>{{Cite journal |last=Liu |first=Zhe |last2=Seo |first2=Hwajeong |date=2019-03 |title=IoT-NUMS: Evaluating NUMS Elliptic Curve Cryptography for IoT Platforms |url=https://ieeexplore.ieee.org/document/8410894/ |journal=IEEE Transactions on Information Forensics and Security |volume=14 |issue=3 |pages=720–729 |doi=10.1109/TIFS.2018.2856123 |issn=1556-6013}}</ref><ref>{{Cite journal |last=Ritzdorf |first=Hubert |last2=Soriente |first2=Claudio |last3=Karame |first3=Ghassan O. |last4=Marinovic |first4=Srdjan |last5=Gruber |first5=Damian |last6=Capkun |first6=Srdjan |date=2018-12 |title=Toward Shared Ownership in the Cloud |url=https://ieeexplore.ieee.org/document/8360480/ |journal=IEEE Transactions on Information Forensics and Security |volume=13 |issue=12 |pages=3019–3034 |doi=10.1109/TIFS.2018.2837648 |issn=1556-6013}}</ref><ref>{{Cite journal |last=Tziakouris |first=Giannis |date=2018-07 |title=Cryptocurrencies—A Forensic Challenge or Opportunity for Law Enforcement? An INTERPOL Perspective |url=https://ieeexplore.ieee.org/document/8425619/ |journal=IEEE Security & Privacy |volume=16 |issue=4 |pages=92–94 |doi=10.1109/MSP.2018.3111243 |issn=1540-7993}}</ref><ref>{{Cite journal |last=Wu |first=Shuangke |last2=Chen |first2=Yanjiao |last3=Wang |first3=Qian |last4=Li |first4=Minghui |last5=Wang |first5=Cong |last6=Luo |first6=Xiangyang |date=2019-07 |title=CReam: A Smart Contract Enabled Collusion-Resistant e-Auction |url=https://ieeexplore.ieee.org/document/8543821/ |journal=IEEE Transactions on Information Forensics and Security |volume=14 |issue=7 |pages=1687–1701 |doi=10.1109/TIFS.2018.2883275 |issn=1556-6013}}</ref> Zhang ''et al.''<ref>{{Cite journal |last=Zhang |first=Yong |last2=Wu |first2=Songyang |last3=Jin |first3=Bo |last4=Du |first4=Jiaying |date=2017-12 |title=A blockchain-based process provenance for cloud forensics |url=http://ieeexplore.ieee.org/document/8322979/ |journal=2017 3rd IEEE International Conference on Computer and Communications (ICCC) |publisher=IEEE |place=Chengdu |pages=2470–2473 |doi=10.1109/CompComm.2017.8322979 |isbn=978-1-5090-6352-9}}</ref> proposed a provenance process model for digital investigations using blockchain in a [[Cloud computing|cloud-based]] environment, with the idea that it can enhance the interaction trust between stakeholders in cloud forensics. Al-Nemrat<ref name=":11">{{Cite journal |last=Al-Nemrat |first=Ameer |date=2018-04 |title=Identity theft on e-government/e-governance & digital forensics |url=https://ieeexplore.ieee.org/document/8378961/ |journal=2018 International Symposium on Programming and Systems (ISPS) |publisher=IEEE |place=Algiers |pages=1–1 |doi=10.1109/ISPS.2018.8378961 |isbn=978-1-5386-4690-8}}</ref> investigated the possibility of introducing blockchain-based technologies in the investigation of financial fraud in e-governance. Al-Nemrat's results show that their proposed technology can be effective in determining financial fraud related to the reviews of online products.<ref name=":11" /> | |||
Ulybyshev ''et al.''<ref>{{Cite journal |last=Ulybyshev |first=Denis |last2=Villarreal-Vasquez |first2=Miguel |last3=Bhargava |first3=Bharat |last4=Mani |first4=Ganapathy |last5=Seaberg |first5=Steve |last6=Conoval |first6=Paul |last7=Pike |first7=Robert |last8=Kobes |first8=Jason |date=2018-07 |title=(WIP) Blockhub: Blockchain-Based Software Development System for Untrusted Environments |url=https://ieeexplore.ieee.org/document/8457849/ |journal=2018 IEEE 11th International Conference on Cloud Computing (CLOUD) |publisher=IEEE |place=San Francisco, CA |pages=582–585 |doi=10.1109/CLOUD.2018.00081 |isbn=978-1-5386-7235-8}}</ref> explained that the blockchain is used to provide the process of audibility, traceability in software development, and a role-based access control mechanism for the accesses of unauthorized data. Hossain ''et al.''<ref>{{Cite journal |last=Hossain |first=Mahmud |last2=Karim |first2=Yasser |last3=Hasan |first3=Ragib |date=2018-07 |title=FIF-IoT: A Forensic Investigation Framework for IoT Using a Public Digital Ledger |url=https://ieeexplore.ieee.org/document/8473437/ |journal=2018 IEEE International Congress on Internet of Things (ICIOT) |publisher=IEEE |place=San Francisco, CA |pages=33–40 |doi=10.1109/ICIOT.2018.00012 |isbn=978-1-5386-7244-0}}</ref> proposed a forensic investigation framework based on the blockchain, which focuses on detecting various criminal incidents in the IoT and also on collecting the details of communications from different entities present in it. Their proposed framework can model the interaction of transactions. The main drawback of their methodology is its inefficiency in the collection of data and its analysis in large-scale IoT-based systems. Lone and Mir<ref>{{Cite journal |last=Lone |first=Auqib Hamid |last2=Mir |first2=Roohie Naaz |date=2019-03 |title=Forensic-chain: Blockchain based digital forensics chain of custody with PoC in Hyperledger Composer |url=https://linkinghub.elsevier.com/retrieve/pii/S174228761830344X |journal=Digital Investigation |language=en |volume=28 |pages=44–55 |doi=10.1016/j.diin.2019.01.002}}</ref> proposed a digital forensic chain based on the popular blockchain platform called Ethereum. Ethereum can provide integrity, transparency, and authenticity for the multiple sources of data. Various studies have been done on the process of digital investigations in the heterogeneous environment<ref>{{Cite journal |last=Caviglione |first=Luca |last2=Wendzel |first2=Steffen |last3=Mazurczyk |first3=Wojciech |date=2017-11 |title=The Future of Digital Forensics: Challenges and the Road Ahead |url=http://ieeexplore.ieee.org/document/8123473/ |journal=IEEE Security & Privacy |volume=15 |issue=6 |pages=12–17 |doi=10.1109/MSP.2017.4251117 |issn=1540-7993}}</ref>, security solutions in lightweight IoT devices<ref name=":9" />, digital witnesses<ref name=":10" />, etc. | |||
From these studies, it appears recent analysis and research on digital forensics falls under two categories: focusing on assisting the law enforcement community and focusing on specific forensics applications. Ćosić and Bača<ref>{{Cite journal |last=Ćosić, J.; Bača, M. |year=2010 |title=A framework to (Im)Prove "Chain of Custody" in Digital Investigation Process |url=http://archive.ceciis.foi.hr/app/index.php/ceciis/2010/schedConf/presentations |journal=Proceedings of the 21st Central European Conference on Information and Intelligent Systems |pages=435–38}}</ref> proposed a conceptual digital evidence management framework (DEMF) to improve the CoC of digital evidence in all the phases of the investigation. They used a hash code for the fingerprinting of evidence, assessing hash similarity to change control, identifying biometrics, authenticating digital signatures, performing automatic and trusted timestamping, and running GPS and RFID for geolocation. These components can be implemented through a database to record all the activities performed by the first responders, forensic investigators, verifier or acceptors, law enforcement personnel, and police officers, etc. This work aims at developing a blockchain-based CustodyBlock digital forensic model that can be used in complex cyber environments (such as IoT, cyber-physical systems, etc.) and providing an effective architecture for the proposed methodology. | |||
==Research methodology== | |||
There are several published forensics models with detailed guidelines for the forensics team. For instance, there is a set of tasks and procedures to maintain the integrity of the captured evidence and avoid contradiction with jurisdictional laws and regulation by maintaining compliance with the applicable law requirements. ISO/IEC 27050-2:2018 is a [[cybersecurity]] guidance document that highlights standards and codes of practice for electronic discovery, i.e., eDiscovery, which aims at protecting electronically stored information (ESI), including recorded data by any involved parties in the investigation process. Similarly, the digital forensic research workshop (DFRWS) model is set to protect the digital forensic process, and has six stages that start with the identification phase during an incident/event, followed by preservation, collection, examination, and analysis. Lastly, the collected evidence report is set as part of the presentation phase.<ref name=":6" /><ref name=":12">{{Cite journal |last=Zhang |first=Xiaolu |last2=Choo |first2=Kim-Kwang Raymond |last3=Beebe |first3=Nicole Lang |date=2019-08 |title=How Do I Share My IoT Forensic Experience With the Broader Community? An Automated Knowledge Sharing IoT Forensic Platform |url=https://ieeexplore.ieee.org/document/8694855/ |journal=IEEE Internet of Things Journal |volume=6 |issue=4 |pages=6850–6861 |doi=10.1109/JIOT.2019.2912118 |issn=2327-4662}}</ref> | |||
This methodology utilizes a grounded and qualitative theory set by Jabareen<ref name=":6" />, i.e., the “conceptual framework analysis” approach to building conceptual frameworks. In addition to the current digital investigation models (e.g., ISO/IEC 27050 and DFRWS), Jabareen’s approach is used to devise the CB model. This stipulates identifying a phenomenon’s key factors, which when organized, clarify the proposed solution. Every key factor has its attributes, assumptions, and roles that have a specific function within the proposed model. In addition, three forms of a given assumption are presented: | |||
*the way things are, i.e., ontological; | |||
*how things interact/work, i.e., epistemological; and | |||
*the process in building the conceptual model that fits/understands the real world, i.e., methodological. | |||
The main step in this method is to derive concepts from data within the knowledge base, i.e., literature cases, and inject the deductive procedure to generate the relationship between the model's key factors. The overall process emphasizes an iterative interplay between inductive data and the analysis phases. In the end, this results in arriving at a solid examination of the potential and applicability of blockchain and smart contracts to advance CoC and the digital evidence handling model. Moreover, basic evidence metrics<ref name=":2" /> are considered to improve the traceability and evidence sources. This includes location of the data when generated, type and form of data, time elapsed since it was stored, its currently employed control and security measures, who last accessed it, when it was last reviewed, who the owner or responsible entity is, and what the transfer procedure was. | |||
==CustodyBlock framework== | |||
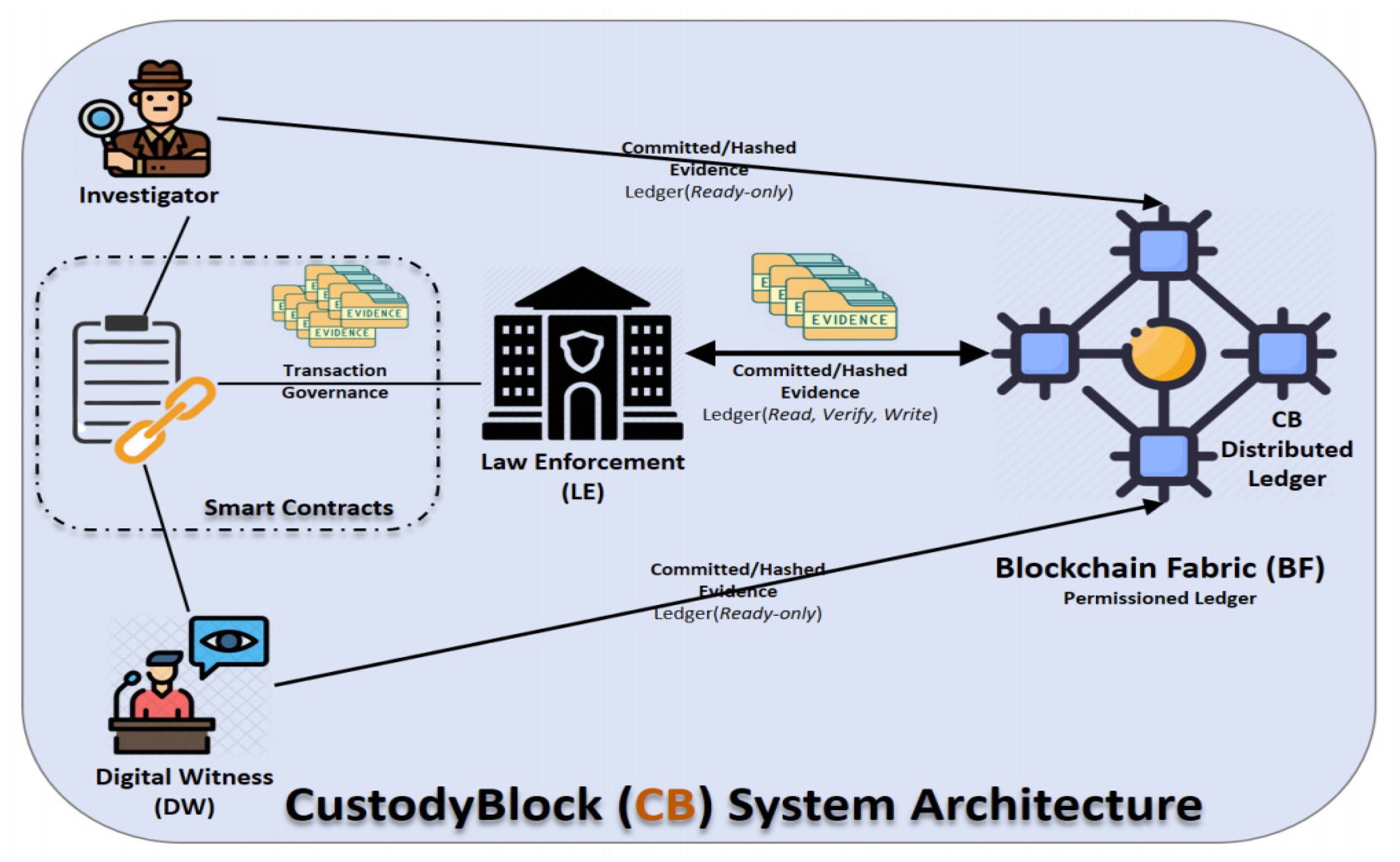
The CustodyBlock system architecture includes the participants (law enforcement, cloud service providers, validators), a consensus algorithm, a smart contract, cryptographic functions, and a digital signature. The main CustodyBlock model components are shown in Figure 3 and described below. | |||
[[File:Fig3 Alruwaili Information21 12-2.png|800px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 3''' CustodyBlock framework</blockquote> | |||
|- | |||
|} | |||
|} | |||
The CustodyBlock model ensures proper CoC documentation in order to allow the admissibility and validity of digital evidence. Participants have many roles and responsibilities within the system. The following are major participating actors in the CustodyBlock model: | |||
*Law enforcement (LE): This is the major player in the model. LE is a trusted third-party or government entity that is tasked with ensuring proper evidence handling procedures, e.g., collection, preservation, analysis, archiving, etc. The LE entity sets the roles for CustodyBlock transactions' read/write controls and ledger read/write controls. LE details the rules needed to be written/coded in smart contracts to automate entity registration and onboarding, e.g., registering digital witnesses and investigators | |||
*Digital witness (DW): This is the interconnected network of devices, such as laptops, smartphones, and IoTs, such as home appliances and connected vehicles, etc. DW provides collaboration on providing incident-based/sensor-based evidence within their capabilities. The captured evidence puts investigators and LE forward for further investigation. | |||
==Digital evidence custody (DEC)== | |||
An approved and accredited administrative person or entity is required to ensure the proper handling of the evidence received from investigators, LE, or authorized trusted law enforcement entities. DEC can be automated through the use of smart contracts and [[machine learning]] algorithms. In this case, the "blockchain fabric" (BF) is used. | |||
BF describes the private blockchain implementation using, e.g., Ethereum or Hyperledger fabric as the main underlying system for the CustodyBlock application. Participating roles and responsibilities act as active nodes of the CustodyBlock blockchain network. The BF contains an essential element to this structure, i.e., the shared ledger or DLT, which will be able to log all collective and transferred evidence and immutability shared among all the different and authorized entities. The DLT is governed by lawmakers and law enforcement institutes. | |||
The BF has three sub-functions, which together form the operation of the BF. These are: | |||
:1. Secure transaction: This carries the evidence track records, e.g., submission, archiving, transfer, fetching, etc. Each transaction entails necessary information and a unique identifier. Information details are set as per forensic investigation standards to include data type, timestamp, submitter and receiver IDs, geographical locations, etc. The transaction is then hashed, and once verified by the consensus algorithm, will be stored in the CustodyBlock DLT and distributed among all active network nodes. | |||
:2. Smart contract: Each transaction can be automated using a smart contract. A smart contract is a set of predetermined executable instructions based on the nature of a certain transaction or input. An output can also trigger another smart contract. For example, a case is created, and the smart contract logs the submitter ID and associated evidence provided by the analysis phase. Based on the analysis output, the smart contract initiates another instance to request more evidence from the submitter or witnesses. If the submitted evidence is sufficient for the case, then the smart contract proceeds to the analysis and investigation procedures. Additional steps in the investigation process, e.g., evidence transfer and archival, are not presented in this paper. | |||
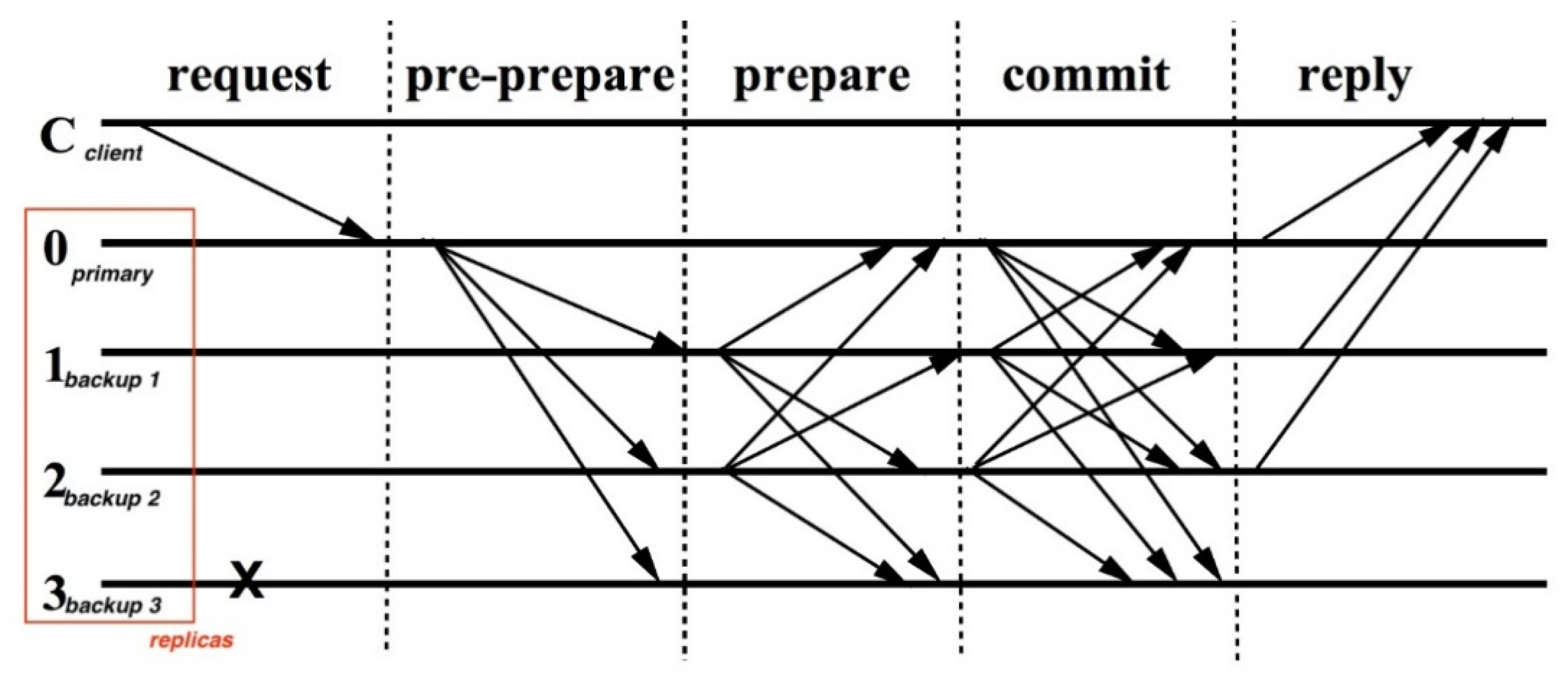
:3. Consensus node: This is a function with a set of rules that is responsible for maintaining, verifying, and approving BF records/transactions and updating the ledger. It also ensures trustworthiness when reliability, availability, accuracy, and authenticity are built in by design. The on-chain governance of the CustodyBlock blockchain is achieved by consensus nodes by not only restricting access to the CustodyBlock ledger, but also who can perform different actions, e.g., validation of transactions. There are different implementations of consensus algorithms, such as proof of work (PoW), proof of stake (PoS), delegated proof of stake (DPoS), practical byzantine fault tolerance (pBFT), proof of authority (PoA), etc. A private (permissioned) implementation of the CustodyBlock model is suggested with the use of practical byzantine fault tolerance (pBFT) as a consensus algorithm. The pBFT is considered for the CustodyBlock model with the assumption that some of the consensus nodes may act faultily or maliciously in the network, hence the need for taking proactive measures to ensure consistent and valid voting/validation, shown in Figure 4. The pBFT does not scale to accommodate other blockchains or larger volume, but for maintaining evidence handling, the author believes it should suffice. | |||
[[File:Fig4 Alruwaili Information21 12-2.png|800px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 4''' Operation phases of pBFT<ref name=":12" /></blockquote> | |||
|- | |||
|} | |||
|} | |||
The given process achieves consensus if the majority of the CB network nodes agree on the same output value. The pBFT phases are: | |||
#A “request” for evidence handling procedure is received. | |||
#A “pre-prepare” phase includes this shared request in a proposal. | |||
#A “prepare” phase is set for voting/validating and coming to an agreement. | |||
#A “commit” phase allows each consensus node to communicate to each other their results, and the majority agreed-upon value will be committed into the ledger and updated in the whole CB network. | |||
==Algorithm for the proposed methodology== | |||
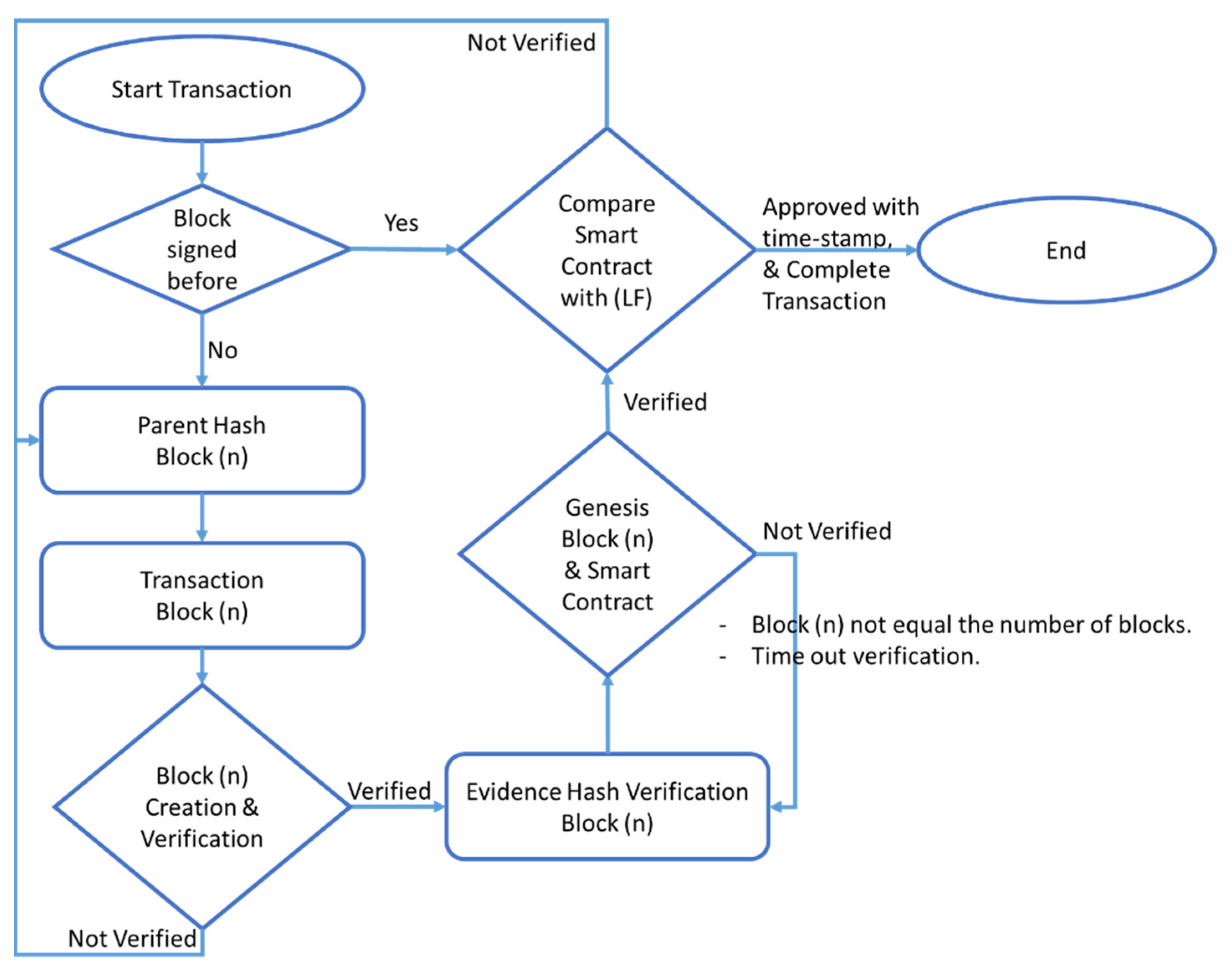
The following programing is the pseudo code of the algorithm of the proposed mechanism using Python and the Hyperledger platform. Our algorithm creates a number of blocks with different hashes and with timestamps to approve, verify, and track the transactions made by the blocks. The blocks’ authentication uses public key infrastructure (PKI) with smart contracts to approve the creation of the created evidence. Figure 5 shows the flowchart of the proposed algorithm. | |||
[[File:Fig5 Alruwaili Information21 12-2.png|800px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="800px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 5''' Flowchart of the proposed algorithm</blockquote> | |||
|- | |||
|} | |||
|} | |||
The mathematical model and algorithm are inspired by the work of Giova<ref name=":1" /> and Tang ''et al.''<ref>{{Cite journal |last=Tang |first=Huanrong |last2=Sun |first2=Yaojing |last3=Ouyang |first3=Jianquan |date=2020 |title=Excellent Practical Byzantine Fault Tolerance |url=https://www.techscience.com/JCS/v2n4/40714 |journal=Journal of Cyber Security |language=en |volume=2 |issue=4 |pages=167–182 |doi=10.32604/jcs.2020.011341 |issn=2579-0064}}</ref> The following is the pseudo Algorithm 1 of our proposed algorithm, which was also created in advance by the Hyperledger platform: | |||
{| | |||
| style="vertical-align:top;" | | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="100%" | |||
|- | |||
| colspan="3" style="background-color:white; padding-left:10px; padding-right:10px;" |'''Algorithm 1.''' Custody Block | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" | | |||
<nowiki># (parent_hash, transactions, hash_evidence, smart_contract)</nowiki><br /> | |||
<nowiki>def get_parent_hash (block): return block [0]</nowiki><br /> | |||
<nowiki>def get_transactions (block): return block [1]</nowiki><br /> | |||
<nowiki>def get_hash_evidence (block): return block [15]</nowiki><br /> | |||
<nowiki># function to create a block in a blockchain</nowiki><br /> | |||
<nowiki>“ver”:1, “vin_sz”:1, “vout_sz”:2,</nowiki><br /> | |||
<nowiki>“lock_time”:”Unavailable”,</nowiki><br /> | |||
<nowiki>hash_evidence=hash ((transactions, parent_hash))</nowiki><br /> | |||
<nowiki>return (parent_hash, transactions, hash_evidence)</nowiki><br /> | |||
<nowiki># function to create the genesis block</nowiki><br /> | |||
<nowiki>def create_genesis_block (transactions):</nowiki><br /> | |||
<nowiki>return create_block (transactions, 0)</nowiki><br /> | |||
<nowiki>Smart_Contract = create_genesis_block (“Create Evidence”)</nowiki><br /> | |||
<nowiki># function to create the smart contract block</nowiki><br /> | |||
<nowiki>block1 = create_block (“Smart Contract”, genesis_block_hash)</nowiki><br /> | |||
<nowiki># function to create the smart contract</nowiki><br /> | |||
<nowiki>genesis_block_hash = get_hash_evidence (smart_contract)</nowiki><br /> | |||
<nowiki>print “smart contract hash:”, smart_contract_hash</nowiki> | |||
|- | |||
|} | |||
|} | |||
==Discussion and further applications== | |||
The CB model can be used in different applications, such as private blockchain or IoT applications. This model is a novel technique inspired by the Hyperledger technology supported by the Linux Foundation and IBM, which uses smart contracts and public key infrastructure (PKI) to achieve confidentiality, integrity, availability, authentication, and authorization. PKI-based solutions encrypt the transaction transmitted from the authorized source peer to the destination. The proposed model can be used to authenticate IoT users and devices to avoid different kinds of inside and outside threads and attacks. | |||
Blockchain is a decentralization technology that stores the data and the transactions into distributed peer-to-peer blocks. These blocks can be used to create and verify transactions using hashing and cryptographic algorithms. New technologies such as zero-knowledge proof (ZKP) are adding even more security to blockchain technology by using a third party, called the “prover,” who can prove and verify the value without getting any information about the transaction while only possessing the secret information.<ref>{{Cite journal |last=Wang |first=Dan |last2=Zhao |first2=Jindong |last3=Wang |first3=Yingjie |date=2020 |title=A Survey on Privacy Protection of Blockchain: The Technology and Application |url=https://ieeexplore.ieee.org/document/9093015/ |journal=IEEE Access |volume=8 |pages=108766–108781 |doi=10.1109/ACCESS.2020.2994294 |issn=2169-3536}}</ref><ref>{{Cite journal |last=Raikwar |first=Mayank |last2=Gligoroski |first2=Danilo |last3=Kralevska |first3=Katina |date=2019 |title=SoK of Used Cryptography in Blockchain |url=https://ieeexplore.ieee.org/document/8865045/ |journal=IEEE Access |volume=7 |pages=148550–148575 |doi=10.1109/ACCESS.2019.2946983 |issn=2169-3536}}</ref><ref>{{Cite journal |last=Partala |first=Juha |last2=Nguyen |first2=Tri Hong |last3=Pirttikangas |first3=Susanna |date=2020 |title=Non-Interactive Zero-Knowledge for Blockchain: A Survey |url=https://ieeexplore.ieee.org/document/9300214/ |journal=IEEE Access |volume=8 |pages=227945–227961 |doi=10.1109/ACCESS.2020.3046025 |issn=2169-3536}}</ref> In fact, Liu ''et al.''<ref name=":4" /> used ZKP and multi-factor authentication in 2019 to secure the verifier's identity. This method is promising and may also be used in many IoT devices and applications. However, the following three properties need to be satisfied for the method to work<ref>{{Cite journal |last=Nieto |first=Ana |last2=Roman |first2=Rodrigo |last3=Lopez |first3=Javier |date=2016-11 |title=Digital Witness: Safeguarding Digital Evidence by Using Secure Architectures in Personal Devices |url=http://ieeexplore.ieee.org/document/7764297/ |journal=IEEE Network |volume=30 |issue=6 |pages=34–41 |doi=10.1109/MNET.2016.1600087NM |issn=0890-8044}}</ref>: | |||
*Completeness: Knowing a spectator and the authenticity of a statement, the prover can convince the verifier. | |||
*Soundness: A malicious prover cannot persuade the verifier in the situation that the assertion is bogus. | |||
*Zero-information: The verifier asserts nothing aside from the fact that the assertion is valid. | |||
==Conclusions and future work== | |||
In this paper, a blockchain-based protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring have been proposed. The proposed method utilizes a conceptual blockchain model using novel CoC technology, along with the CB model using private blockchain protocol and smart contracts, to fill the gap in the literature and address the challenges faced in handling digital evidence to efficiently transform global legal practices. The CB model demonstrates how blockchain and smart contracts can provide monitored and traceable access to the evidence chain for those involved participants, e.g., regulators, courts, law firms, etc. To ensure security in sharing the forensic data, the proposed mechanism ensures that all participating entities are authorized to exchange and share the data. The proposed model provides the platform on which the forensic data can be stored without any attacks and acts as a better and more secure evidence preservation and handling methodology. | |||
Future enhancements to this model can be imagined. For example, intelligent-based methods can be combined with the blockchain for providing privacy and security in electronic data. Additional benefits could be had with the addition of biometric-based systems. | |||
In the future, CoC technology can be used for IoT smart home and healthcare applications to add security. In situations like the [[COVID-19]] [[pandemic]]—where rapid, accurate, and secure information is vital to effective treatments—this model has the potential to help patients and the treatment team by better securing point-of-care and IoT medical devices, [[electronic health record]]s (EHRs), patient healthcare information (PHI), and other healthcare applications. In the future, we would like to conduct a case study comparing the proposed CB model with a zero-knowledge proof (ZKP) model for smart home IoT applications using multi-factor authentication to secure the IoT user’s identity. | |||
==Acknowledgements== | |||
===Funding=== | |||
This research received no external funding. | |||
===Data availability=== | |||
Data available on request due to restrictions e.g., privacy or ethical. | |||
===Conflict of interest=== | |||
The author declares no conflict of interest. | |||
==References== | ==References== | ||
| Line 73: | Line 235: | ||
==Notes== | ==Notes== | ||
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added. | This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added. The original uses "DC" in the text but fails to establish what it means. It's also not clear what it means after looking at the figures. This version assumes it means "investigators." The original mistakenly omitted a citation for Liu ''et al.'' 2019 in the discussion; it was added for this version. | ||
<!--Place all category tags here--> | <!--Place all category tags here--> | ||
[[Category:LIMSwiki journal articles (added in | [[Category:LIMSwiki journal articles (added in 2022)]] | ||
[[Category:LIMSwiki journal articles (all)]] | [[Category:LIMSwiki journal articles (all)]] | ||
[[Category:LIMSwiki journal articles on cybersecurity]] | [[Category:LIMSwiki journal articles on cybersecurity]] | ||
[[Category:LIMSwiki journal articles on forensic science]] | [[Category:LIMSwiki journal articles on forensic science]] | ||
Latest revision as of 16:19, 28 June 2022
| Full article title | CustodyBlock: A distributed chain of custody evidence framework |
|---|---|
| Journal | Information |
| Author(s) | Alruwaili, Fahad F. |
| Author affiliation(s) | Shaqra University |
| Primary contact | Email: alruwaili at su dot edu dot sa |
| Year published | 2021 |
| Volume and issue | 12(2) |
| Article # | 88 |
| DOI | 10.3390/info12020088 |
| ISSN | 2078-2489 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2078-2489/12/2/88/htm |
| Download | https://www.mdpi.com/2078-2489/12/2/88/pdf (PDF) |
Abstract
With the increasing number of cybercrimes, the digital forensics team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of information that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient evidence management to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate chain of custody (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private blockchain protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed.
Keywords: forensics, cybersecurity, distributed ledger technology (DLT), smart contract, blockchain
Introduction
Evidence management is one of the most important problems in digital forensics. Digital proof plays a vital role in crime investigations because it is used to link persons with their criminal activities. Chain of custody (CoC) in digital forensics can be defined as a process of documenting and maintaining the chronological history of handling digital evidence.[1][2] This plays an important role in the investigation of digital forensics because it notes every detail of concern to digital evidence through different levels of hierarchy. This goes from the first responder to the higher authorities who were responsible for handling the investigation of cybercrime.
Digital proof comes with its own particular challenges, particularly when linked with the CoC. Blockchain technology can enable various stages of digital transaction to take place, however, providing massive advantages for the forensic community. In general, blockchain can act as a scattered form of information that maintains tamper-proof arrangement blocks that hold a cluster of individual transactions. It executes a decentralized and fully replicated append-only ledger, present in a peer-to-peer network, originally deployed for the bitcoin cryptocurrency. All the nodes present on the chain maintain a complete local copy of the blockchain. The blockchain is an indigenous technology that has emerged for decentralized applications, the outcome of complicated privacy and security issues present in applications for over half a century.[3][4] It is a peer-to-peer system that authorizes users to maintain a ledger for various transactions that are reproduced, and it remains identical in more than one location over multiple user servers.[5]
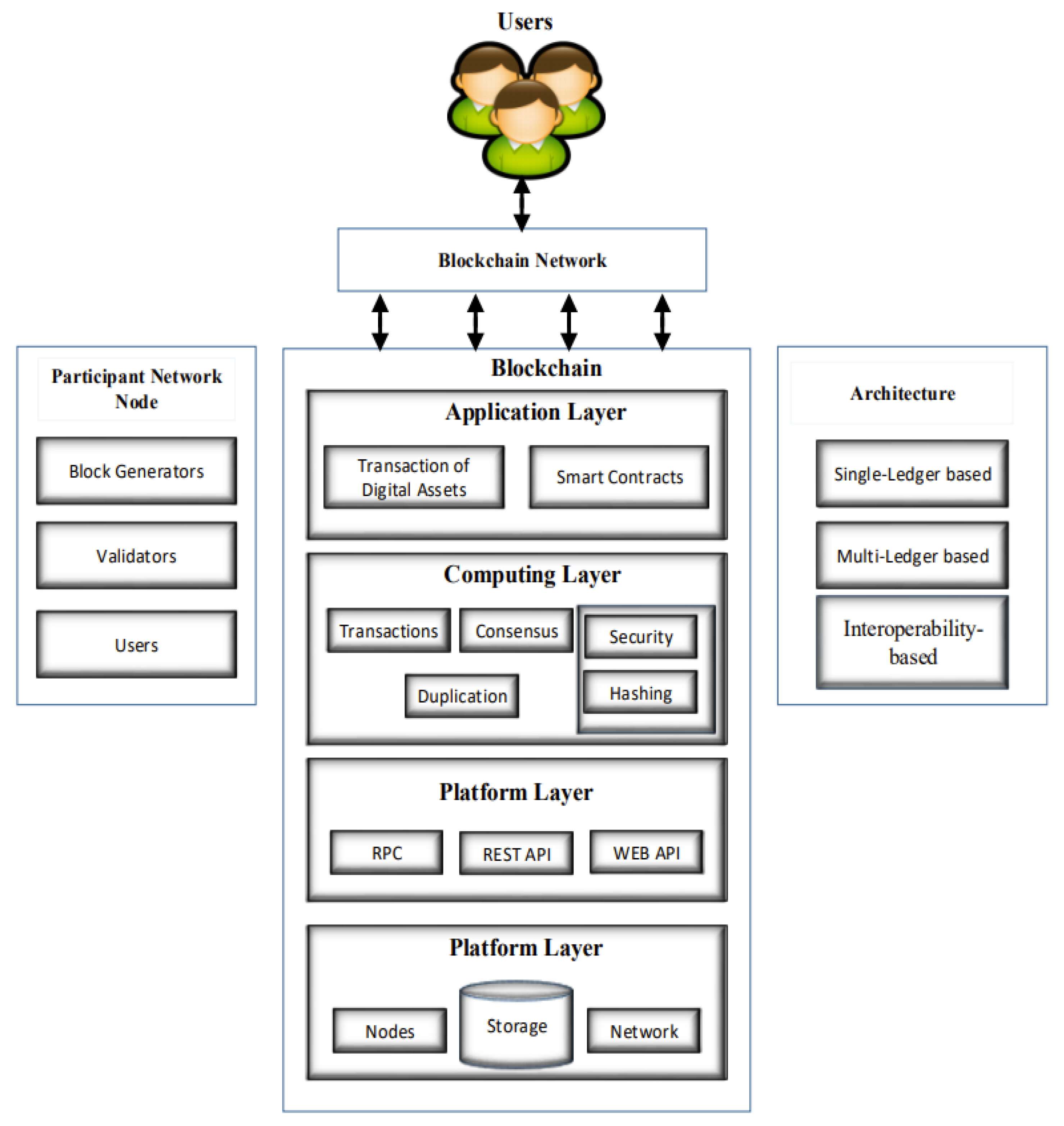
A blockchain is essentially a "block of chains," with the growing list of records that come from it referred to as "blocks" that are joined with cryptography.[4] Each blockchain contains a hash of a previous block, and a timestamp that keeps track of the creation and modification time of a document. In terms of security, nobody, not even the owners of the document, ought to be able to modify it once it has been recorded (this can be done only if the integrity of time-stampers is compromised, which is rare). Blockchain was invented in 2008 and implemented in 2009 to function in the general public ledger of the Bitcoin cryptocurrency, a type of electronic money. Blockchain technology is decentralized (i.e., peer-to-peer). It consists of world network computers, which apply blockchain technology to put together and manage the information that records each Bitcoin transaction managed by its network. The architecture of blockchain technology, shown in Figure 1, implements a decentralized, fully replicated append-only ledger in a peer-to-peer network.[6]
|
The methodology proposed in this paper uses IBM's Hyperledger blockchain technology, as it is private and open-source. Hyperledger supports smart contracts called chaincodes.[7] Hyperledger is able to approve blocks and send the associated exchange transactions to the trusted and approved blocks to be validated and approved.[8] This is the most broadly utilized blockchain stage, utilized across various ventures and use-cases. It is utilized in a few models and proof-of-concepts, and is also being disseminated in record frameworks.
Hyperledger is a blockchain with pluggable agreement. It is one of the more favorable uses of Hyperledger, which is hosted by the Linux Foundation. It is the first blockchain framework that permits the execution of dispersed applications written in standard programming. While generic blockchain utilizes request–execute–approve engineering, Hyperledger uses an execute–request–approve design and a support strategy that is overseen by assigned directors and functions as a static library for exchange approval.[9]
Blockchain technology also provides decentralization, tracking, data transparency, security, and privacy for internet of things (IoT) applications.[10] IoT applications running in medical, transportation, agriculture, and other contexts require a high level of security. Blockchain provides the necessary security and privacy for different IoT applications and transactions, while maintaining a high level of integrity. Additionally, blockchain provides a high level of management for IoT systems by using privileged digital identities and access management.[11] Many researchers illustrate the importance of connecting IoT systems to a blockchain-based technology to enhance the level of security and IoT performance.[12][13][14]
In the context of digital forensics, the production of evidence in the modern digital world is a complex task. For this reason, we consider it essential that digital evidence should be accepted as valid in court only if the CoC can assure exactly what the evidence is, why it was collected and analyzed, and how evidentiary data were collected, analyzed, and reported. This can be in the form of big data.[15][16] Additionally, the CoC must demonstrate exactly where, when, and who came into contact with the electronic evidence in each stage of an investigation, as well as any manipulation of the evidence.[17][18] The increasing complexity of forensic science in the digital area leads researchers to claim that traditional computer forensics “is on the edge of a precipice,” especially because of the great diversity of electronic devices to be examined and the intensive growth of the quantity of data that must be collected and examined during preservation in the blockchain.[19][20] This growing complexity makes it harder to create and maintain a reliable CoC, and it exposes a wide gap between general evidentiary criteria based on traditional forensic procedures and the scientific community’s point of view about the risks and conditions necessary to consider reliable any contemporary digital evidence.
This scenario circumscribes the objective of this work: to review difficulties and formulate suggestions to make a more reliable CoC of digital evidence, making it more consistent with legal necessity regardless of the country, company, or tool through which digital evidence is collected. Within this objective, this work explores gaps between the traditional CoC and the modern studies’ point-of-view about the risks and requirements concerning the reliability of contemporary digital evidence.
This paper also aims to contribute to the discussion about the trend to establish a worldwide standard more suited to maintaining CoC throughout the lifecycle of digital evidence and to help the improvement of new versions of CoC software. This work will not define or select any standard itself, because that is outside the scope of this paper. More specifically, this paper aims to address the challenges in forensic evidence collection, preservation, and investigation processes, for IoT environments in the smart home domain, by exploiting novel CoC technology, along with the CustodyBlock (CB) model, using private blockchain protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring of forensic evidence.
The remainder of the paper is structured as follows. The next section analyzes the inherent problems of maintaining the CoC of digital evidence and the motivation for the proposed research, while the existing studies done in the area of the application of blockchain in forensics are described in the section after that. The paper then explains the research methodology, shows the proposed CustodyBlock model and its supporting architecture, illustrates digital evidence custody (DEC), and explains the algorithm for the proposed methodology. The penultimate section provides discussion and states future work, while the conclusion and future enhancements are given at the end.
Problem analysis and motivation for this research
In the event of a crime, the investigation process relies heavily on physical and digital evidence. The judicial system has gradually become flexible in accepting digital evidence given the fact that the handling mechanism is somewhat similar to how they treat physical evidence.[17][21] The field of digital investigation continues to grow and therefore requires effective computer investigators with skills needed to capture the crime scene, call data records, search collected records, recover data, and engage with the forensic process.[7][21][22]
The issues a forensics team encounters with digital evidence are due to the nature of digital information. For example, digital information:
- can easily be duplicated or reproduced;
- can be altered and modified with new data or the removal of important information to the case, compromising its integrity;
- has varying levels of accessibility, depending on how and by whom the information is treated/managed and what level of access control is granted to it;
- requires secure storage to maintain its integrity;
- can be transmitted to someone else or to a different country; and
- in some cases, can be time-sensitive in purpose (e.g., to the case and pre-arrest situations).
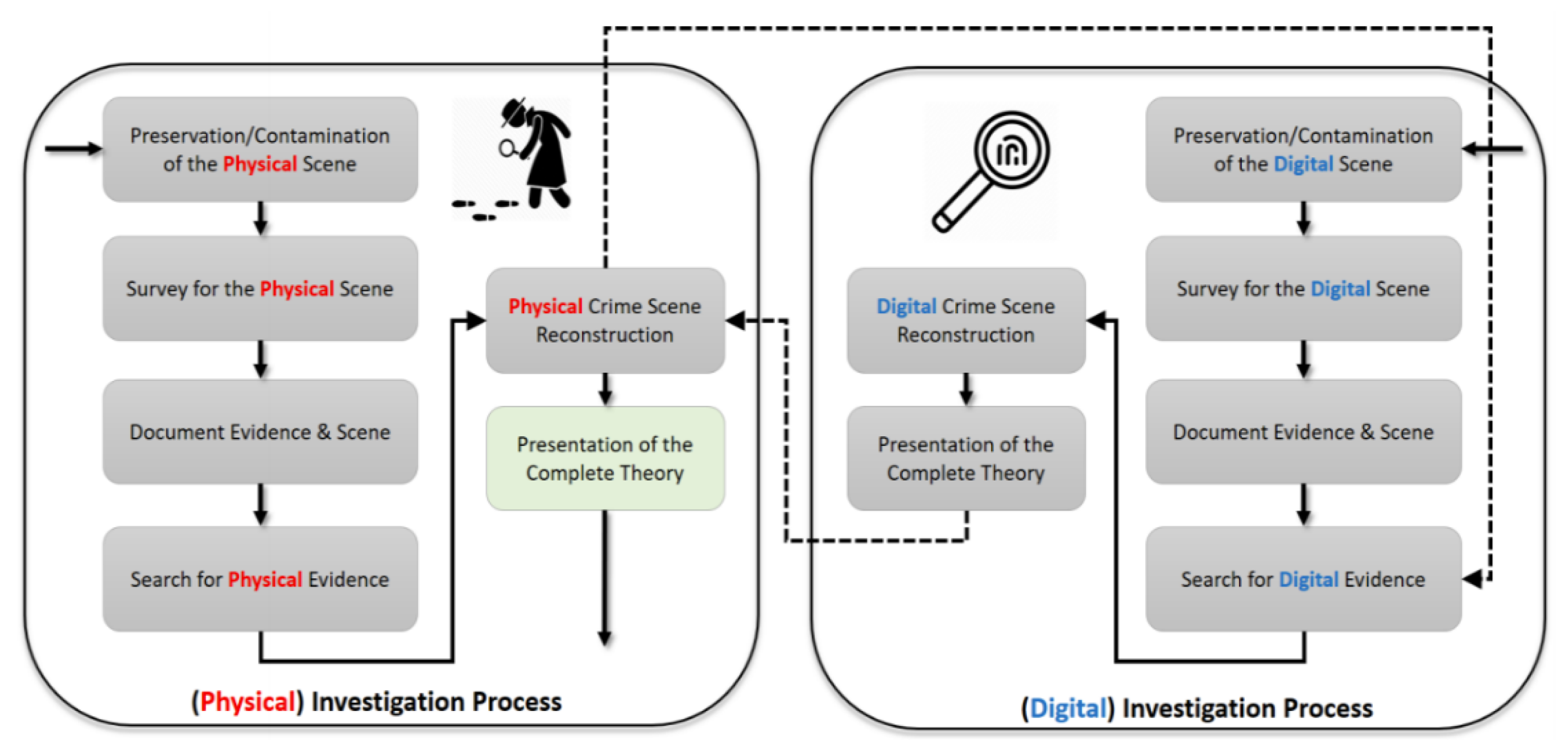
An issue arises with the gap introduced when providing digital evidence versus physical evidence in the court of law. This is certainly becoming a challenge to the judicial system’s solid and secure digital witnesses.[17][23] Another issue is that there are various practices of digital forensics activities and models. Figure 2 demonstrates the investigation process and how physical and digital evidence support each other in creating a complete theory about the criminal case.
|
This paper argues for the utilization of blockchain technology to improve the CoC process and the evidence-handling life cycle. The blockchain is a digital ledger system, namely a distributed ledger technology (DLT), and we believe it can address the current issues faced with the digital evidence handling lifecycle. DLT implementation is growing due to its benefits in advancing sustainability, automation, and digital transformation. It also provides built-in security to control access to information and trace changes throughout the data life period. Nonetheless, the blockchain is an emerging technological advancement, hence very few concrete real-life applications have been identified.
Proposed herein is a conceptual blockchain model (CB) to fill the gap in the literature and address the challenges faced in handling digital evidence to efficiently transform the global practice of law. The CB model demonstrates how blockchain and smart contracts can provide monitored and traceable access to the evidence chain for those involved participants, e.g., regulators, courts, law firms, etc. The CB nodes are trusted network stakeholders that have a sustainable and distributed set of rules/standards. The CB smart contracts ensure the automation of rights on the evidence related to the plaintiff, defendant, and involved third party. It also has the flexibility to adapt to and comply with the applicable judicial system and provide compliance metrics to the evidence-handling lifecycle.
Various researchers[17][20][24][25] have strongly suggested that computer forensics and law firms consider blockchain implementations for evidence handling before acquiring CoC services. By combining trustless, scalable, distributed, and traceable custody systems with the next generation of legal digital standards and service level agreements (SLAs), the forensics team and involved parties on a crime scene can be confident in their CoC and forensics activities. However, the focus here is on leveraging the trust, security, accessibility, provenance, and transportation of the digital evidence and handling service, the improvement of and investment in supporting law-enforcement institutions, and the investigation of cybercrime.
Existing research
Nowadays, forensic software is used to better acquire evidence that describes and identifies the electronic user, e.g., via the digital signature, audit trail, etc. Still, there is still a significant gap between the usual CoC software and using traceable digital evidence effectively in the courtroom. Nowadays, this process is executed through the concept of CoC. The CoC is a set of consecutive documented records that demonstrate the order of custody for physical or electronic evidence, as well as of its control, transfer, and analysis. Maintaining CoC during the process of investigation and at the time of submitting the evidence in court can be challenging, however. In the past few years, various IoT-based studies have been conducted in forensics[26][27][28][29][30], which includes the identification of the digital evidence, its collection, storage, analysis, and distribution within IoT platforms.[16] This process is entirely different from existing computer-based forensics. Since 2017, blockchain technology has been applied in various applications of digital forensics, such as the documentation of evidence.[31][32][33][34][35][36] Zhang et al.[37] proposed a provenance process model for digital investigations using blockchain in a cloud-based environment, with the idea that it can enhance the interaction trust between stakeholders in cloud forensics. Al-Nemrat[38] investigated the possibility of introducing blockchain-based technologies in the investigation of financial fraud in e-governance. Al-Nemrat's results show that their proposed technology can be effective in determining financial fraud related to the reviews of online products.[38]
Ulybyshev et al.[39] explained that the blockchain is used to provide the process of audibility, traceability in software development, and a role-based access control mechanism for the accesses of unauthorized data. Hossain et al.[40] proposed a forensic investigation framework based on the blockchain, which focuses on detecting various criminal incidents in the IoT and also on collecting the details of communications from different entities present in it. Their proposed framework can model the interaction of transactions. The main drawback of their methodology is its inefficiency in the collection of data and its analysis in large-scale IoT-based systems. Lone and Mir[41] proposed a digital forensic chain based on the popular blockchain platform called Ethereum. Ethereum can provide integrity, transparency, and authenticity for the multiple sources of data. Various studies have been done on the process of digital investigations in the heterogeneous environment[42], security solutions in lightweight IoT devices[22], digital witnesses[31], etc.
From these studies, it appears recent analysis and research on digital forensics falls under two categories: focusing on assisting the law enforcement community and focusing on specific forensics applications. Ćosić and Bača[43] proposed a conceptual digital evidence management framework (DEMF) to improve the CoC of digital evidence in all the phases of the investigation. They used a hash code for the fingerprinting of evidence, assessing hash similarity to change control, identifying biometrics, authenticating digital signatures, performing automatic and trusted timestamping, and running GPS and RFID for geolocation. These components can be implemented through a database to record all the activities performed by the first responders, forensic investigators, verifier or acceptors, law enforcement personnel, and police officers, etc. This work aims at developing a blockchain-based CustodyBlock digital forensic model that can be used in complex cyber environments (such as IoT, cyber-physical systems, etc.) and providing an effective architecture for the proposed methodology.
Research methodology
There are several published forensics models with detailed guidelines for the forensics team. For instance, there is a set of tasks and procedures to maintain the integrity of the captured evidence and avoid contradiction with jurisdictional laws and regulation by maintaining compliance with the applicable law requirements. ISO/IEC 27050-2:2018 is a cybersecurity guidance document that highlights standards and codes of practice for electronic discovery, i.e., eDiscovery, which aims at protecting electronically stored information (ESI), including recorded data by any involved parties in the investigation process. Similarly, the digital forensic research workshop (DFRWS) model is set to protect the digital forensic process, and has six stages that start with the identification phase during an incident/event, followed by preservation, collection, examination, and analysis. Lastly, the collected evidence report is set as part of the presentation phase.[17][44]
This methodology utilizes a grounded and qualitative theory set by Jabareen[17], i.e., the “conceptual framework analysis” approach to building conceptual frameworks. In addition to the current digital investigation models (e.g., ISO/IEC 27050 and DFRWS), Jabareen’s approach is used to devise the CB model. This stipulates identifying a phenomenon’s key factors, which when organized, clarify the proposed solution. Every key factor has its attributes, assumptions, and roles that have a specific function within the proposed model. In addition, three forms of a given assumption are presented:
- the way things are, i.e., ontological;
- how things interact/work, i.e., epistemological; and
- the process in building the conceptual model that fits/understands the real world, i.e., methodological.
The main step in this method is to derive concepts from data within the knowledge base, i.e., literature cases, and inject the deductive procedure to generate the relationship between the model's key factors. The overall process emphasizes an iterative interplay between inductive data and the analysis phases. In the end, this results in arriving at a solid examination of the potential and applicability of blockchain and smart contracts to advance CoC and the digital evidence handling model. Moreover, basic evidence metrics[6] are considered to improve the traceability and evidence sources. This includes location of the data when generated, type and form of data, time elapsed since it was stored, its currently employed control and security measures, who last accessed it, when it was last reviewed, who the owner or responsible entity is, and what the transfer procedure was.
CustodyBlock framework
The CustodyBlock system architecture includes the participants (law enforcement, cloud service providers, validators), a consensus algorithm, a smart contract, cryptographic functions, and a digital signature. The main CustodyBlock model components are shown in Figure 3 and described below.
|
The CustodyBlock model ensures proper CoC documentation in order to allow the admissibility and validity of digital evidence. Participants have many roles and responsibilities within the system. The following are major participating actors in the CustodyBlock model:
- Law enforcement (LE): This is the major player in the model. LE is a trusted third-party or government entity that is tasked with ensuring proper evidence handling procedures, e.g., collection, preservation, analysis, archiving, etc. The LE entity sets the roles for CustodyBlock transactions' read/write controls and ledger read/write controls. LE details the rules needed to be written/coded in smart contracts to automate entity registration and onboarding, e.g., registering digital witnesses and investigators
- Digital witness (DW): This is the interconnected network of devices, such as laptops, smartphones, and IoTs, such as home appliances and connected vehicles, etc. DW provides collaboration on providing incident-based/sensor-based evidence within their capabilities. The captured evidence puts investigators and LE forward for further investigation.
Digital evidence custody (DEC)
An approved and accredited administrative person or entity is required to ensure the proper handling of the evidence received from investigators, LE, or authorized trusted law enforcement entities. DEC can be automated through the use of smart contracts and machine learning algorithms. In this case, the "blockchain fabric" (BF) is used.
BF describes the private blockchain implementation using, e.g., Ethereum or Hyperledger fabric as the main underlying system for the CustodyBlock application. Participating roles and responsibilities act as active nodes of the CustodyBlock blockchain network. The BF contains an essential element to this structure, i.e., the shared ledger or DLT, which will be able to log all collective and transferred evidence and immutability shared among all the different and authorized entities. The DLT is governed by lawmakers and law enforcement institutes.
The BF has three sub-functions, which together form the operation of the BF. These are:
- 1. Secure transaction: This carries the evidence track records, e.g., submission, archiving, transfer, fetching, etc. Each transaction entails necessary information and a unique identifier. Information details are set as per forensic investigation standards to include data type, timestamp, submitter and receiver IDs, geographical locations, etc. The transaction is then hashed, and once verified by the consensus algorithm, will be stored in the CustodyBlock DLT and distributed among all active network nodes.
- 2. Smart contract: Each transaction can be automated using a smart contract. A smart contract is a set of predetermined executable instructions based on the nature of a certain transaction or input. An output can also trigger another smart contract. For example, a case is created, and the smart contract logs the submitter ID and associated evidence provided by the analysis phase. Based on the analysis output, the smart contract initiates another instance to request more evidence from the submitter or witnesses. If the submitted evidence is sufficient for the case, then the smart contract proceeds to the analysis and investigation procedures. Additional steps in the investigation process, e.g., evidence transfer and archival, are not presented in this paper.
- 3. Consensus node: This is a function with a set of rules that is responsible for maintaining, verifying, and approving BF records/transactions and updating the ledger. It also ensures trustworthiness when reliability, availability, accuracy, and authenticity are built in by design. The on-chain governance of the CustodyBlock blockchain is achieved by consensus nodes by not only restricting access to the CustodyBlock ledger, but also who can perform different actions, e.g., validation of transactions. There are different implementations of consensus algorithms, such as proof of work (PoW), proof of stake (PoS), delegated proof of stake (DPoS), practical byzantine fault tolerance (pBFT), proof of authority (PoA), etc. A private (permissioned) implementation of the CustodyBlock model is suggested with the use of practical byzantine fault tolerance (pBFT) as a consensus algorithm. The pBFT is considered for the CustodyBlock model with the assumption that some of the consensus nodes may act faultily or maliciously in the network, hence the need for taking proactive measures to ensure consistent and valid voting/validation, shown in Figure 4. The pBFT does not scale to accommodate other blockchains or larger volume, but for maintaining evidence handling, the author believes it should suffice.
|
The given process achieves consensus if the majority of the CB network nodes agree on the same output value. The pBFT phases are:
- A “request” for evidence handling procedure is received.
- A “pre-prepare” phase includes this shared request in a proposal.
- A “prepare” phase is set for voting/validating and coming to an agreement.
- A “commit” phase allows each consensus node to communicate to each other their results, and the majority agreed-upon value will be committed into the ledger and updated in the whole CB network.
Algorithm for the proposed methodology
The following programing is the pseudo code of the algorithm of the proposed mechanism using Python and the Hyperledger platform. Our algorithm creates a number of blocks with different hashes and with timestamps to approve, verify, and track the transactions made by the blocks. The blocks’ authentication uses public key infrastructure (PKI) with smart contracts to approve the creation of the created evidence. Figure 5 shows the flowchart of the proposed algorithm.
|
The mathematical model and algorithm are inspired by the work of Giova[2] and Tang et al.[45] The following is the pseudo Algorithm 1 of our proposed algorithm, which was also created in advance by the Hyperledger platform:
| ||||
Discussion and further applications
The CB model can be used in different applications, such as private blockchain or IoT applications. This model is a novel technique inspired by the Hyperledger technology supported by the Linux Foundation and IBM, which uses smart contracts and public key infrastructure (PKI) to achieve confidentiality, integrity, availability, authentication, and authorization. PKI-based solutions encrypt the transaction transmitted from the authorized source peer to the destination. The proposed model can be used to authenticate IoT users and devices to avoid different kinds of inside and outside threads and attacks.
Blockchain is a decentralization technology that stores the data and the transactions into distributed peer-to-peer blocks. These blocks can be used to create and verify transactions using hashing and cryptographic algorithms. New technologies such as zero-knowledge proof (ZKP) are adding even more security to blockchain technology by using a third party, called the “prover,” who can prove and verify the value without getting any information about the transaction while only possessing the secret information.[46][47][48] In fact, Liu et al.[14] used ZKP and multi-factor authentication in 2019 to secure the verifier's identity. This method is promising and may also be used in many IoT devices and applications. However, the following three properties need to be satisfied for the method to work[49]:
- Completeness: Knowing a spectator and the authenticity of a statement, the prover can convince the verifier.
- Soundness: A malicious prover cannot persuade the verifier in the situation that the assertion is bogus.
- Zero-information: The verifier asserts nothing aside from the fact that the assertion is valid.
Conclusions and future work
In this paper, a blockchain-based protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring have been proposed. The proposed method utilizes a conceptual blockchain model using novel CoC technology, along with the CB model using private blockchain protocol and smart contracts, to fill the gap in the literature and address the challenges faced in handling digital evidence to efficiently transform global legal practices. The CB model demonstrates how blockchain and smart contracts can provide monitored and traceable access to the evidence chain for those involved participants, e.g., regulators, courts, law firms, etc. To ensure security in sharing the forensic data, the proposed mechanism ensures that all participating entities are authorized to exchange and share the data. The proposed model provides the platform on which the forensic data can be stored without any attacks and acts as a better and more secure evidence preservation and handling methodology.
Future enhancements to this model can be imagined. For example, intelligent-based methods can be combined with the blockchain for providing privacy and security in electronic data. Additional benefits could be had with the addition of biometric-based systems.
In the future, CoC technology can be used for IoT smart home and healthcare applications to add security. In situations like the COVID-19 pandemic—where rapid, accurate, and secure information is vital to effective treatments—this model has the potential to help patients and the treatment team by better securing point-of-care and IoT medical devices, electronic health records (EHRs), patient healthcare information (PHI), and other healthcare applications. In the future, we would like to conduct a case study comparing the proposed CB model with a zero-knowledge proof (ZKP) model for smart home IoT applications using multi-factor authentication to secure the IoT user’s identity.
Acknowledgements
Funding
This research received no external funding.
Data availability
Data available on request due to restrictions e.g., privacy or ethical.
Conflict of interest
The author declares no conflict of interest.
References
- ↑ Adam, Iliyasu Yahaya; Varol, Cihan (1 June 2020). "Intelligence in Digital Forensics Process". 2020 8th International Symposium on Digital Forensics and Security (ISDFS) (Beirut, Lebanon: IEEE): 1–6. doi:10.1109/ISDFS49300.2020.9116442. ISBN 978-1-7281-6939-2. https://ieeexplore.ieee.org/document/9116442/.
- ↑ 2.0 2.1 Giova, G. (2011). "Improving Chain of Custody in Forensic Investigation of Electronic Digital Systems". International Journal of Computer Science and Network Security 11 (1): 1–9. http://paper.ijcsns.org/07_book/html/201101/201101001.html.
- ↑ Bali, Jatinder; Garg, Rohit; Bali, RenuT (2019). "Artificial intelligence (AI) in healthcare and biomedical research: Why a strong computational/AI bioethics framework is required?" (in en). Indian Journal of Ophthalmology 67 (1): 3. doi:10.4103/ijo.IJO_1292_18. ISSN 0301-4738. PMC PMC6324122. PMID 30574881. https://journals.lww.com/10.4103/ijo.IJO_1292_18.
- ↑ 4.0 4.1 Sabir, B. E.; Youssfi, M.; Bouattane, O.; Allali, H. (4 April 2020). "Towards a New Model to Secure IoT-based Smart Home Mobile Agents using Blockchain Technology". Engineering, Technology & Applied Science Research 10 (2): 5441–5447. doi:10.48084/etasr.3394. ISSN 1792-8036. https://etasr.com/index.php/ETASR/article/view/3394.
- ↑ Zheng, Zibin; Xie, Shaoan; Dai, Hong Ning; Chen, Xiangping; Wang, Huaimin (2018). "Blockchain challenges and opportunities: a survey" (in en). International Journal of Web and Grid Services 14 (4): 352–75. doi:10.1504/IJWGS.2018.095647. ISSN 1741-1106. http://www.inderscience.com/link.php?id=95647.
- ↑ 6.0 6.1 Zhang, Yu; Wen, Jiangtao (1 July 2017). "The IoT electric business model: Using blockchain technology for the internet of things" (in en). Peer-to-Peer Networking and Applications 10 (4): 983–994. doi:10.1007/s12083-016-0456-1. ISSN 1936-6442. http://link.springer.com/10.1007/s12083-016-0456-1.
- ↑ 7.0 7.1 Ramezan, Gholamreza; Leung, Cyril (1 November 2018). "A Blockchain-Based Contractual Routing Protocol for the Internet of Things Using Smart Contracts" (in en). Wireless Communications and Mobile Computing 2018: 1–14. doi:10.1155/2018/4029591. ISSN 1530-8669. https://www.hindawi.com/journals/wcmc/2018/4029591/.
- ↑ Bozic, Nikola; Pujolle, Guy; Secci, Stefano (1 December 2016). "A tutorial on blockchain and applications to secure network control-planes". 2016 3rd Smart Cloud Networks & Systems (SCNS) (Dubai, United Arab Emirates: IEEE): 1–8. doi:10.1109/SCNS.2016.7870552. ISBN 978-1-5090-4476-4. http://ieeexplore.ieee.org/document/7870552/.
- ↑ Pavithran, Deepa; Shaalan, Khaled; Al-Karaki, Jamal N.; Gawanmeh, Amjad (1 September 2020). "Towards building a blockchain framework for IoT" (in en). Cluster Computing 23 (3): 2089–2103. doi:10.1007/s10586-020-03059-5. ISSN 1386-7857. http://link.springer.com/10.1007/s10586-020-03059-5.
- ↑ Yang, Wenli; Aghasian, Erfan; Garg, Saurabh; Herbert, David; Disiuta, Leandro; Kang, Byeong (2019). "A Survey on Blockchain-Based Internet Service Architecture: Requirements, Challenges, Trends, and Future". IEEE Access 7: 75845–75872. doi:10.1109/ACCESS.2019.2917562. ISSN 2169-3536. https://ieeexplore.ieee.org/document/8717702/.
- ↑ Mamdouh, Moustafa; Awad, Ali Ismail; Hamed, Hesham F. A.; Khalaf, Ashraf A. M. (2020), Hassanien, Aboul-Ella; Azar, Ahmad Taher; Gaber, Tarek et al.., eds., "Outlook on Security and Privacy in IoHT: Key Challenges and Future Vision" (in en), Proceedings of the International Conference on Artificial Intelligence and Computer Vision (AICV2020) (Cham: Springer International Publishing) 1153: 721–730, doi:10.1007/978-3-030-44289-7_67, ISBN 978-3-030-44288-0, http://link.springer.com/10.1007/978-3-030-44289-7_67. Retrieved 2022-06-28
- ↑ Ernest, Bonnah; Shiguang, Ju (2020). "Privacy Enhancement Scheme (PES) in a Blockchain-Edge Computing Environment". IEEE Access 8: 25863–25876. doi:10.1109/ACCESS.2020.2968621. ISSN 2169-3536. https://ieeexplore.ieee.org/document/8966296/.
- ↑ Kim, Hyunil; Kim, Seung-Hyun; Hwang, Jung Yeon; Seo, Changho (2019). "Efficient Privacy-Preserving Machine Learning for Blockchain Network". IEEE Access 7: 136481–136495. doi:10.1109/ACCESS.2019.2940052. ISSN 2169-3536. https://ieeexplore.ieee.org/document/8827509/.
- ↑ 14.0 14.1 Liu, Wenzheng; Wang, Xiaofeng; Peng, Wei (2020). "Secure Remote Multi-Factor Authentication Scheme Based on Chaotic Map Zero-Knowledge Proof for Crowdsourcing Internet of Things". IEEE Access 8: 8754–8767. doi:10.1109/ACCESS.2019.2962912. ISSN 2169-3536. https://ieeexplore.ieee.org/document/8945237/.
- ↑ Alfandi, Omar; Otoum, Safa; Jararweh, Yaser (1 April 2020). "Blockchain Solution for IoT-based Critical Infrastructures: Byzantine Fault Tolerance". NOMS 2020 - 2020 IEEE/IFIP Network Operations and Management Symposium (Budapest, Hungary: IEEE): 1–4. doi:10.1109/NOMS47738.2020.9110312. ISBN 978-1-7281-4973-8. https://ieeexplore.ieee.org/document/9110312/.
- ↑ 16.0 16.1 Khan, Z. Faizal; Alotaibi, Sultan Refa (2020). "Applications of Artificial Intelligence and Big Data Analytics in m-Health: A Healthcare System Perspective" (in en). Journal of Healthcare Engineering 2020: 8894694. doi:10.1155/2020/8894694. ISSN 2040-2295. PMC PMC7481991. PMID 32952992. https://www.hindawi.com/journals/jhe/2020/8894694/.
- ↑ 17.0 17.1 17.2 17.3 17.4 17.5 Jabareen, Yosef (1 December 2009). "Building a Conceptual Framework: Philosophy, Definitions, and Procedure" (in en). International Journal of Qualitative Methods 8 (4): 49–62. doi:10.1177/160940690900800406. ISSN 1609-4069. http://journals.sagepub.com/doi/10.1177/160940690900800406.
- ↑ Singh, Kumar Shanu; Irfan, Annie; Dayal, Neelam (1 November 2019). "Cyber Forensics and Comparative Analysis of Digital Forensic Investigation Frameworks". 2019 4th International Conference on Information Systems and Computer Networks (ISCON) (Mathura, India: IEEE): 584–590. doi:10.1109/ISCON47742.2019.9036214. ISBN 978-1-7281-3651-6. https://ieeexplore.ieee.org/document/9036214/.
- ↑ Sun, Xia; Zou, Jinglin; Li, Li; Luo, Min (1 February 2021). "A blockchain-based online language learning system" (in en). Telecommunication Systems 76 (2): 155–166. doi:10.1007/s11235-020-00699-1. ISSN 1018-4864. https://link.springer.com/10.1007/s11235-020-00699-1.
- ↑ 20.0 20.1 Tiwari, V.; Keskar, A.; Shivaprakash, N. C. (24 April 2017). "Design of an IoT Enabled Local Network Based Home Monitoring System with a Priority Scheme". Engineering, Technology & Applied Science Research 7 (2): 1464–1472. doi:10.48084/etasr.1033. ISSN 1792-8036. https://etasr.com/index.php/ETASR/article/view/1033.
- ↑ 21.0 21.1 Reedy, Paul (2020). "Interpol review of digital evidence 2016 - 2019" (in en). Forensic Science International: Synergy 2: 489–520. doi:10.1016/j.fsisyn.2020.01.015. PMC PMC7770434. PMID 33385144. https://linkinghub.elsevier.com/retrieve/pii/S2589871X20300152.
- ↑ 22.0 22.1 Aziz, Benjamin; Blackwell, Clive; Islam, Shareeful (1 April 2013). "A Framework for Digital Forensics and Investigations: The Goal-Driven Approach" (in ng). International Journal of Digital Crime and Forensics 5 (2): 1–22. doi:10.4018/jdcf.2013040101. ISSN 1941-6210. https://services.igi-global.com/resolvedoi/resolve.aspx?doi=10.4018/jdcf.2013040101.
- ↑ Mante, R. V.; Khan, Reshma (1 March 2020). "A Survey on Video-based Evidence Analysis and Digital Forensic". 2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC) (Erode, India: IEEE): 118–121. doi:10.1109/ICCMC48092.2020.ICCMC-00024. ISBN 978-1-7281-4889-2. https://ieeexplore.ieee.org/document/9076417/.
- ↑ Carrier, B.D.; Spafford, E.H. (2004). "An Event-Based Digital Forensic Investigation Framework". Proceedings of the 2004 Digital Forensic Research Workshop: CERIAS TR 2004-53. https://www.cerias.purdue.edu/apps/reports_and_papers/view/2762.
- ↑ Zhang, Ning; Zhong, Shan; Tian, Li (4 December 2017). "Using Blockchain to Protect Personal Privacy in the Scenario of Online Taxi-hailing". International Journal of Computers Communications & Control 12 (6): 886–902. doi:10.15837/ijccc.2017.6.2886. ISSN 1841-9836. http://univagora.ro/jour/index.php/ijccc/article/view/2886.
- ↑ Hossain, Mahmud; Hasan, Ragib; Zawoad, Shams (1 June 2017). "Trust-IoV: A Trustworthy Forensic Investigation Framework for the Internet of Vehicles (IoV)". 2017 IEEE International Congress on Internet of Things (ICIOT) (Honolulu, HI, USA: IEEE): 25–32. doi:10.1109/IEEE.ICIOT.2017.13. ISBN 978-1-5386-2011-3. http://ieeexplore.ieee.org/document/8039051/.
- ↑ Hossain, Mahmud; Hasan, Ragib; Zawoad, Shams (1 April 2018). "Probe-IoT: A public digital ledger based forensic investigation framework for IoT". IEEE INFOCOM 2018 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) (Honolulu, HI: IEEE): 1–2. doi:10.1109/INFCOMW.2018.8406875. ISBN 978-1-5386-5979-3. https://ieeexplore.ieee.org/document/8406875/.
- ↑ Li, Wanxin; Guo, Hao; Nejad, Mark; Shen, Chien-Chung (2020). "Privacy-Preserving Traffic Management: A Blockchain and Zero-Knowledge Proof Inspired Approach". IEEE Access 8: 181733–181743. doi:10.1109/ACCESS.2020.3028189. ISSN 2169-3536. https://ieeexplore.ieee.org/document/9210529/.
- ↑ Perdana, Arif; Robb, Alastair; Balachandran, Vivek; Rohde, Fiona (1 April 2021). "Distributed ledger technology: Its evolutionary path and the road ahead" (in en). Information & Management 58 (3): 103316. doi:10.1016/j.im.2020.103316. https://linkinghub.elsevier.com/retrieve/pii/S0378720620302494.
- ↑ Shah, Makhdoom; Saleem, Shahzad; Zulqarnain, Roha (2017). "Protecting Digital Evidence Integrity and Preserving Chain of Custody". The Journal of Digital Forensics, Security and Law 12: 12. doi:10.15394/jdfsl.2017.1478. https://commons.erau.edu/jdfsl/vol12/iss2/12/.
- ↑ 31.0 31.1 Cebe, Mumin; Erdin, Enes; Akkaya, Kemal; Aksu, Hidayet; Uluagac, Selcuk (1 October 2018). "Block4Forensic: An Integrated Lightweight Blockchain Framework for Forensics Applications of Connected Vehicles". IEEE Communications Magazine 56 (10): 50–57. doi:10.1109/MCOM.2018.1800137. ISSN 0163-6804. https://ieeexplore.ieee.org/document/8493118/.
- ↑ Van Der Horst, Luuc; Choo, Kim-Kwang Raymond; Le-Khac, Nhien-An (2017). "Process Memory Investigation of the Bitcoin Clients Electrum and Bitcoin Core". IEEE Access 5: 22385–22398. doi:10.1109/ACCESS.2017.2759766. ISSN 2169-3536. http://ieeexplore.ieee.org/document/8058429/.
- ↑ Liu, Zhe; Seo, Hwajeong (1 March 2019). "IoT-NUMS: Evaluating NUMS Elliptic Curve Cryptography for IoT Platforms". IEEE Transactions on Information Forensics and Security 14 (3): 720–729. doi:10.1109/TIFS.2018.2856123. ISSN 1556-6013. https://ieeexplore.ieee.org/document/8410894/.
- ↑ Ritzdorf, Hubert; Soriente, Claudio; Karame, Ghassan O.; Marinovic, Srdjan; Gruber, Damian; Capkun, Srdjan (1 December 2018). "Toward Shared Ownership in the Cloud". IEEE Transactions on Information Forensics and Security 13 (12): 3019–3034. doi:10.1109/TIFS.2018.2837648. ISSN 1556-6013. https://ieeexplore.ieee.org/document/8360480/.
- ↑ Tziakouris, Giannis (1 July 2018). "Cryptocurrencies—A Forensic Challenge or Opportunity for Law Enforcement? An INTERPOL Perspective". IEEE Security & Privacy 16 (4): 92–94. doi:10.1109/MSP.2018.3111243. ISSN 1540-7993. https://ieeexplore.ieee.org/document/8425619/.
- ↑ Wu, Shuangke; Chen, Yanjiao; Wang, Qian; Li, Minghui; Wang, Cong; Luo, Xiangyang (1 July 2019). "CReam: A Smart Contract Enabled Collusion-Resistant e-Auction". IEEE Transactions on Information Forensics and Security 14 (7): 1687–1701. doi:10.1109/TIFS.2018.2883275. ISSN 1556-6013. https://ieeexplore.ieee.org/document/8543821/.
- ↑ Zhang, Yong; Wu, Songyang; Jin, Bo; Du, Jiaying (1 December 2017). "A blockchain-based process provenance for cloud forensics". 2017 3rd IEEE International Conference on Computer and Communications (ICCC) (Chengdu: IEEE): 2470–2473. doi:10.1109/CompComm.2017.8322979. ISBN 978-1-5090-6352-9. http://ieeexplore.ieee.org/document/8322979/.
- ↑ 38.0 38.1 Al-Nemrat, Ameer (1 April 2018). "Identity theft on e-government/e-governance & digital forensics". 2018 International Symposium on Programming and Systems (ISPS) (Algiers: IEEE): 1–1. doi:10.1109/ISPS.2018.8378961. ISBN 978-1-5386-4690-8. https://ieeexplore.ieee.org/document/8378961/.
- ↑ Ulybyshev, Denis; Villarreal-Vasquez, Miguel; Bhargava, Bharat; Mani, Ganapathy; Seaberg, Steve; Conoval, Paul; Pike, Robert; Kobes, Jason (1 July 2018). "(WIP) Blockhub: Blockchain-Based Software Development System for Untrusted Environments". 2018 IEEE 11th International Conference on Cloud Computing (CLOUD) (San Francisco, CA: IEEE): 582–585. doi:10.1109/CLOUD.2018.00081. ISBN 978-1-5386-7235-8. https://ieeexplore.ieee.org/document/8457849/.
- ↑ Hossain, Mahmud; Karim, Yasser; Hasan, Ragib (1 July 2018). "FIF-IoT: A Forensic Investigation Framework for IoT Using a Public Digital Ledger". 2018 IEEE International Congress on Internet of Things (ICIOT) (San Francisco, CA: IEEE): 33–40. doi:10.1109/ICIOT.2018.00012. ISBN 978-1-5386-7244-0. https://ieeexplore.ieee.org/document/8473437/.
- ↑ Lone, Auqib Hamid; Mir, Roohie Naaz (1 March 2019). "Forensic-chain: Blockchain based digital forensics chain of custody with PoC in Hyperledger Composer" (in en). Digital Investigation 28: 44–55. doi:10.1016/j.diin.2019.01.002. https://linkinghub.elsevier.com/retrieve/pii/S174228761830344X.
- ↑ Caviglione, Luca; Wendzel, Steffen; Mazurczyk, Wojciech (1 November 2017). "The Future of Digital Forensics: Challenges and the Road Ahead". IEEE Security & Privacy 15 (6): 12–17. doi:10.1109/MSP.2017.4251117. ISSN 1540-7993. http://ieeexplore.ieee.org/document/8123473/.
- ↑ Ćosić, J.; Bača, M. (2010). "A framework to (Im)Prove "Chain of Custody" in Digital Investigation Process". Proceedings of the 21st Central European Conference on Information and Intelligent Systems: 435–38. http://archive.ceciis.foi.hr/app/index.php/ceciis/2010/schedConf/presentations.
- ↑ 44.0 44.1 Zhang, Xiaolu; Choo, Kim-Kwang Raymond; Beebe, Nicole Lang (1 August 2019). "How Do I Share My IoT Forensic Experience With the Broader Community? An Automated Knowledge Sharing IoT Forensic Platform". IEEE Internet of Things Journal 6 (4): 6850–6861. doi:10.1109/JIOT.2019.2912118. ISSN 2327-4662. https://ieeexplore.ieee.org/document/8694855/.
- ↑ Tang, Huanrong; Sun, Yaojing; Ouyang, Jianquan (2020). "Excellent Practical Byzantine Fault Tolerance" (in en). Journal of Cyber Security 2 (4): 167–182. doi:10.32604/jcs.2020.011341. ISSN 2579-0064. https://www.techscience.com/JCS/v2n4/40714.
- ↑ Wang, Dan; Zhao, Jindong; Wang, Yingjie (2020). "A Survey on Privacy Protection of Blockchain: The Technology and Application". IEEE Access 8: 108766–108781. doi:10.1109/ACCESS.2020.2994294. ISSN 2169-3536. https://ieeexplore.ieee.org/document/9093015/.
- ↑ Raikwar, Mayank; Gligoroski, Danilo; Kralevska, Katina (2019). "SoK of Used Cryptography in Blockchain". IEEE Access 7: 148550–148575. doi:10.1109/ACCESS.2019.2946983. ISSN 2169-3536. https://ieeexplore.ieee.org/document/8865045/.
- ↑ Partala, Juha; Nguyen, Tri Hong; Pirttikangas, Susanna (2020). "Non-Interactive Zero-Knowledge for Blockchain: A Survey". IEEE Access 8: 227945–227961. doi:10.1109/ACCESS.2020.3046025. ISSN 2169-3536. https://ieeexplore.ieee.org/document/9300214/.
- ↑ Nieto, Ana; Roman, Rodrigo; Lopez, Javier (1 November 2016). "Digital Witness: Safeguarding Digital Evidence by Using Secure Architectures in Personal Devices". IEEE Network 30 (6): 34–41. doi:10.1109/MNET.2016.1600087NM. ISSN 0890-8044. http://ieeexplore.ieee.org/document/7764297/.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added. The original uses "DC" in the text but fails to establish what it means. It's also not clear what it means after looking at the figures. This version assumes it means "investigators." The original mistakenly omitted a citation for Liu et al. 2019 in the discussion; it was added for this version.