Difference between revisions of "Journal:CustodyBlock: A distributed chain of custody evidence framework"
Shawndouglas (talk | contribs) (Created stub. Saving and adding more.) |
Shawndouglas (talk | contribs) (Saving and adding more.) |
||
| Line 27: | Line 27: | ||
==Abstract== | ==Abstract== | ||
With the increasing number of cybercrimes, the [[digital forensics]] team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of [[information]] that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient evidence management to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate [[chain of custody]] (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private [[blockchain]] protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed. | With the increasing number of cybercrimes, the [[digital forensics]] team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of [[information]] that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient [[wikipedia:Evidence management|evidence management]] to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate [[chain of custody]] (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private [[blockchain]] protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed. | ||
'''Keywords''': forensics, cybersecurity, distributed ledger technology (DLT), smart contract, blockchain | '''Keywords''': forensics, cybersecurity, distributed ledger technology (DLT), smart contract, blockchain | ||
==Introduction== | ==Introduction== | ||
[[wikipedia:Evidence management|Evidence management]] is one of the most important problems in [[digital forensics]]. Digital proof plays a vital role in crime investigations because it is used to link persons with their criminal activities. [[Chain of custody]] (CoC) in digital forensics can be defined as a process of documenting and maintaining the chronological history of handling digital evidence. [1,2] This plays an important role in the investigation of digital forensics because it notes every detail of concern to digital evidence through different levels of hierarchy. This goes from the first responder to the higher authorities who were responsible for handling the investigation of cybercrime. | |||
Digital proof comes with its own particular challenges, particularly when linked with the CoC. Blockchain technology can enable various stages of digital transaction to take place, however, providing massive advantages for the forensic community. In general, blockchain can act as a scattered form of [[information]] that maintains tamper-proof arrangement blocks that hold a cluster of individual transactions. It executes a decentralized and fully replicated append-only ledger, present in a peer-to-peer network, originally deployed for the bitcoin cryptocurrency. All the nodes present on the chain maintain a complete local copy of the blockchain. The blockchain is an indigenous technology that has emerged for decentralized applications, the outcome of complicated privacy and security issues present in applications for over half a century. [3,4] It is a peer-to-peer system that authorizes users to maintain a ledger for various transactions that are reproduced, and it remains identical in more than one location over multiple user servers. [5] | |||
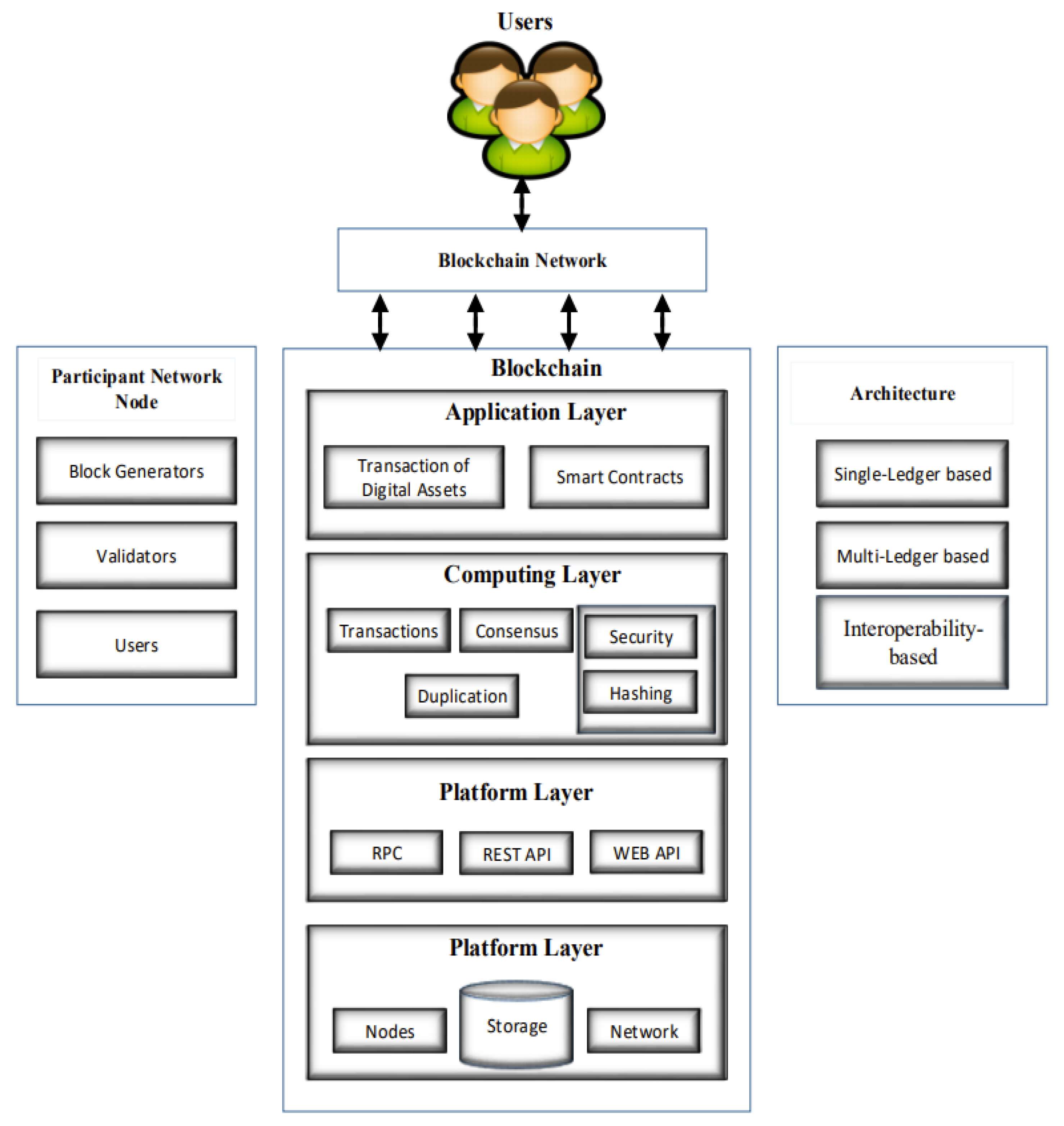
A blockchain is essentially a "block of chains," with the growing list of records that come from it referred to as "blocks" that are joined with [[Encryption|cryptography]]. [4] Each blockchain contains a hash of a previous block, and a timestamp that keeps track of the creation and modification time of a document. In terms of security, nobody, not even the owners of the document, ought to be able to modify it once it has been recorded (this can be done only if the integrity of time-stampers is compromised, which is rare). Blockchain was invented in 2008 and implemented in 2009 to function in the general public ledger of the Bitcoin cryptocurrency, a type of electronic money. Blockchain technology is decentralized (i.e., peer-to-peer). It consists of world network computers, which apply blockchain technology to put together and manage the information that records each Bitcoin transaction managed by its network. The architecture of blockchain technology, shown in Figure 1, implements a decentralized, fully replicated append-only ledger in a peer-to-peer network. [6] | |||
[[File:Fig1 Alruwaili Information21 12-2.png|700px]] | |||
{{clear}} | |||
{| | |||
| style="vertical-align:top;" | | |||
{| border="0" cellpadding="5" cellspacing="0" width="700px" | |||
|- | |||
| style="background-color:white; padding-left:10px; padding-right:10px;" |<blockquote>'''Fig. 1''' Architecture of blockchain</blockquote> | |||
|- | |||
|} | |||
|} | |||
The methodology proposed in this paper uses IBM's Hyperledger blockchain technology, as it is private and open-source. Hyperledger supports smart contracts called chaincodes. [7] Hyperledger is able to approve blocks and send the associated exchange transactions to the trusted and approved blocks to be validated and approved. [8] This is the most broadly utilized blockchain stage, utilized across various ventures and use-cases. It is utilized in a few models and proof-of-concepts, and is also being disseminated in record frameworks. | |||
Hyperledger is a blockchain with pluggable agreement. It is one of the more favorable uses of Hyperledger, which is hosted by the Linux Foundation. It is the first blockchain framework that permits the execution of dispersed applications written in standard programming. While generic blockchain utilizes request–execute–approve engineering, Hyperledger uses an execute–request–approve design and a support strategy that is overseen by assigned directors and functions as a static library for exchange approval. [9] | |||
Blockchain technology also provides decentralization, tracking, data transparency, security, and privacy for [[internet of things]] (IoT) applications. [10] IoT applications running in medical, transportation, agriculture, and other contexts require a high level of security. Blockchain provides the necessary security and privacy for different IoT applications and transactions, while maintaining a high level of integrity. Additionally, blockchain provides a high level of management for IoT systems by using privileged digital identities and access management. [11] Many researchers illustrate the importance of connecting IoT systems to a blockchain-based technology to enhance the level of security and IoT performance. [12,13,14] | |||
In the context of digital forensics, the production of evidence in the modern digital world is a complex task. For this reason, we consider it essential that digital evidence should be accepted as valid in court only if the CoC can assure exactly what the evidence is, why it was collected and analyzed, and how evidentiary data were collected, analyzed, and reported. This can be in the form of big data. [15,16] Additionally, the CoC must demonstrate exactly where, when, and who came into contact with the electronic evidence in each stage of an investigation, as well as any manipulation of the evidence. [17,18] The increasing complexity of [[forensic science]] in the digital area leads researchers to claim that traditional computer forensics “is on the edge of a precipice,” especially because of the great diversity of electronic devices to be examined and the intensive growth of the quantity of data that must be collected and examined during preservation in the blockchain. [19,20] This growing complexity makes it harder to create and maintain a reliable CoC, and it exposes a wide gap between general evidentiary criteria based on traditional forensic procedures and the scientific community’s point of view about the risks and conditions necessary to consider reliable any contemporary digital evidence. | |||
This scenario circumscribes the objective of this work: to review difficulties and formulate suggestions to make a more reliable CoC of digital evidence, making it more consistent with legal necessity regardless of the country, company, or tool through which digital evidence is collected. Within this objective, this work explores gaps between the traditional CoC and the modern studies’ point-of-view about the risks and requirements concerning the reliability of contemporary digital evidence. | |||
This paper also aims to contribute to the discussion about the trend to establish a worldwide standard more suited to maintaining CoC throughout the lifecycle of digital evidence and to help the improvement of new versions of CoC software. This work will not define or select any standard itself, because that is outside the scope of this paper. More specifically, this paper aims to address the challenges in forensic evidence collection, preservation, and investigation processes, for IoT environments in the smart home domain, by exploiting novel CoC technology, along with the CustodyBlock (CB) model, using private blockchain protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring of forensic evidence. | |||
The remainder of the paper is structured as follows. The next section analyzes the inherent problems of maintaining the CoC of digital evidence and the motivation for the proposed research, while the existing studies done in the area of the application of blockchain in forensics are described in the section after that. The paper then explains the research methodology, shows the proposed CustodyBlock model and its supporting architecture, illustrates digital evidence custody (DEC), and explains the algorithm for the proposed methodology. The penultimate section provides discussion and states future work, while the conclusion and future enhancements are given at the end. | |||
==Problem analysis and motivation for this research== | |||
Revision as of 22:46, 16 June 2022
| Full article title | CustodyBlock: A distributed chain of custody evidence framework |
|---|---|
| Journal | Information |
| Author(s) | Alruwaili, Fahad F. |
| Author affiliation(s) | Shaqra University |
| Primary contact | Email: alruwaili at su dot edu dot sa |
| Year published | 2021 |
| Volume and issue | 12(2) |
| Article # | 88 |
| DOI | 10.3390/info12020088 |
| ISSN | 2078-2489 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2078-2489/12/2/88/htm |
| Download | https://www.mdpi.com/2078-2489/12/2/88/pdf (PDF) |
|
|
This article should be considered a work in progress and incomplete. Consider this article incomplete until this notice is removed. |
Abstract
With the increasing number of cybercrimes, the digital forensics team has no choice but to implement more robust and resilient evidence-handling mechanisms. The capturing of digital evidence, which is a tangible and probative piece of information that can be presented in court and used in trial, is challenging due to its volatility and the possible effects of improper handling procedures. When computer systems get compromised, digital forensics comes into play to analyze, discover, extract, and preserve all relevant evidence. Therefore, it is imperative to maintain efficient evidence management to guarantee the credibility and admissibility of digital evidence in a court of law. A critical component of this process is to utilize an adequate chain of custody (CoC) approach to preserve the evidence in its original state from compromise and/or contamination. In this paper, a practical and secure CustodyBlock (CB) model using private blockchain protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring is proposed. The smart contracts in CB are utilized to enhance the model automation process for better and more secure evidence preservation and handling. A further research direction in terms of implementing blockchain-based evidence management ecosystems, and the implications on other different areas, are discussed.
Keywords: forensics, cybersecurity, distributed ledger technology (DLT), smart contract, blockchain
Introduction
Evidence management is one of the most important problems in digital forensics. Digital proof plays a vital role in crime investigations because it is used to link persons with their criminal activities. Chain of custody (CoC) in digital forensics can be defined as a process of documenting and maintaining the chronological history of handling digital evidence. [1,2] This plays an important role in the investigation of digital forensics because it notes every detail of concern to digital evidence through different levels of hierarchy. This goes from the first responder to the higher authorities who were responsible for handling the investigation of cybercrime.
Digital proof comes with its own particular challenges, particularly when linked with the CoC. Blockchain technology can enable various stages of digital transaction to take place, however, providing massive advantages for the forensic community. In general, blockchain can act as a scattered form of information that maintains tamper-proof arrangement blocks that hold a cluster of individual transactions. It executes a decentralized and fully replicated append-only ledger, present in a peer-to-peer network, originally deployed for the bitcoin cryptocurrency. All the nodes present on the chain maintain a complete local copy of the blockchain. The blockchain is an indigenous technology that has emerged for decentralized applications, the outcome of complicated privacy and security issues present in applications for over half a century. [3,4] It is a peer-to-peer system that authorizes users to maintain a ledger for various transactions that are reproduced, and it remains identical in more than one location over multiple user servers. [5]
A blockchain is essentially a "block of chains," with the growing list of records that come from it referred to as "blocks" that are joined with cryptography. [4] Each blockchain contains a hash of a previous block, and a timestamp that keeps track of the creation and modification time of a document. In terms of security, nobody, not even the owners of the document, ought to be able to modify it once it has been recorded (this can be done only if the integrity of time-stampers is compromised, which is rare). Blockchain was invented in 2008 and implemented in 2009 to function in the general public ledger of the Bitcoin cryptocurrency, a type of electronic money. Blockchain technology is decentralized (i.e., peer-to-peer). It consists of world network computers, which apply blockchain technology to put together and manage the information that records each Bitcoin transaction managed by its network. The architecture of blockchain technology, shown in Figure 1, implements a decentralized, fully replicated append-only ledger in a peer-to-peer network. [6]
|
The methodology proposed in this paper uses IBM's Hyperledger blockchain technology, as it is private and open-source. Hyperledger supports smart contracts called chaincodes. [7] Hyperledger is able to approve blocks and send the associated exchange transactions to the trusted and approved blocks to be validated and approved. [8] This is the most broadly utilized blockchain stage, utilized across various ventures and use-cases. It is utilized in a few models and proof-of-concepts, and is also being disseminated in record frameworks.
Hyperledger is a blockchain with pluggable agreement. It is one of the more favorable uses of Hyperledger, which is hosted by the Linux Foundation. It is the first blockchain framework that permits the execution of dispersed applications written in standard programming. While generic blockchain utilizes request–execute–approve engineering, Hyperledger uses an execute–request–approve design and a support strategy that is overseen by assigned directors and functions as a static library for exchange approval. [9]
Blockchain technology also provides decentralization, tracking, data transparency, security, and privacy for internet of things (IoT) applications. [10] IoT applications running in medical, transportation, agriculture, and other contexts require a high level of security. Blockchain provides the necessary security and privacy for different IoT applications and transactions, while maintaining a high level of integrity. Additionally, blockchain provides a high level of management for IoT systems by using privileged digital identities and access management. [11] Many researchers illustrate the importance of connecting IoT systems to a blockchain-based technology to enhance the level of security and IoT performance. [12,13,14]
In the context of digital forensics, the production of evidence in the modern digital world is a complex task. For this reason, we consider it essential that digital evidence should be accepted as valid in court only if the CoC can assure exactly what the evidence is, why it was collected and analyzed, and how evidentiary data were collected, analyzed, and reported. This can be in the form of big data. [15,16] Additionally, the CoC must demonstrate exactly where, when, and who came into contact with the electronic evidence in each stage of an investigation, as well as any manipulation of the evidence. [17,18] The increasing complexity of forensic science in the digital area leads researchers to claim that traditional computer forensics “is on the edge of a precipice,” especially because of the great diversity of electronic devices to be examined and the intensive growth of the quantity of data that must be collected and examined during preservation in the blockchain. [19,20] This growing complexity makes it harder to create and maintain a reliable CoC, and it exposes a wide gap between general evidentiary criteria based on traditional forensic procedures and the scientific community’s point of view about the risks and conditions necessary to consider reliable any contemporary digital evidence.
This scenario circumscribes the objective of this work: to review difficulties and formulate suggestions to make a more reliable CoC of digital evidence, making it more consistent with legal necessity regardless of the country, company, or tool through which digital evidence is collected. Within this objective, this work explores gaps between the traditional CoC and the modern studies’ point-of-view about the risks and requirements concerning the reliability of contemporary digital evidence.
This paper also aims to contribute to the discussion about the trend to establish a worldwide standard more suited to maintaining CoC throughout the lifecycle of digital evidence and to help the improvement of new versions of CoC software. This work will not define or select any standard itself, because that is outside the scope of this paper. More specifically, this paper aims to address the challenges in forensic evidence collection, preservation, and investigation processes, for IoT environments in the smart home domain, by exploiting novel CoC technology, along with the CustodyBlock (CB) model, using private blockchain protocol and smart contracts to support the control, transfer, analysis, and preservation monitoring of forensic evidence.
The remainder of the paper is structured as follows. The next section analyzes the inherent problems of maintaining the CoC of digital evidence and the motivation for the proposed research, while the existing studies done in the area of the application of blockchain in forensics are described in the section after that. The paper then explains the research methodology, shows the proposed CustodyBlock model and its supporting architecture, illustrates digital evidence custody (DEC), and explains the algorithm for the proposed methodology. The penultimate section provides discussion and states future work, while the conclusion and future enhancements are given at the end.
Problem analysis and motivation for this research
References
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added. Numerous links that were originally posted inline in the text were turned into full citations for this version, adding significantly to the total citation count.