Difference between revisions of "Journal:Registered data-centered lab management system based on data ownership security architecture"
Shawndouglas (talk | contribs) (Saving and adding more.) |
Shawndouglas (talk | contribs) (Saving and adding more.) |
||
| Line 116: | Line 116: | ||
|} | |} | ||
However, DOSA-related studies have designed models for some domains such as tourism, which only have frameworks without practical implementation. [9] We propose to use technical methods to solve data ownership by binding persons that used a key management system to protect [[Information privacy|data privacy]]. | |||
===Key system methods=== | |||
To ensure data registration and sharing security, this work adopted RSA and AES algorithms, as well as Chinese domestic commercial keys SM2 and SM4, to compare the aspects of addressing efficiency and security of data. Table 2 summarizes the pros and cons of these key algorithms. | |||
{| | |||
| style="vertical-align:top;" | | |||
{| class="wikitable" border="1" cellpadding="5" cellspacing="0" width="100%" | |||
|- | |||
| colspan="4" style="background-color:white; padding-left:10px; padding-right:10px;" |'''Table 2.''' Comparison of the four key algorithms examined in this research. | |||
|- | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;" |Algorithm | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;" |Description | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;" |Advantage | |||
! style="background-color:#dddddd; padding-left:10px; padding-right:10px;" |Disadvantage | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |'''RSA''' | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Asymmetric encryption that encrypts with public key; decrypts with private key [20] | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |In the process of encryption and decryption, there is no need to transmit confidential keys through the network. The key management is better than the AES algorithm. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |The speed of encryption and decryption is relatively slow; usually it is not suitable for the encryption of a large number of data files. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |'''AES''' | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Symmetric encryption algorithm; encryption and decryption processes use the same set of keys | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |The operation does not require a computer with very high processing power and significant memory. The operation resists attacks easily. It always maintains good performance in different operating environments; the encryption speed is relatively fast. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |It is required to secretly distribute the key before communication. The decrypted private key must be transmitted to the receiver of the encrypted data through the network. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |'''SM2''' | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Asymmetric encryption algorithm which is an elliptic curve public key cryptography algorithm based on elliptic-curve cryptography (ECC) [21] | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Compared with RSA, the performance of SM2 is better and more secure. The password complexity is high, the processing speed is fast, and the computer performance consumption is comparatively small. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Encryption and decryption take a relatively long time and are suitable for encrypting small amounts of data. | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |'''SM4''' | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |Symmetric encryption algorithm; the key length and block length are both 128 bits | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |SM4 is efficient and secure, while remaining easy to implement across software and hardware. It usually has a fast computing speed. | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |The management and distribution of keys are relatively difficult and not secure enough. | |||
|- | |||
|} | |||
|} | |||
SM2 and SM4 are cryptographic standards authorized to be used in China. Relevant studies have shown that the SM2 and SM4 algorithms are more secure than ECDSA and AES. [22] During a controlled experiment, AES outperformed SM4 by a significant margin. [23] Symmetric encryption is usually used when the message sender needs to encrypt a large amount of data. It has the characteristics of an open algorithm, a small amount of calculation, and fast encryption speed. The advantage of the symmetric encryption algorithm lies in the high speed of encryption and decryption, and the difficulty of cracking when using a long key. The disadvantages of symmetric encryption are that key management and distribution are difficult and insecure. Before the data are transmitted, the sender and the receiver must agree on a secret key, and both parties must keep the key. If the key of one party is leaked, the encrypted information is insecure, and its security cannot be guaranteed. [24] | |||
The advantage of asymmetric encryption is its higher security. The public key is made available, and the private key is kept by itself so there is no need to give the private key to others. The disadvantage of asymmetric encryption is that its speed is relatively slow, so it is only suitable for encrypting a small amount of data. | |||
==Methodology== | |||
===Laboratory-related management data and persons=== | |||
Revision as of 22:01, 28 July 2023
| Full article title | Registered data-centered lab management system based on data ownership security architecture |
|---|---|
| Journal | Electronics |
| Author(s) | Zheng, Xuying; Miao, Fang; Udomwong, Piyachat; Chakpitak, Nopasit |
| Author affiliation(s) | Chiangmai University, Chengdu University |
| Primary contact | Email: nopasit at cmuic dot net |
| Year published | 2023 |
| Volume and issue | 12(8) |
| Article # | 1817 |
| DOI | 10.3390/electronics12081817 |
| ISSN | 2079-9292 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2079-9292/12/8/1817 |
| Download | https://www.mdpi.com/2079-9292/12/8/1817/pdf?version=1681215589 (PDF) |
|
|
This article should be considered a work in progress and incomplete. Consider this article incomplete until this notice is removed. |
Abstract
University and college laboratories are important places to train professional and technical personnel. Various regulatory departments in colleges and universities still rely on traditional laboratory management in research projects, which are prone to problems such as untimely information and data transmission. The present study aimed to propose a new method to solve the problem of data islands, explicit ownership, conditional sharing, data security, and efficiency during laboratory data management. Hence, this study aimed to develop a data-centered lab management system that enhances the security of laboratory data management and allows the data owners of the labs to control data sharing with other users. The architecture ensures data privacy by binding data ownership with a person using a key management method. To achieve secure data flow, data ownership conversion through the process of authorization and confirmation was introduced. The designed lab management system enables laboratory regulatory departments to receive data in a secure form by using this platform, which could solve data sharing barriers. Finally, the proposed system was applied and run in different server environments by implementing data security registration, authorization, confirmation, and conditional sharing using SM2, SM4, RSA, and AES algorithms. The system was evaluated in terms of the execution time for several lab data with different sizes. The findings of this study indicate that the proposed strategy is secure and efficient for lab data sharing across domains.
Keywords: university laboratory management, data sharing, data ownership safety architecture, conditional sharing, security and efficiency
Introduction
The importance of knowledge for organizations is now widely recognized, being one of the resources whose management influences the success of organizations through the exchange and sharing of information, knowledge, and experience among its members. Numerous challenges are associated with the management of laboratory data, as labs generate a lot of experimental and management data on a daily basis. Frequent experimental accidents and the leakage of hazardous chemicals is worthy of attention. Supervision departments, such as the Education Bureau, Emergency Bureau, and Public Security Department, need various types of laboratory management data to report while supervising laboratory safety.
At present, existing laboratory management systems used by each university, regulatory department, and even various laboratories are different, which leads to obvious problems when lab data collection or emergency response is needed. For example, which laboratory management data are classified confidential, and which data can be handed over to relevant departments? Who must claim the ownership of laboratory-related data? Which departments can view or use the data? Could lab data be transferred to other departments? These questions raised laboratory data ownership issues. Secondly, some data that relate to laboratory management need to be kept confidential. Where and how can we best secure this data? Is it safe for different departments to transmit data? How can we guarantee that there will be no data transfer to others? These can be summarized as data security storage and transmission questions. In recent years, frequent university laboratory accidents have occurred; in such cases, emergency responding units and other regulatory departments need to collect real-time lab-related data. If it is still a regular report retrieval process, it cannot meet the requirements of time efficiency. So, we need to find efficient and trustworthy methods to solve this problem of obtaining data in a timely manner.
The main reason for the above problems is that laboratory management data ownership is unclear, and the existing laboratory information management systems (LIMS) of each branch are independent. It is impossible to collect real-time, tamper-free, statistically accurate data when it is needed. To deal with these problems, we intend to adopt data ownership security architecture (DOSA) to securely circulate laboratory management data and cultivate an ecological and sustainable forest from the “flowerpot” of each independent system. [1]
Laboratories are currently using LIMS frequently. [2] A university may also have multiple management systems, including an equipment management system, a chemical management system, a safety examination system, etc. Related systems comprise relevant departments of the laboratory, such as the experiment management department of the Education Bureau, the accident handling department of the Emergency Bureau, and the hazardous chemicals supervision department of Public Security. Such complicated systems make it difficult to obtain information accurately and quickly when the same report requires the cooperation of different departments or laboratories. Compared to traditional manual records, the LIMS used by a specific business unit or company can be easily outdated and has high maintenance costs. Once the database needs major updates related to its data source, the existing system cannot meet the demand, and a new system must be designed so that all data can be transferred, resulting in increased costs. The linkage between different systems is weak, the efficiency is relatively low, and the security is not uniform and difficult to guarantee when it is necessary to submit data.
Blockchain poses one potential solution. The medical industry uses the blockchain system to manage medical imaging data, and the banking system uses blockchain as a new type of financial technology. [3] Blockchain has high energy consumption, expensive development costs, but relatively high security. At present, some scholars have produced a framework diagram of the blockchain management in university education, but there is no corresponding technical means. [4]
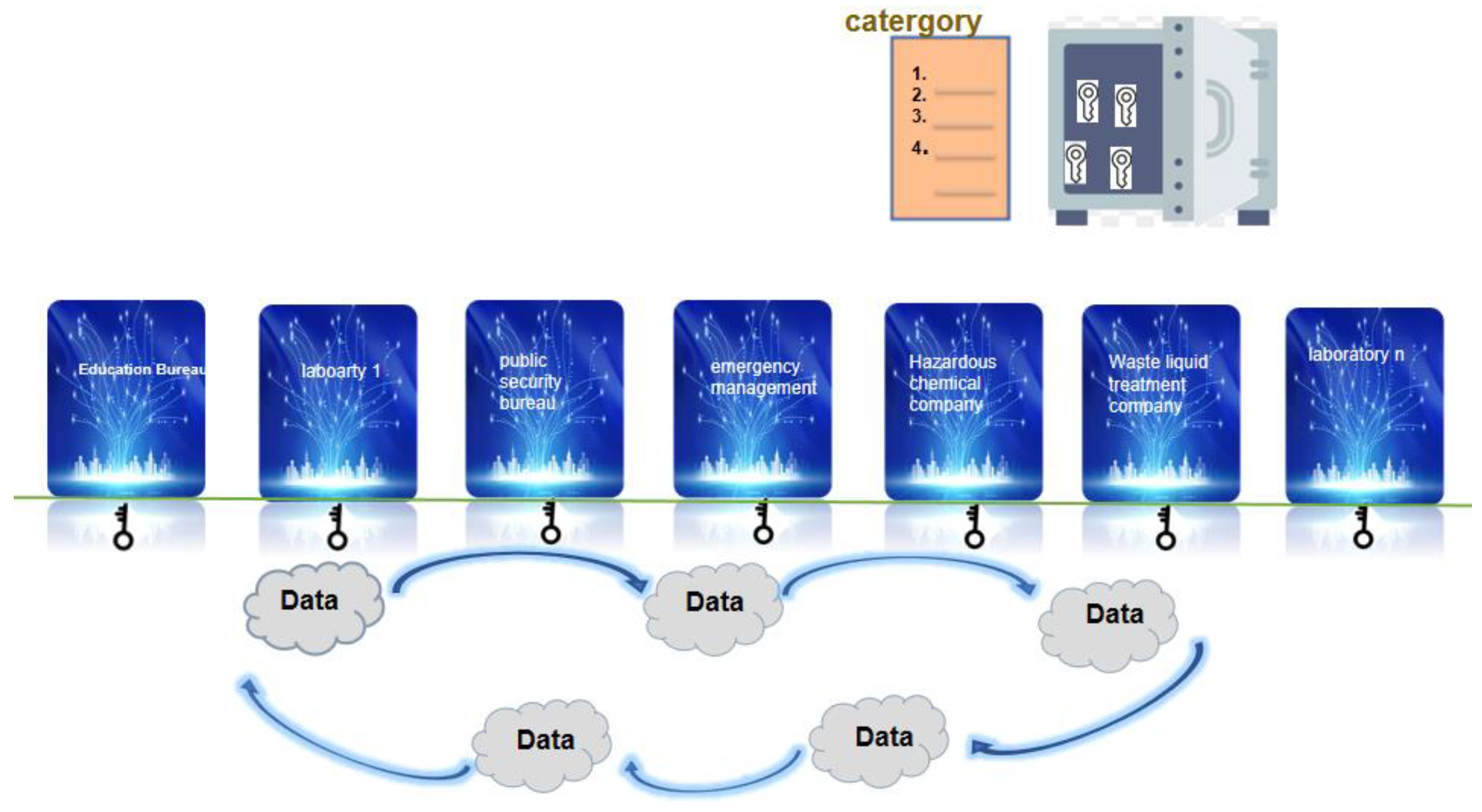
Considering the problems mentioned above, the lab industry would require a technology that allows data to flow securely and efficiently. This article’s contributes discussion about potential technology to solve such problems. In our work, experiment-related data management is based on the data ownership security architecture. This security technology is built such that data ownership binds with a person and it can be safely registered on this platform; meanwhile, ownership of data can be determined, and data users and owners can conditionally share or trade using ownership conversion across domains and across borders efficiently and securely. Our proposed laboratory data management architecture is shown in Figure 1.
|
The current study has been organized as follows. The next section explains related theories and key management. After that, we present the core strategies used, including laboratory data encrypted registration and an authorized transfer method for conditional sharing. We then detail the whole lab management framework and the incident searching case study based on DOSA using the above ownership conversion method. We then discuss and verify the effectiveness of the data flow process using key management based on proposed core strategies. Finally, we provide our conclusions.
Related work
Data ownership security architecture
As data has a tendency to not be securely circulated and shared, Miao et al. proposed a data ownership security architecture (DOSA) that contains one body with two wings. [5] The body represents data binding ownership, while one wing is the key and the other wing signifies value.
To solve the problem of data transfer barriers, DOSA proposes a global, cross-border, comprehensive, collaborative, secure, and efficient data architecture system. The whole field is no longer the cross-domain data of the head industry or a single system as previous, but all industry-related data are registered. Integration and collaboration mean that data are retrieved and used by different industry sources. This architecture has efficient security technologies for data security from source, registration, circulation, and use to supervision.
DOSA is composed of a data registration center (DRC), a data authorization center (DAC), a data exception center (DEC), data application units (DAUs), a key system, and other components. Safety and efficiency are the core of DOSA. Similar DOSA-like framework applications have been implemented in tourism, lab education, and data product trading processes. [9,10]
DRC
The DRC stores the data in an encrypted form, which is invisible even to the administrator. It not only confirms the ownership of the data but also keeps it safe and confidential. After the data are registered, the directory is automatically generated, which is convenient for data users to view and find relevant data sources. It can register the data of relevant units or laboratories to DRC or link to DRC through an application programming interface (API). [6]
DAC
To ensure the relationship between people and data ownership, DAC is responsible for the process of data ownership confirmation and authorization. [7] By guaranteeing the interests of data owners, they are confident to put their data on the platform. The owner of the data divides data-related personnel into data owners, data producers, and data users. In the current study, a design was proposed to save all the related public keys to the DAC, and the private key is kept by their client, without placing it on any platform or cloud, to ensure security.
DEC
To protect the interests of data owners, DEC needs to supervise during the data flow process. From the point of data register and data conditional sharing, even after the trading process, we took blockchain-related technical means, such as watermarks and timestamps, and added them to the data authorization process to ensure data users cannot transmit data again without the owner’s permission. [8]
Laboratory management technology
Existing laboratory management usually uses a LIMS that collects related data through various laboratories. Some benefits of using a LIMS are the ability to track individual data items or samples from reported results. [11] Some limitations of a LIMS for this specific application exist, as they may not be specialized for specific equipment, or applicable to certain chemistries. [12] Some LIMS chemistry systems are only available to connect with the Public Safety department. It is rare to find a LIMS system for chemistry widely used in related departments. There is also a high price for many commercial LIMS systems. Various systems’ costs are expensive for labs, and customization is limited to what the system offers. [13] Additionally, experimental data are private to external parties, yet it still needs to be shared among the research team.
Recently, researchers have designed some LIMS for education labs or other specific applications. Focusing on education, there is Chaoqun and Lanlan's interactive LIMS, which incoporates experimental teaching management, experimental equipment management, laboratory open management, communication, and interactive management modules. [14] For specific disciplines, there are LIMS and other laboratory informatics solutions specifically designed for high-level biosafety labs or biobanks. [15,16] However, these systems only flow data inside the lab, in which data cannot flow quickly to supervision departments or related companies. Some researchers realized that the LIMS needs to be both secure and enhance efficiency in order to enable laboratory staff to conduct their research as freely as possible; therefore, the information on research, laboratory personnel, experimental materials, and experimental equipment is generally collected and utilized by only one system. [17] However, the current research mainly focuses on such a system's design, and there is no specific experimental technical means to verify it. Thus, we employed DOSA to rapidly and securely move data inside or outside the laboratory. In Table 1, we compare our proposed architecture to existing lab management systems.
| ||||||||||||||||||||||||
However, DOSA-related studies have designed models for some domains such as tourism, which only have frameworks without practical implementation. [9] We propose to use technical methods to solve data ownership by binding persons that used a key management system to protect data privacy.
Key system methods
To ensure data registration and sharing security, this work adopted RSA and AES algorithms, as well as Chinese domestic commercial keys SM2 and SM4, to compare the aspects of addressing efficiency and security of data. Table 2 summarizes the pros and cons of these key algorithms.
| ||||||||||||||||||||||||
SM2 and SM4 are cryptographic standards authorized to be used in China. Relevant studies have shown that the SM2 and SM4 algorithms are more secure than ECDSA and AES. [22] During a controlled experiment, AES outperformed SM4 by a significant margin. [23] Symmetric encryption is usually used when the message sender needs to encrypt a large amount of data. It has the characteristics of an open algorithm, a small amount of calculation, and fast encryption speed. The advantage of the symmetric encryption algorithm lies in the high speed of encryption and decryption, and the difficulty of cracking when using a long key. The disadvantages of symmetric encryption are that key management and distribution are difficult and insecure. Before the data are transmitted, the sender and the receiver must agree on a secret key, and both parties must keep the key. If the key of one party is leaked, the encrypted information is insecure, and its security cannot be guaranteed. [24]
The advantage of asymmetric encryption is its higher security. The public key is made available, and the private key is kept by itself so there is no need to give the private key to others. The disadvantage of asymmetric encryption is that its speed is relatively slow, so it is only suitable for encrypting a small amount of data.
Methodology
References
Notes
This presentation is faithful to the original, with only a few minor changes to presentation. In some cases important information was missing from the references, and that information was added.