Difference between revisions of "Cloud computing"
Shawndouglas (talk | contribs) (→History: Added more) |
Shawndouglas (talk | contribs) m (Fixed citation issue) |
||
| Line 123: | Line 123: | ||
As cloud computing increases in popularity, concerns are being raised about the security issues introduced through the adoption of this new model. The effectiveness and efficiency of traditional protection mechanisms are being reconsidered as the characteristics of this innovative deployment model differ widely from those of traditional architectures.<ref name="Zissis10">{{cite journal |title=Addressing cloud computing security issues |journal=Future Generation Computer Systems |author=Zissis, D.; Lekkas, D. |volume=28 |issue=3 |pages=583–92 |year=2012 |doi=10.1016/j.future.2010.12.006}}</ref> | As cloud computing increases in popularity, concerns are being raised about the security issues introduced through the adoption of this new model. The effectiveness and efficiency of traditional protection mechanisms are being reconsidered as the characteristics of this innovative deployment model differ widely from those of traditional architectures.<ref name="Zissis10">{{cite journal |title=Addressing cloud computing security issues |journal=Future Generation Computer Systems |author=Zissis, D.; Lekkas, D. |volume=28 |issue=3 |pages=583–92 |year=2012 |doi=10.1016/j.future.2010.12.006}}</ref> | ||
Issues barring the adoption of cloud computing are due in large part to the private and public sectors' unease surrounding the external management of security based services. It is the very nature of cloud computing based services, private or public, that promote external management of provided services. This delivers great incentive among cloud computing service providers in producing a priority in building and maintaining strong management of secure services.<ref name="MessmerSecurity10">{{cite web |url=https://www.networkworld.com/article/2244954/security-of-virtualization--cloud-computing-divides-it-and-security-pros.html |title=Security of virtualization, cloud computing divides IT and security pros |author=Messmer, E. |publisher=Network World |date=22 February 2010 |accessdate=14 April 2020}}</ref> Security issues have been categorized into sensitive data access, data segregation, privacy, bug exploitation, recovery, accountability, malicious insiders, management console security, account control, and multi-tenancy issues. Solutions to various cloud security issues vary from cryptography (particularly public key infrastructure), use of multiple cloud providers, standardization of APIs, improving virtual machine support, and legal support.<ref name="Zissis10" /><ref name="Armbrust10">{{cite journal |title=A view of cloud computing |journal=Communications of the ACM |author=Armbrust, M.; Fox, A.; Griffith, R. et al. |volume=53 |issue=4 |pages=50–58 |year=2010 |doi=10.1145/1721654.1721672}}</ref><ref name=" | Issues barring the adoption of cloud computing are due in large part to the private and public sectors' unease surrounding the external management of security based services. It is the very nature of cloud computing based services, private or public, that promote external management of provided services. This delivers great incentive among cloud computing service providers in producing a priority in building and maintaining strong management of secure services.<ref name="MessmerSecurity10">{{cite web |url=https://www.networkworld.com/article/2244954/security-of-virtualization--cloud-computing-divides-it-and-security-pros.html |title=Security of virtualization, cloud computing divides IT and security pros |author=Messmer, E. |publisher=Network World |date=22 February 2010 |accessdate=14 April 2020}}</ref> Security issues have been categorized into sensitive data access, data segregation, privacy, bug exploitation, recovery, accountability, malicious insiders, management console security, account control, and multi-tenancy issues. Solutions to various cloud security issues vary from cryptography (particularly public key infrastructure), use of multiple cloud providers, standardization of APIs, improving virtual machine support, and legal support.<ref name="Zissis10" /><ref name="Armbrust10">{{cite journal |title=A view of cloud computing |journal=Communications of the ACM |author=Armbrust, M.; Fox, A.; Griffith, R. et al. |volume=53 |issue=4 |pages=50–58 |year=2010 |doi=10.1145/1721654.1721672}}</ref><ref name="AnthesSecurity10">{{cite journal |title=Security in the cloud |journal=Communications of the ACM |author=Anthes, G. |volume=53 |issue=11 |pages=16–18 |year=2010 |doi=10.1145/1839676.1839683}}</ref> | ||
The complexity of security is further increased when data is distributed over a wider area or greater number of devices and in multi-tenant systems that are being shared by unrelated users. In addition, user access to security audit logs may be difficult or impossible. The move to private cloud installations are in part motivated by users' desire to retain control over the infrastructure and avoid losing control of information security. | The complexity of security is further increased when data is distributed over a wider area or greater number of devices and in multi-tenant systems that are being shared by unrelated users. In addition, user access to security audit logs may be difficult or impossible. The move to private cloud installations are in part motivated by users' desire to retain control over the infrastructure and avoid losing control of information security. | ||
Revision as of 18:12, 19 September 2021
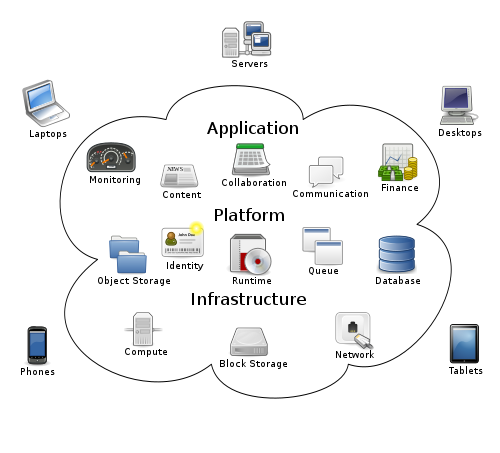
Cloud computing is the delivery of computing as a service rather than a product, whereby shared resources, software, and information are provided to computers and other devices as a utility (like the electricity grid) over a network, typically the Internet.
Cloud computing describes a new supplement, consumption, and delivery model for IT services based on Internet protocols, and it typically involves provisioning of dynamically scalable and often virtualized resources[1][2] Details are abstracted from end-users, who no longer have need for expertise in, or control over, the technology infrastructure "in the cloud" that supports them.[3]
Cloud computing typically takes the form of web-based tools or applications that users can access and use through a web browser as if they were programs installed locally on their own computers. Those applications and resulting data are stored on servers at a remote location. In some cases, legacy applications (line of business applications that until now have been prevalent in thin client Windows computing) are delivered via a screen-sharing technology, while the computing resources are consolidated at a remote data center location; in other cases, entire business applications have been coded using web-based technologies such as Ajax.
Overview
Term
The term "cloud" is used as a metaphor for the Internet, based on the cloud drawing used in the past to represent the telephone network,[4] and later to depict the Internet in computer network diagrams as an abstraction of the underlying infrastructure it represents.[5]
Characteristics
The National Institute of Standards and Technology (NIST) offers an authoritative definition of cloud computing. That definition encompasses the essential characteristics, service models, and deployment models of the service. Of the essential characteristics, cloud computing must[6]:
- provide computing capabilities and services on an as-needed basis, without human intervention;
- be broadly accessible from a wide variety of standard desktop and mobile platforms;
- make storage, processing, memory, and network bandwidth available as pooled, multi-tenant resources;
- make those resources scalable with demand, often automatically, at any time; and
- meter those resources and make the resulting information transparently available to both provider and consumer.
Additional, more granular characteristics of cloud computing include the following.
- An application programming interface (API) enables machines to interact with cloud software in the same way the user interface facilitates interaction between humans and computers. Cloud computing systems typically use REST-based APIs.
- Cost is potentially reduced in a public cloud delivery model, with capital expenditure being converted to operational expenditure, including research, development, and sales.[7] This is purported to lower barriers to entry, as infrastructure is typically provided by a third-party and does not need to be purchased for one-time or infrequent intensive computing tasks. Pricing on a utility computing basis is fine-grained with usage-based options and fewer in-house IT skills are required for implementation.[8]
- Device and location independence enable users to access systems using a web browser regardless of their location or what device they are using (e.g., PC, mobile phone).[9] As infrastructure is off-site (typically provided by a third-party) and accessed via the Internet, users can connect from anywhere.[8]
- Multi-tenancy enables sharing of resources and costs across a large pool of users, allowing for centralization of infrastructure in locations with lower costs, peak-load capacity increases, and utilization and efficiency improvements.
- Reliability is improved if multiple redundant sites are used, which makes well-designed cloud computing suitable for business continuity and disaster recovery.[10]
- Services are scalable and elastic via dynamic, "on-demand" provisioning of resources on a fine-grained, self-service basis in real-time, without users having to engineer for peak loads.[11]
- Performance is monitored, and consistent and loosely coupled architectures are constructed using web services as the system interface.[8]
- Security could improve due to centralization of data, increased security-focused resources, etc., but concerns may persist about loss of control over certain sensitive data and the lack of security for stored kernels.
- Maintenance of cloud computing applications is easier, because they do not need to be installed on each user's computer. They are easier to support and to improve, as the changes reach the clients instantly.
Service models
The NIST definition also details the service models, which include software as a service (SaaS; provider's application runs on their infrastructure), platform as a service (PaaS; consumer-created or -acquired application runs on provider's infrastructure), and infrastructure as a service (IaaS; customer deploys operating systems and applications over fundamental computing resources provisioned by the provider).[6]
SaaS
NIST's definition of cloud computing defines SaaS as[6]:
The capability provided to the consumer is to use the provider's applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g., web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings.
By not needing to manage the cloud infrastructure and platform where the application runs, the need to install and run the application on the cloud user's own computers is eliminated, simplifying maintenance and support. The pricing model for SaaS applications is typically a monthly or yearly flat fee per user, and as such prices become scalable and adjustable if users are added or removed at any point.
Proponents of this model claim that SaaS has the potential to reduce IT operational costs by outsourcing hardware and software maintenance and support to the cloud provider. This enables the business to reallocate IT operations costs away from hardware/software spending and from personnel expenses, towards meeting other goals. In addition, with applications hosted centrally, updates can be released without the need for users to install new software.[12]
PaaS
NIST's definition of cloud computing defines PaaS as[6]:
The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment.
As such, PaaS users do not manage or control the underlying cloud infrastructure, including network, servers, operating systems, or storage. Rather, they have control over the deployed applications, and in some cases the configuration settings for the application-hosting environment.[12]
IaaS
NIST's definition of cloud computing describes IaaS as a platform "where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications, and possibly limited control of select networking components (e.g., host firewalls)."[6]
IaaS-cloud providers supply these resources on-demand from their large pools of equipment installed in data centers. For wide area network connectivity, customers can use either the internet or carrier clouds (dedicated virtual private networks). To deploy their applications, cloud users install operating-system images and their application software on the cloud infrastructure. The cloud user patches and maintains the operating systems and the application software on the infrastructure. Cloud providers typically bill IaaS services on a utility computing basis: cost reflects the amount of resources allocated and consumed.[12]
Deployment models
The NIST definition identifies four deployment models for cloud computing.[6]
Private cloud: an infrastructure operated solely for a single organization, whether managed internally or by a third-party and hosted internally or externally
Community cloud: an infrastructure shared between several organisations from a specific community with common concerns (security, compliance, jurisdiction, etc.), managed internally or by a third-party and hosted internally or externally
Public cloud: an infrastructure where resources are dynamically provisioned to the general public on a fine-grained, self-service basis over the Internet, via web applications/web services, from an off-site third-party provider who bills on a metered basis
Hybrid cloud: a composition of two or more clouds (private, community, or public) that remain unique entities but are bound together, offering the benefits of multiple deployment models
Other deployment options have arisen as well. Another (potentially classifiable as "hybrid") that has become more notable is carrier cloud, cloud computing services integrated into a communications service provider's network infrastructure.[13][14] Others include distributed cloud (a distributed set of machines in different locations)[15], high-performance computing cloud (able to handle high-performance computing applications)[16], and polycloud (use of multiple public clouds from different providers, levaraging specific services each offers).[17]
History
The underlying concept of cloud computing dates back to the 1960s, when John McCarthy opined that "computation may someday be organized as a public utility."[18] Almost all the modern-day characteristics of cloud computing (elastic provision, provided as a utility, online, illusion of infinite supply), as well as the comparison to the electricity industry and the use of public, private, government, and community forms, were thoroughly explored in Douglas Parkhill's 1966 book, The Challenge of the Computer Utility.[19]
The actual term "cloud" borrows from telephony in that telecommunications companies, that until the 1990s offered primarily dedicated point-to-point data circuits, began offering virtual private network (VPN) services with comparable quality of service but at a much lower cost. By switching traffic to balance utilization as they saw fit, they were able to utilize their overall network bandwidth more effectively. The cloud symbol was used to denote the demarcation point between that which was the responsibility of the provider and that which was the responsibility of the user. Cloud computing extends this boundary to cover servers as well as the network infrastructure.[20]
By the beginning of the twenty-first century, the advent of virtualization technology and cost effective computing hardware, as well as ubiquitous Internet connectivity, enabled a first wave of cloud services, including Salesforce.com in 1999 and Amazon Web Services in 2002.[21] After the dot-com bubble, Amazon continued to play key role in the development of cloud computing by modernizing their data centers, which, like most computer networks, were using as little as 10 percent of their capacity at any one time, just to leave room for occasional spikes. Having found the new cloud architecture resulted in significant internal efficiency improvements whereby small, fast-moving "two-pizza teams" could add new features faster and more easily, Amazon initiated a new commercial cloud-based project, launching its Elastic Compute cloud (EC2) in 2006.[21]
In May 2008, Eucalyptus became the first open-source, Amazon Web Service API-compatible platform for deploying private clouds.[22] In early 2008, OpenNebula, enhanced in the RESERVOIR European Commission-funded project, became the first open-source software for deploying private and hybrid clouds and for the federation of clouds.[23] By mid-2008, technology research firm Gartner saw an opportunity for cloud computing "to shape the relationship among consumers of IT services, those who use IT services and those who sell them"[24] and observed that "organisations are switching from company-owned hardware and software assets to per-use service-based models" so that the "projected shift to cloud computing ... will result in dramatic growth in IT products in some areas and significant reductions in other areas."[25]
By 2013, Gartner was reporting the public cloud services market was forecast to grow 18.5 percent in 2013, totalling $131 billion worldwide, up from $111 billion in 2012. Infrastructure as a service (IaaS) made up the fastest-growing segment of the market, growing 42.4 percent in 2012 to $6.1 billion, with expectations of it growing 47.3 percent in 2013 to $9 billion.[26]
By 2017, "edge computing" began to emerge as a viable option. Edge computing is a distributed computing paradigm that brings computation and storage closer to the location where is needed, thus improving response times and saving bandwidth. This in part has been driven by increasing use of mobile applications, and sensor-based internet of things devices.[27] More broadly, by the late 2010s, a distinct trend in cloud computing was emerging, as noted by Varghese and Buyya: "The general trend seems to be towards making use of infrastructure from multiple providers and decentralising computing away from resources currently concentrated in data centers. This is in contrast to traditional cloud offerings from single providers. Consequently, new computing models to suit the demands of the market are emerging."[28]
Issues and concerns
General criticisms of cloud computing state the term is too unspecific or even misleading. CEO Larry Ellison of Oracle Corporation asserts that cloud computing is "everything that we already do"[29] and that the company could simply "change the wording on some of our ads" [30] to deploy cloud-based services.
In 2008, Forrester Research VP Frank Gillett questioned the very nature of and motivation behind the push for cloud computing, describing what he calls "cloud washing"—companies simply relabeling their products as "cloud computing", resulting in mere marketing innovation instead of "real" innovation. [31] That same year, GNU's Richard Stallman insisted the industry will only use the model to deliver services at ever increasing rates over proprietary systems, otherwise likening it to a "marketing hype campaign."[32]
Privacy
The cloud model has been criticized by privacy advocates for the greater ease in which the companies hosting the cloud services control and monitor at will, lawfully or unlawfully, the communication and data stored between the user and the host company, leading to questions about whether or not privacy concerns can be addressed.[33][34]
Compliance
In order to obtain compliance with regulations including FISMA, HIPAA, and SOX in the United States, the Data Protection Directive in the European Union, and the credit card industry's PCI DSS, users may have to adopt community or hybrid deployment modes that are typically more expensive and may offer restricted benefits. This is how Google is able to "manage and meet additional government policy requirements beyond FISMA"[35][36] and Rackspace Cloud are able to claim PCI compliance.[37]
Many providers also obtain SAS 70 Type II certification, but this has been criticized on the grounds that the hand-picked set of goals and standards determined by the auditor and the auditee are often not disclosed and can vary widely.[38] Providers typically make this information available on request, under non-disclosure agreement.[39]
Customers in the European Union contracting with cloud providers established outside the area have to adhere to the European Union's regulations on export of personal data.[40]
Performance
Public cloud instances typically function well at the server and client hardware; however, speed across the connecting public Internet pipeline can vary significantly. Internet speeds can be asymmetrical and non-guaranteed, bandwidth may need to be shared, and Internet traffic rarely follow the same path, constraining performance and making a cloud option less appealing than a localized option.[41] Poor upload speeds, especially from non-business home accounts, are also quoted as a factor limiting cloud computing's appeal.[42]
Legal
Since 2007, the number of trademark filings covering cloud computing brands, goods, and services has increased rapidly. For example, in March 2007, Dell applied to trademark the term "cloud computing" (U.S. Trademark 77,139,082) in the United States. The "Notice of Allowance" the company received in July 2008 was canceled in August, resulting in a formal rejection of the trademark application less than a week later. As Dell and other companies sought to better position themselves for cloud computing branding and marketing efforts, cloud computing trademark filings increased by 483 percent between 2008 and 2009. In 2009, 116 cloud computing trademarks were filed, and trademark analysts predicted that over 500 such marks could be filed during 2010.[43]
Other legal cases may shape the use of cloud computing by the public sector. On October 29, 2010, Google filed a lawsuit against the U.S. Department of Interior, which opened up a bid for software that required bidders use Microsoft's Business Productivity Online Suite. Google sued, calling the requirement "unduly restrictive of competition."[44] Scholars have pointed out that, beginning in 2005, the prevalence of open standards and open-source software options may have an impact on the way public entities choose to select vendors and their software.[45]
Concerns about the legal and financial repercussions of a cloud provider shutting down, which has happened in a number of cases, also exist.[46]
Open standards
Most cloud providers expose APIs that are typically well-documented (often under a Creative Commons license[47]) but also unique to their implementation and thus not interoperable. Some vendors have adopted others' APIs, and there are a number of open standards under development, with a view to delivering interoperability and portability.[48]
Security
As cloud computing increases in popularity, concerns are being raised about the security issues introduced through the adoption of this new model. The effectiveness and efficiency of traditional protection mechanisms are being reconsidered as the characteristics of this innovative deployment model differ widely from those of traditional architectures.[49]
Issues barring the adoption of cloud computing are due in large part to the private and public sectors' unease surrounding the external management of security based services. It is the very nature of cloud computing based services, private or public, that promote external management of provided services. This delivers great incentive among cloud computing service providers in producing a priority in building and maintaining strong management of secure services.[50] Security issues have been categorized into sensitive data access, data segregation, privacy, bug exploitation, recovery, accountability, malicious insiders, management console security, account control, and multi-tenancy issues. Solutions to various cloud security issues vary from cryptography (particularly public key infrastructure), use of multiple cloud providers, standardization of APIs, improving virtual machine support, and legal support.[49][51][52]
The complexity of security is further increased when data is distributed over a wider area or greater number of devices and in multi-tenant systems that are being shared by unrelated users. In addition, user access to security audit logs may be difficult or impossible. The move to private cloud installations are in part motivated by users' desire to retain control over the infrastructure and avoid losing control of information security.
Contracts
Most transitions to a cloud computing solution entail a change from a technically managed solution to a contractually managed solution. This change necessitates increased IT contract negotiation skills to establish the terms of the relationship and vendor management skills to maintain the relationship. All rights and responsibilities associated with the relationship between a client and a provider must be codified in the contract and effectively managed until the relationship has been terminated. Key risks and issues that are either unique to cloud computing or essential to its effective adoption typically involve service level agreements; data processing and access; provider infrastructure and security; and contract and vendor management.[53]
Further reading
- Halpert, Ben (2011). Auditing Cloud Computing: A Security and Privacy Guide. John Wiley & Sons. pp. 206. ISBN 9780470874745. http://books.google.com/books?id=GjsH0HJ2PmYC&pg=PT10&lpg=PT10.
- Kavis, Michael J (2014). Architecting the Cloud: Design Decisions for Cloud Computing Service Models (SaaS, PaaS, and IaaS). John Wiley & Sons. pp. 224. ISBN 9781118617618. http://www.amazon.com/Architecting-Cloud-Decisions-Computing-Service/dp/1118617614.
Notes
This article reuses numerous content elements from the Wikipedia article.
References
- ↑ "Gartner Says Cloud Computing Will Be As Influential As E-business". Gartner, Inc. 26 June 2008. Archived from the original on 28 August 2018. https://web.archive.org/web/20180828134416/https://www.gartner.com/newsroom/id/707508. Retrieved 14 April 2020.
- ↑ Knorr, E. (2 October 2018). "What is cloud computing? Everything you need to know now". InfoWorld. IDG Network. https://www.infoworld.com/article/2683784/what-is-cloud-computing.html. Retrieved 14 April 2020.
- ↑ Danielson, K. (26 March 2008). "Distinguishing Cloud Computing from Utility Computing". ebizQ. TechTarget. http://www.ebizq.net/blogs/saasweek/2008/03/distinguishing_cloud_computing/. Retrieved 14 April 2020.
- ↑ Sells, Chris (1 July 1998). "Windows Telephony Programming: A Developer's Guide to TAPI". Sellsbrothers.com. Archived from the original on 02 May 2005. https://web.archive.org/web/20050502192319/http://www.sellsbrothers.com/writing/intro2tapi/default.aspx?content=pstn.htm. Retrieved 21 August 2014.
- ↑ Scanlon,Jessie Holliday; Wieners, Brad (9 July 1999). "The Internet Cloud". The Industry Standard. IDG Network. Archived from the original on 11 February 2010. https://web.archive.org/web/20100211133442/http://www.thestandard.com/article/0,1902,5466,00.html. Retrieved 2010-08-22.
- ↑ 6.0 6.1 6.2 6.3 6.4 6.5 Mell, P.; Grance, T. (September 2011). "The NIST Definition of Cloud Computing". National Institute of Standards and Technology. https://csrc.nist.gov/publications/detail/sp/800-145/final. Retrieved 14 April 2020.
- ↑ Columbus, L. (10 April 2013). "Making Cloud Computing Pay". Forbes. https://www.forbes.com/sites/louiscolumbus/2013/04/10/making-cloud-computing-pay-2/. Retrieved 14 April 2020.
- ↑ 8.0 8.1 8.2 Gens, Frank (23 September 2008). "Defining "Cloud Services" and "Cloud Computing"". IDC. Archived from the original on 28 May 2017. https://web.archive.org/web/20170528125047/http://blogs.idc.com/ie/?p=190. Retrieved 14 April 2020.
- ↑ Farber, D. (25 June 2008). "The new geek chic: Data centers". CNET. CBS Interactive. https://www.cnet.com/news/the-new-geek-chic-data-centers/. Retrieved 14 April 2020.
- ↑ King, R. (4 August 2008). "Cloud Computing: Small Companies Take Flight". Bloomberg.
- ↑ Kuperberg, M.; Herbst, N.; von Kistowski, J.; Reussner, R. (2011). "Defining and Quantifying Elasticity of Resources in Cloud Computing and Scalable Platforms". Karlsruher Institut für Technologie. https://publikationen.bibliothek.kit.edu/1000023476. Retrieved 14 April 2020.
- ↑ 12.0 12.1 12.2 Griffin, R. (2018). Internet Governance. ED-Tech Press. pp. 111–13. ISBN 9781839473951. https://books.google.com/books?id=OuTEDwAAQBAJ&pg=PA111. Retrieved 14 April 2020.
- ↑ "Cloud Evolution: The Carrier Cloud" (PDF). Kontron. 2013. https://www.kontron.com/resources/collateral/white_papers/kontroncarriercloudwp.pdf.
- ↑ Narcisi, G. (November 2013). "Carrier cloud services: Do customers care if you own the network?". SearchNetworking. TechTarget. https://searchnetworking.techtarget.com/feature/Carrier-cloud-services-Do-customers-care-if-you-own-the-network. Retrieved 14 April 2020.
- ↑ Cunsolo, V.D.; Distefano, S.; Puliafito, A. et al. (2009). "Volunteer Computing and Desktop Cloud: The Cloud@Home Paradigm". 2009 Eighth IEEE International Symposium on Network Computing and Applications: 134–9. doi:10.1109/NCA.2009.41.
- ↑ Netto, M.A.S.; Calheiros, R.N.; Rodrigues, E.R. et al. (2018). "HPC Cloud for Scientific and Business Applications: Taxonomy, Vision, and Research Challenges". AMC Computing Surveys 51 (1): 8. doi:10.1145/3150224.
- ↑ Gall, R. (16 May 2018). "Polycloud: A better alternative to cloud agnosticism". Cloud and Networking News. Packt Publishing. https://hub.packtpub.com/polycloud-a-better-alternative-to-cloud-agnosticism/. Retrieved 14 April 2020.
- ↑ Halpert, Ben (2011). "Chapter 1: Introduction to Cloud Computing". Auditing Cloud Computing: A Security and Privacy Guide. John Wiley & Sons. pp. 1–13. ISBN 9781118116043. http://books.google.com/books?id=GjsH0HJ2PmYC&pg=PT10&lpg=PT10. Retrieved 21 August 2014.
- ↑ Parhill, Douglas (2006). The Challenge of the Computer Utility. Addison-Wesley Pub. Co. http://books.google.com/books?id=8kJZAAAAMAAJ. Retrieved 21 August 2014.
- ↑ Laubach, Mark (July 1993). "Minutes of the IP Over Asynchronous Transfer Mode Working Group (ATM)". Hewlett-Packard. Archived from the original on 22 July 2003. https://web.archive.org/web/20030722214022/http://ftp.univie.ac.at/netinfo/ietf/atm/atm-minutes-93jul.txt. Retrieved 14 April 2020.
- ↑ 21.0 21.1 Mohamed, A. (9 April 2018). "A history of cloud computing". ComputerWeekly.com. TechTarget. https://www.computerweekly.com/feature/A-history-of-cloud-computing. Retrieved 14 April 2020.
- ↑ "The Eucalyptus Story". Eucalyptus Systems, Inc. Archived from the original on 26 June 2014. https://web.archive.org/web/20140626125211/https://www.eucalyptus.com/about/story. Retrieved 14 April 2020.
- ↑ Rochwerger, B.; Caceres, J.; Montero, R.S. et al. (2009). "The RESERVOIR Model and Architecture for Open Federated Cloud Computing". IBM Journal of Research and Development 53 (4). Archived from the original on 08 January 2012. https://web.archive.org/web/20120108183022/http://researchweb.watson.ibm.com/journal/abstracts/rd/534/rochwerger.html. Retrieved 14 April 2020.
- ↑ Schurr, A. (8 July 2008). "Keep an eye on cloud computing". Network World. https://www.networkworld.com/article/2281563/keep-an-eye-on-cloud-computing.html. Retrieved 14 April 2020.
- ↑ "Gartner Says Worldwide IT Spending On Pace to Surpass Trillion in 2008". Gartner, Inc. 18 August 2008. Archived from the original on 03 July 2017. https://web.archive.org/web/20170703131346/http://www.gartner.com/newsroom/id/742913. Retrieved 14 April 2020.
- ↑ "Gartner Says Worldwide Public Cloud Services Market to Total $131 Billion". Gartner, Inc. 28 February 2013. Archived from the original on 18 February 2017. https://web.archive.org/web/20170218030806/http://www.gartner.com/newsroom/id/2352816. Retrieved 14 April 2020.
- ↑ Satyanarayanan, M. (2017). "The Emergence of Edge Computing". Computer 50 (1): 30–39. doi:10.1109/MC.2017.9.
- ↑ Varghese, B.; Buyya, R. (2018). "Next generation cloud computing: New trends and research directions". Future Generation Computer Systems 79 (Part 3): 849–61. doi:10.1016/j.future.2017.09.020.
- ↑ Farber, D. (26 September 2008). "Oracle's Ellison nails cloud computing". CNET. CBS Interactive. https://www.cnet.com/news/oracles-ellison-nails-cloud-computing/. Retrieved 14 April 2020.
- ↑ Kanaracus, C. (9 February 2010). "Oracle launches worldwide cloud-computing tour". Network World. https://www.networkworld.com/article/2244231/oracle-launches-worldwide-cloud-computing-tour.html. Retrieved 14 April 2020.
- ↑ Plesser, A. (29 September 2008). "Cloud Computing is Hyped and Overblown". YouTube. https://www.youtube.com/watch?v=f7wv1i8ubng. Retrieved 14 April 2020.
- ↑ Johnson, B. (29 September 2008). "Cloud computing is a trap, warns GNU founder Richard Stallman". The Guardian. https://www.theguardian.com/technology/2008/sep/29/cloud.computing.richard.stallman. Retrieved 14 April 2020.
- ↑ Maier, F. (19 October 2011). "Can There Ever Really Be Privacy in the Cloud?". Mashable. https://mashable.com/2011/10/19/cloud-privacy/. Retrieved 14 April 2020.
- ↑ Schwartz, P.M. (2013). "Information Privacy in the Cloud". University of Pennsylvania Law Review 161 (1623): 2290303. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2290303. Retrieved 14 April 2020.
- ↑ Howard, A.B. (18 December 2009). "FISMA compliance for federal cloud computing on the horizon in 2010". SearchCompliance. TechTarget. https://searchcompliance.techtarget.com/news/1377298/FISMA-compliance-for-federal-cloud-computing-on-the-horizon-in-2010. Retrieved 14 April 2020.
- ↑ Glotzbach, M. (15 September 2009). "Google Apps and Government". Google Official Enterprise Blog. Google. https://cloud.googleblog.com/2009/09/google-apps-and-government.html. Retrieved 14 April 2020.
- ↑ Bartels, Angela (5 March 2009). "Cloud Hosting is Secure for Take-off: Mosso Enables The Spreadsheet Store, an Online Merchant, to become PCI Compliant". Rackspace. Archived from the original on 23 February 2011. https://web.archive.org/web/20110223172816/http://www.rackspace.com/cloud/blog/2009/03/05/cloud-hosting-is-secure-for-take-off-mosso-enables-the-spreadsheet-store-an-online-merchant-to-become-pci-compliant/. Retrieved 21 August 2014.
- ↑ Brooks, C. (17 November 2009). "Amazon gets SAS 70 Type II audit stamp, but analysts not satisfied". SearchCloudComputing. TechTarget. https://searchcloudcomputing.techtarget.com/news/1374629/Amazon-gets-SAS-70-Type-II-audit-stamp-but-analysts-not-satisfied. Retrieved 14 April 2020.
- ↑ Norton, Jerry (31 December 2009). "Assessing Cloud Computing Agreements and Controls". WTN News. WTN Media. http://wtnnews.com/articles/6954/. Retrieved 21 August 2014.
- ↑ Helbing, T. (29 August 2012). "How the New EU Rules on Data Export Affect Companies in and Outside the EU". Dr. Thomas Helbing. https://www.thomashelbing.com/en/blog/how-new-eu-rules-data-export-affect-companies-and-outside-eu. Retrieved 14 April 2020.
- ↑ Richards, B. (17 June 2013). "Cloud Computing – Storm or Silver Lining? Pt 2". Trinus Technologies Inc. Archived from the original on 21 January 2015. https://web.archive.org/web/20150121005425/http://www.trinustech.com/cloud-computing-storm-or-silver-lining-pt-2/. Retrieved 14 April 2020.
- ↑ Jenks, Stephen (8 November 2011). "Cloud Computing for Home Has Huge Problems". Stephen Jenks' Blog. http://www.stephenjenks.com/2011/11/cloud-computing-for-home-has-huge-problems/. Retrieved 21 August 2014.
- ↑ "Cloud Computing Trademark Trends". Inside Trademarks. 24 March 2010. Archived from the original on 28 March 2010. https://web.archive.org/web/20100328121742/http://insidetrademarks.com/2010/03/24/cloud-computing-trademark-trends/. Retrieved 21 August 2014.
- ↑ "Google v US Complaint". Scribd. 31 October 2010. https://www.scribd.com/document/40513712/Google-v-US-Complaint. Retrieved 14 April 2020.
- ↑ Casson, T.; Ryan, P.S. (1 May 2006). "Open Standards, Open Source Adoption in the Public Sector, and Their Relationship to Microsoft’s Market Dominance". Social Science Electronic Publishing. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1656616. Retrieved 14 April 2020.
- ↑ Scheier, R.L (20 April 2009). "What to do if your cloud provider disappears". InfoWorld. IDG Network. https://www.infoworld.com/article/2634406/cloud-computing-what-to-do-if-your-cloud-provider-disappears.html. Retrieved 14 April 2020.
- ↑ "GoGrid Moves API Specification to Creative Commons". ServePath. 20 January 2009. Archived from the original on 01 February 2009. https://web.archive.org/web/20090201061221/http://gogrid.com/company/press-releases/gogrid-moves-api-specification-to-creativecommons.php. Retrieved 21 August 2014.
- ↑ Brockmeier, J. (19 February 2010). "Eucalyptus Completes Amazon Web Services Specs with Latest Release". OStatic. Archived from the original on 07 March 2012. https://web.archive.org/web/20120307062957/http://ostatic.com/blog/eucalyptus-completes-amazon-web-services-specs-with-latest-release. Retrieved 14 April 2020.
- ↑ 49.0 49.1 Zissis, D.; Lekkas, D. (2012). "Addressing cloud computing security issues". Future Generation Computer Systems 28 (3): 583–92. doi:10.1016/j.future.2010.12.006.
- ↑ Messmer, E. (22 February 2010). "Security of virtualization, cloud computing divides IT and security pros". Network World. https://www.networkworld.com/article/2244954/security-of-virtualization--cloud-computing-divides-it-and-security-pros.html. Retrieved 14 April 2020.
- ↑ Armbrust, M.; Fox, A.; Griffith, R. et al. (2010). "A view of cloud computing". Communications of the ACM 53 (4): 50–58. doi:10.1145/1721654.1721672.
- ↑ Anthes, G. (2010). "Security in the cloud". Communications of the ACM 53 (11): 16–18. doi:10.1145/1839676.1839683.
- ↑ Trappier, T. (24 June 2010). "If It's in the Cloud, Get It on Paper: Cloud Computing Contract Issues". EDUCAUSE. https://er.educause.edu/articles/2010/6/if-its-in-the-cloud-get-it-on-paper-cloud-computing-contract-issues. Retrieved 14 April 2020.