Difference between revisions of "Main Page/Featured article of the week/2022"
Shawndouglas (talk | contribs) (Added last week's article of the week) |
Shawndouglas (talk | contribs) (Added last week's article of the week) |
||
| Line 17: | Line 17: | ||
<!-- Below this line begin pasting previous news --> | <!-- Below this line begin pasting previous news --> | ||
<h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 17–23:</h2> | <h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 24–30:</h2> | ||
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig5 Jebali JofInfoTelec2020 5-1.jpg|240px]]</div> | |||
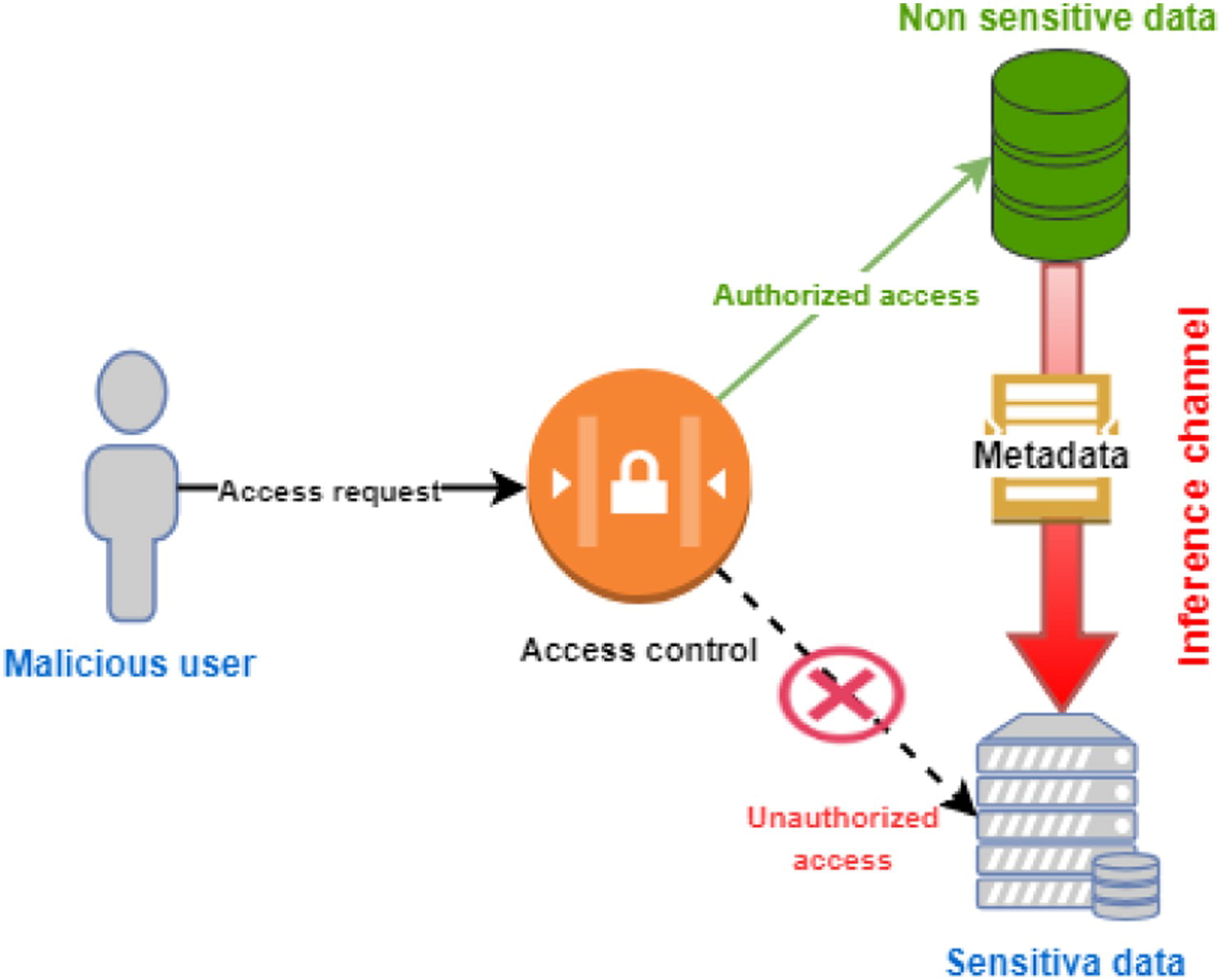
'''"[[Journal:Secure data outsourcing in presence of the inference problem: Issues and directions|Secure data outsourcing in presence of the inference problem: Issues and directions]]"''' | |||
With the emergence of the [[cloud computing]] paradigms, secure data outsourcing—moving some or most data to a third-party provider of secure data management services—has become one of the crucial challenges of modern computing. Data owners place their data among cloud service providers (CSPs) in order to increase flexibility, optimize storage, enhance data manipulation, and decrease processing time. Nevertheless, from a [[Cybersecurity|security]] point of view, access control proves to be a major concern in this situation seeing that the security policy of the data owner must be preserved when data is moved to the cloud. The lack of a comprehensive and systematic review on this topic in the available literature motivated us to review this research problem. Here, we discuss current and emerging research on privacy and confidentiality concerns in cloud-based data outsourcing and pinpoint potential issues that are still unresolved. ('''[[Journal:Secure data outsourcing in presence of the inference problem: Issues and directions|Full article...]]''')<br /> | |||
|- | |||
|<br /><h2 style="font-size:105%; font-weight:bold; text-align:left; color:#000; padding:0.2em 0.4em; width:50%;">Featured article of the week: January 17–23:</h2> | |||
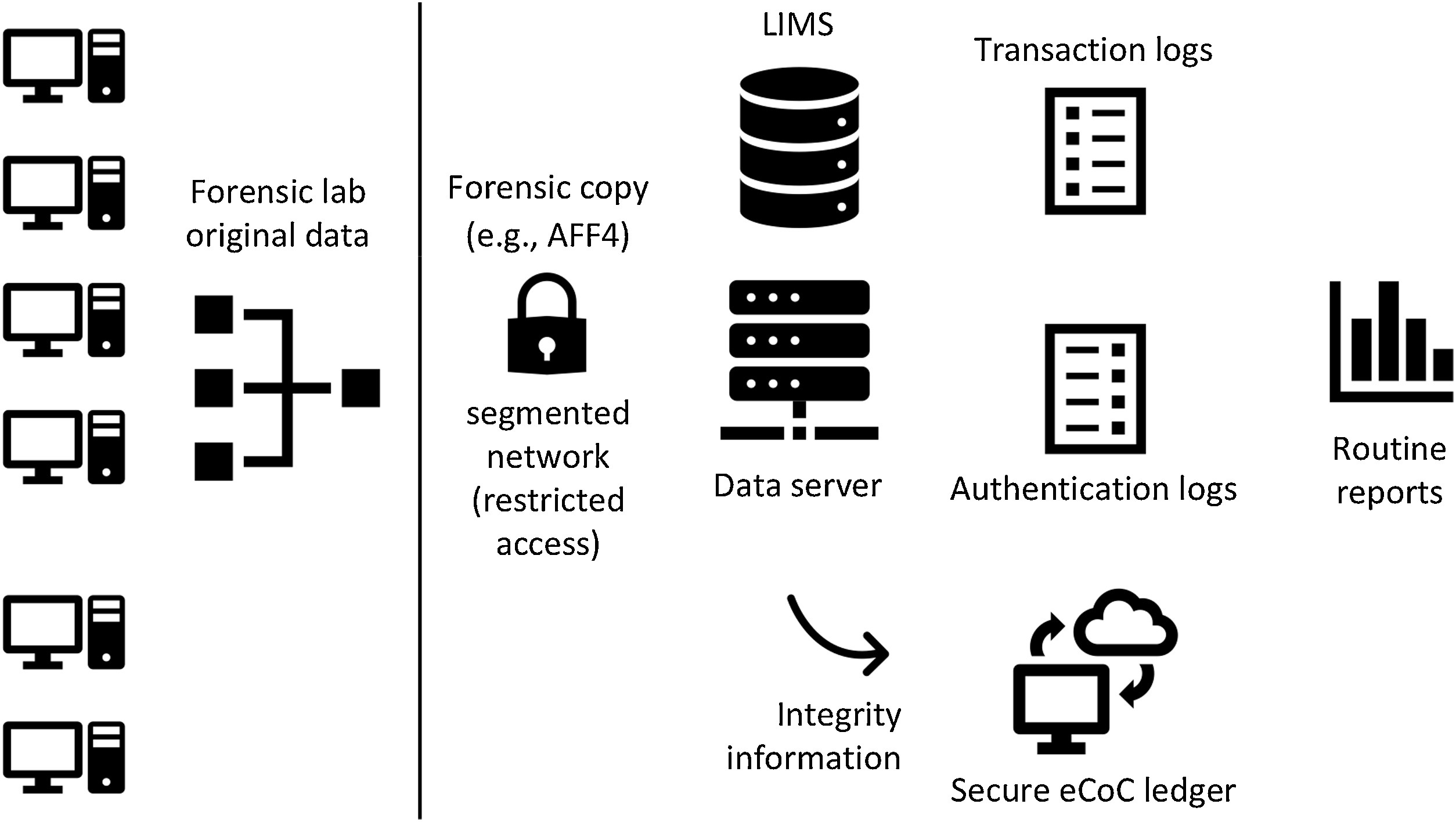
<div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Casey ForensicSciInt2020 316.jpg|240px]]</div> | <div style="float: left; margin: 0.5em 0.9em 0.4em 0em;">[[File:Fig2 Casey ForensicSciInt2020 316.jpg|240px]]</div> | ||
'''"[[Journal:Digital transformation risk management in forensic science laboratories|Digital transformation risk management in forensic science laboratories]]"''' | '''"[[Journal:Digital transformation risk management in forensic science laboratories|Digital transformation risk management in forensic science laboratories]]"''' | ||
Revision as of 16:11, 31 January 2022
|
|
If you're looking for other "Article of the Week" archives: 2014 - 2015 - 2016 - 2017 - 2018 - 2019 - 2020 - 2021 - 2022 |
Featured article of the week archive - 2022
Welcome to the LIMSwiki 2022 archive for the Featured Article of the Week.
Featured article of the week: January 24–30:"Secure data outsourcing in presence of the inference problem: Issues and directions" With the emergence of the cloud computing paradigms, secure data outsourcing—moving some or most data to a third-party provider of secure data management services—has become one of the crucial challenges of modern computing. Data owners place their data among cloud service providers (CSPs) in order to increase flexibility, optimize storage, enhance data manipulation, and decrease processing time. Nevertheless, from a security point of view, access control proves to be a major concern in this situation seeing that the security policy of the data owner must be preserved when data is moved to the cloud. The lack of a comprehensive and systematic review on this topic in the available literature motivated us to review this research problem. Here, we discuss current and emerging research on privacy and confidentiality concerns in cloud-based data outsourcing and pinpoint potential issues that are still unresolved. (Full article...)
|